Gedantar Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | April 4, 2018 |
| Last Seen: | April 18, 2018 |
| OS(es) Affected: | Windows |
The Gedantar Ransomware is an encryption ransomware Trojan. Once the Gedantar Ransomware infects a computer, it will run as an executable file named 'Gedantar.exe.' PC security researchers received the first reports of the Gedantar Ransomware infections on March 28, 2018. It seems that the Gedantar Ransomware is designed to target computer users in Russian-speaking locations because it delivers a ransom note written in Russian to the victim's computer. The Gedantar Ransomware is a variant of Unlock92, a ransomware family that includes several threats. The Gedantar Ransomware is the fourth version in this family of threats.
Table of Contents
How the Gedantar Ransomware Carries out Its Attack
The most common way in which the Gedantar Ransomware enters a computer is through spam email messages. Victims will receive a spam email message containing an attached document with enabled macro scripts. The Gedantar Ransomware will be downloaded and installed on the victim's computer by these macros. Once the Gedantar Ransomware is installed, it will use a strong encryption algorithm to encrypt the victim's files, making them inaccessible. The Gedantar Ransomware will mark the files encrypted by the attack by adding a string of eight random characters after the file's original name but preserving the original file extension. However, the Gedantar Ransomware will make the affected files to become inaccessible, and their contents will be locked away. Some samples of the files that are commonly targeted in attacks like the Gedantar Ransomware include:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
The Gedantar Ransomware’s Ransom Demand
The Gedantar Ransomware will deliver a ransom note in the form of a JPG image that will be delivered as a JPG file with a name composed of 20 random characters. The image consists of a white screen with black text and red hyperlinks. The text of the Gedantar Ransomware ransom note, written entirely in Russian, reads:
'Ваши файлы были зашифрованы с помощью алгоритма а5А-2048 Если вы хотите их вернуть то отправьте один из зашифрованных файлов на е-mail: unlckr@protonmail.com
Если вы не получили ответ в течение суток то скачайте с сайта www.torproject.com браузер ТО и с его помощью зайдите на сайт h[tt]p://n3r2kuzhw2h7x6j5[.]onion -там будет указан действующий V почтовый ящик.
Попытки самостоятельного восстановления файлов могут безвозвратно их испортить!'
An English translation of the Gedantar Ransomware ransom note:
'Your files were encrypted using the a5A-2048 algorithm. If you want to return them, send one of the encrypted files to an e-mail: unlckr@protonmail.com
If you did not receive a reply within 24 hours then download the TO browser from the site www.torproject.com and use it to go to the site h[tt]p://n3r2kuzhw2h7x6j5[.]onion -the current V mailbox will be indicated.
Attempts to repair files yourself can irrevocably ruin them!'
The email address used by the people associated with the Gedantar Ransomware has been observed in previous versions in this ransomware family.
Dealing with the Gedantar Ransomware
Unfortunately, once the Gedantar Ransomware has compromised the files, they will not be recoverable without the decryption key. Because of this, PC security researchers advise using a security program that is fully up-to-date and handling spam email with caution, to prevent the Gedantar Ransomware from being installed in the first place. Computer users should use backup copies of their files to restore any files encrypted by the Gedantar Ransomware attack.
SpyHunter Detects & Remove Gedantar Ransomware
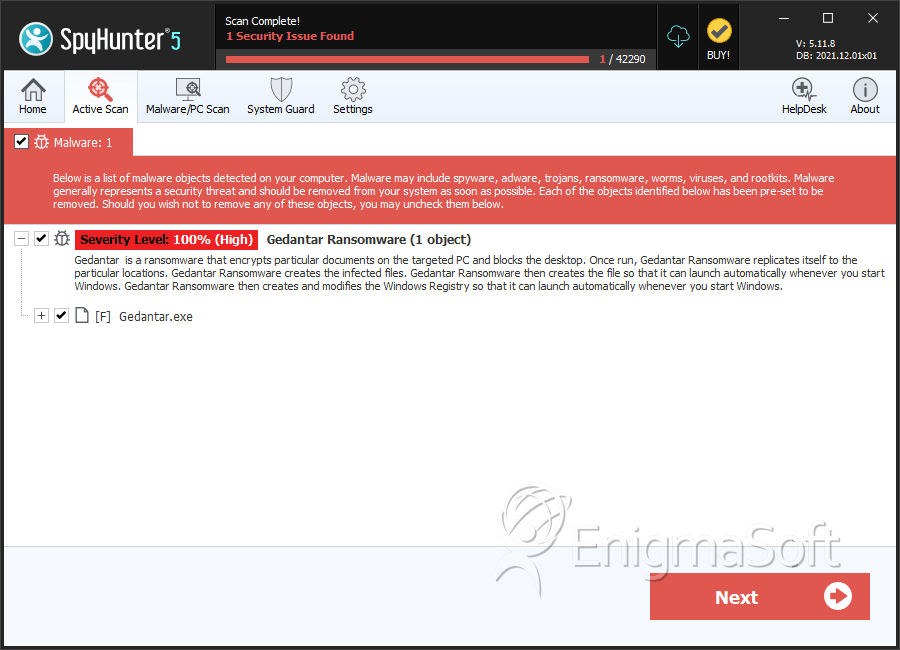
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Gedantar.exe | 8afcb6e9b45c234bbb5982f382396049 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.