Gerkaman@aol.com Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 27 |
| First Seen: | September 1, 2016 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
The 'Gerkaman@aol.com' Ransomware is a infection that is part of a large family of ransomware Trojans known as Troldesh or Shade. The 'Gerkaman@aol.com' Ransomware and other Troldesh variants have been very active during the Summer of 2016, with numerous variants in this family being released every week. Troldesh variants like the 'Gerkaman@aol.com' Ransomware may be distinguished from Crysis variants, another family of threats that has been very active in the same period of time, by the fact that the 'Gerkaman@aol.com' Ransomware and other Troldesh variants change the affected files' extensions to '.xbtl' or '.ybtl' after the encryption process.
How the 'Gerkaman@aol.com' Ransomware Carries out Its Attack
The 'Gerkaman@aol.com' Ransomware attack is not too difficult to understand, since it is an attack that has been seen countless times before in a wide variety of ransomware Trojans. The following are the steps involved in a the 'Gerkaman@aol.com' Ransomware infection commonly (as well as with other ransomware Trojan attacks):
- The 'Gerkaman@aol.com' Ransomware may be delivered to the victim's computer through social engineering, direct hacking, or through the use of other threats. The most common method for delivering the 'Gerkaman@aol.com' Ransomware is by disguising the 'Gerkaman@aol.com' Ransomware as a harmless file that will be attached to an email message. These email messages may impersonate receipts or emails from shipping companies, prompting the victim to open the attached file. Due to all of this, you need to exercise care when dealing with any unsolicited email attachments.
- After the 'Gerkaman@aol.com' Ransomware has been installed, it connects to a Command and Control server, which is operated by the con artists responsible for this attack, and encrypts the victim's files using a sophisticated encryption algorithm. The 'Gerkaman@aol.com' Ransomware will store the decryption information on the server, making it inaccessible to the victim. During its attack, the 'Gerkaman@aol.com' Ransomware targets the files that will have value to the victim but avoids preventing Windows from functioning, since it requires that the operating system remains operational to deliver its ransom demand.
- At this point, the 'Gerkaman@aol.com' Ransomware has taken the victim's files hostage essentially. The 'Gerkaman@aol.com' Ransomware demands the payment of a ransom through some anonymous payment method by dropping ransom notes on the victim's computer and changing the victim's Desktop image into a copy of the ransom note.
The following are the types of files that are targeted in attacks related to Troldesh variants like the 'Gerkaman@aol.com' Ransomware:
.odc, .odm, .odp, .ods, .odt, .docm, .docx, .doc, .odb, .mp4, sql, .7z, .m4a, .rar, .wma, .gdb, .tax, .pkpass, .bc6, .bc7, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps.
PC security analysts strongly advise computer users against paying the 'Gerkaman@aol.com' Ransomware ransom. Instead, the 'Gerkaman@aol.com' Ransomware should be removed, and steps should be taken to restore the affected files from an off-site backup (an important preventive method that will make computer users immune to these kinds of attacks).
SpyHunter Detects & Remove Gerkaman@aol.com Ransomware
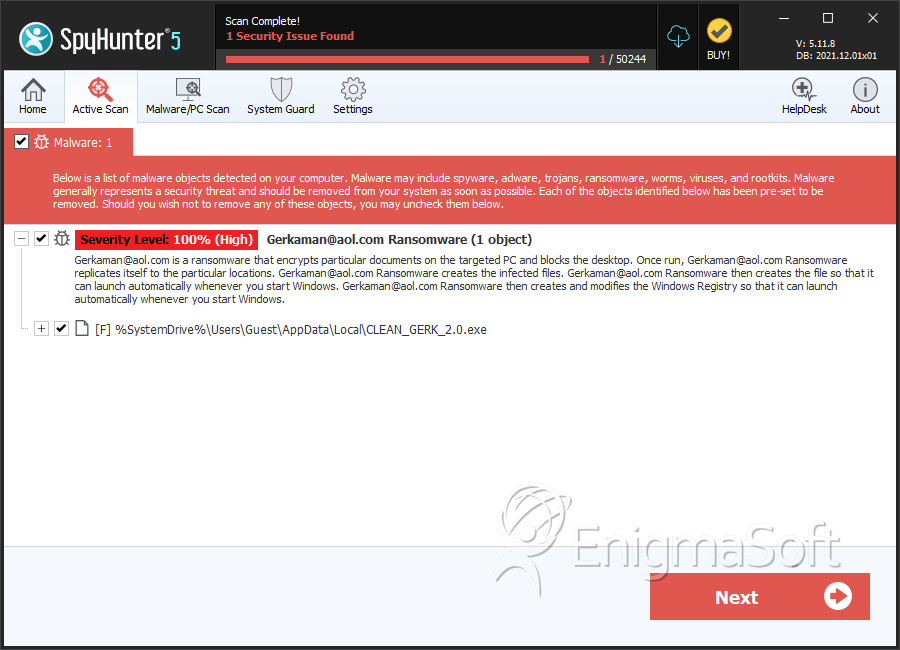
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | CLEAN_GERK_2.0.exe | 56d7fdc09e6edc3701b179bcffc33277 | 25 |
