IT.Books Ransomware
The IT.Books Ransomware is an encryption ransomware Trojan, designed to make the victim's files inaccessible and then demand a ransom payment. The IT.Books Ransomware recycles code from two well-known ransomware threats: HiddenTear and Jigsaw. The IT.Books Ransomware represents an important threat to the victim's data, and this is why you need to take steps to ensure that your data is protected from this and similar threats.
Table of Contents
What Does the IT.Books Ransomware Do with Your Files
The IT.Books Ransomware targets the user-generated files, using a strong encryption algorithm to make the victim's files inaccessible. The IT.Books Ransomware marks the files it encrypts by its attack by adding the file extension 'fucked' to the end of each compromised file. We can mention a few examples of the files that the IT.Books Ransomware targets in these attacks:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
After the IT.Books Ransomware encrypts the victim's files, it delivers a ransom note in the form of a text file named 'READ_IT.txt' and in a program window. The criminals responsible for the Matrix-CHE08 Ransomware IT.Books Ransomware attack demand a ransom payment of 600 USD in exchange for the decryption key needed to restore the affected files. The Matrix-CHE08 Ransomware IT.Books Ransomware ransom note goes on to say that if the victim attempts to reboot the affected computer, the victim's files will be deleted permanently. The IT.Books Ransomware's ransom is demanded in Bitcoin.
Dealing with the IT.Books Ransomware
Unfortunately, just after the IT.Books Ransomware attack, it will not be possible to decrypt the files that it encrypted due to the strength of the encryption method used by the criminals responsible for the attack. It also is not advisable to contact the criminals to pay the ransom. It is very improbable that the malefactors will let the victims recover their files after the payment is carried out. Instead, computer users are advised to take steps to protect their files preemptively, to ensure that they can restore them even after they are compromised by a threat like the IT.Books Ransomware. It is obvious that the best protection against threats like the IT.Books Ransomware is to have file backups. The backup copies of your files will ensure that the criminals will not have any power over their victims since there is no point in paying these ransoms if the files can be recovered from a backup. In fact, if enough computer users have access to backup copies of their data, ransomware attacks like the IT.Books Ransomware would likely stop since they would no longer be profitable. Apart from file backups, computer users should use a security program that is fully up-to-date.
SpyHunter Detects & Remove IT.Books Ransomware
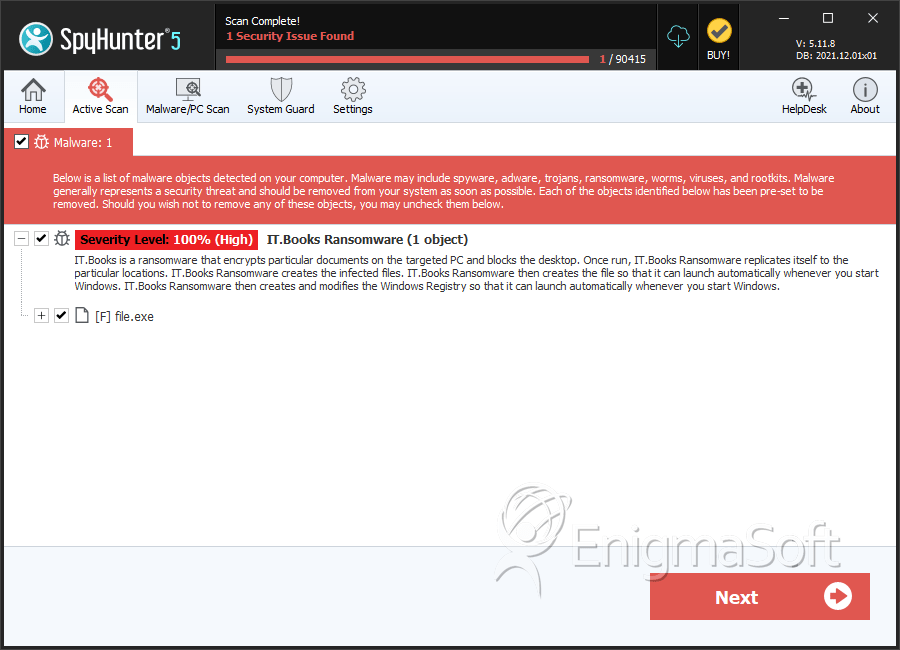
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 98a9d3fe8f64e5d34d143ed5a6b73eb0 | 0 |

