GarrantyDecrypt Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 11 |
| First Seen: | October 14, 2018 |
| Last Seen: | July 23, 2019 |
| OS(es) Affected: | Windows |
GarrantyDecrypt Ransomware Image
The GarrantyDecrypt Ransomware is an encryption ransomware Trojan. The GarrantyDecrypt Ransomware was first reported on October 10, 2018. The GarrantyDecrypt Ransomware is being distributed to its victims through the use of spam email attachments. The victims will often receive a Microsoft Word file with embedded macros that, when opened, installs the GarrantyDecrypt Ransomware on the targeted computer. Once installed, the GarrantyDecrypt Ransomware is designed to take the victim's files hostage, demanding a ransom payment afterward.
Table of Contents
Should you Trust the Promise on the GarrantyDecrypt Ransomware’s Name?
The GarrantyDecrypt Ransomware targets the user-generated files, which may include numerous documents such as videos, audio, texts, and other file types. Examples of the data that threats like the GarrantyDecrypt Ransomware will target in attacks such as these include:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
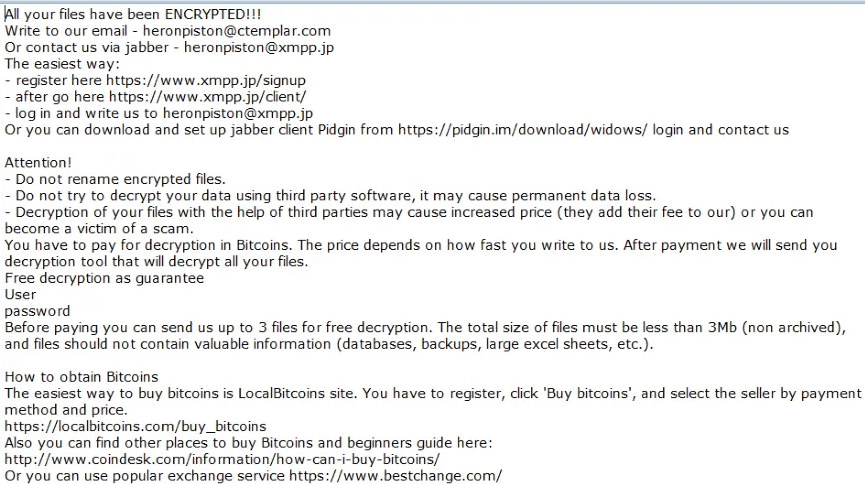
The GarrantyDecrypt Ransomware will use a strong encryption algorithm in its attack to make the victim's files inaccessible. The GarrantyDecrypt Ransomware will rename the files by adding the file extension '.garrantydecrypt' to their names after the files have been taken hostage. The GarrantyDecrypt Ransomware delivers its ransom note in the form of a text file named '#RECOVERY_FILES#.txt' that is dropped on the infected computer's desktop. The following is the full text of the GarrantyDecrypt Ransomware ransom note:
'All your files have been ENCRYPTED
Do you really want to restore your files?
Write to our email - garrantydecrypt@airmail.cc
and tell us your unique ID
[random characters]'
Threat researchers strongly advise computer users to refrain from paying the GarrantyDecrypt Ransomware ransom or contacting the criminals responsible for this attack. Doing this just allows the criminals to continue creating and distributing threats such as this one.
Protecting Your Data from Threats Like the GarrantyDecrypt Ransomware
Unfortunately, the GarrantyDecrypt Ransomware and similar threats use an encryption method that is quite strong, and it is impossible to restore the files compromised by the attacks currently. Because of the many problems a ransomware infection can cause, computer users should take steps to protect their data preemptively. The best protection computer users can have, should include an updated security program and backup copies of all data. Having backup copies of your data ensures that, in the event of an attack, the data can be recovered without having to contact the criminals or spend money.
Update December 28th, 2018 — Nostro Ransomware
The Nostro Ransomware is the second major release to the GarrantyDecrypt line of encryption Trojans. The original threat emerged on October 10th, 2018 with the new release coming out on December 28th, 2018. The Nostro Ransomware uses a new ransom note, a new file extension, a new email, and slightly altered encryption technologies. The Nostro Ransomware is classified as another run-of-the-mill crypto-threat that eliminates the Shadow Volume snapshots in Windows, overwrites targeted data and removes the System Restore points to prevent easy recovery. The Nostro Ransomware is known to scan the local and removable drives currently attached to the PC and encode standard data containers. Microsoft Word files, presentations, PDFs, eBooks, databases, audio, and video materials are made inaccessible, but you can still copy/paste, move and delete them. The files receive the '.NOSTRO' suffix and something like 'Sabathon-Inmate 4859.acc' is renamed to 'Sabathon-Inmate 4859.acc.NOSTRO.' The new ransom note retains the name '#RECOVERY_FILES#.txt' and can be found on the user's desktop. However, it has an entirely new message and email account:
'CONGRATULATIONS!
All your files have been encrypted!
Now you should send us email with your personal identifier.
This email will be as confirmation you are ready to pay for decryption key.
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
Contact us using this email address
nostro19@protonmail.com
And tell us your unique ID
[random characters]'
Computer security experts that are working with ransomware samples are pessimistic that a free decryptor can be made for the victims of the Nostro Ransomware. The malware does not include a hardcoded decryption key, it does not keep any information on the infected host, and it self-destructs after your data has been encrypted successfully. Do not contact the 'nostro19@protonmail.com' and attempt to negotiate a favorable price. The threat authors may attempt to profile you and give you an absurd price for your data if they suspect you have lost access to important files. Use a respected anti-malware service to remove the Nostro Ransomware and make sure you have a portable memory disk to store your backups.
SpyHunter Detects & Remove GarrantyDecrypt Ransomware
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 7b16fbd06e3442bc9055208abd8f1ef3 | 0 |

