FenixLocker Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | September 19, 2016 |
| Last Seen: | July 23, 2019 |
| OS(es) Affected: | Windows |
The FenixLocker Ransomware is a ransomware threat that was discovered in September of 2016 and almost defeated very quickly, as the FenixLocker Ransomware decryption utility was released almost immediately after this threat was discovered. The FenixLocker Ransomware uses the AES encryption to encrypt the victim's files. The FenixLocker Ransomware will then add the extension '.centrumfr@india.com!!' to each file it encrypts. The FenixLocker Ransomware drops ransom notes named 'Cryptolocker.txt' or 'Help to decrypt.txt' that simply say:
All of your files are encrypted, to decrypt them write me to email: centrumfr@india.com
Your key:
[redacted]
The FenixLocker Ransomware has been referred to by its @india.com email address as well. However, some PC security researchers have taken to calling the FenixLocker Ransomware with this other name because of a string in the FenixLocker Ransomware's code that seems to be a love message from the threat creators to someone named 'Fenix.' Fortunately, a FenixLocker Ransomware decryptor is available and easy to use currently. Simply drag one of the encrypted files onto the decryptor and it will provide you with the password or decryption key that you would need to decrypt all the other files affected by the FenixLocker Ransomware attack.
Table of Contents
A Brief Description of the FenixLocker Ransomware Attack
The FenixLocker Ransomware attack is simple to understand. The FenixLocker Ransomware will enter a computer using covert methods, encrypt the victim's files, and then display a ransom note alerting the victim of the attack and asking for payment to restore the encrypted files. The FenixLocker Ransomware drops ransom notes in directories that contain encrypted files, as well as on the affected computer's Desktop. Although the FenixLocker Ransomware references CryptoLocker in its ransomware note (a well-known ransomware Trojan that has been responsible for countless attacks), there is no relationship between the FenixLocker Ransomware and Cryptolocker. This may simply be a misleading tactic or a way to increase the FenixLocker Ransomware's profile in the eyes of the victim.
The most common way in which the FenixLocker Ransomware is delivered to its victims' computers is through corrupted email messages. Email messages containing a social engineering tactic (such as a fake invoice or receipt) will land on the victims' inboxes. These email messages will be crafted with the intention of tricking computer users into opening the attached file. When the PC user opens the attached file, the FenixLocker Ransomware will begin running in the background, encrypting the victim's files and communicating with its Command and Control server. The FenixLocker Ransomware also will make changes to the affected computer's settings to ensure that the FenixLocker Ransomware runs automatically when Windows starts up.
Preventing the FenixLocker Ransomware Attacks
Although it is possible to recover thanks to the availability of a free decryption utility in the case of the FenixLocker Ransomware, this may not happen with most ransomware Trojans. In fact, after a ransomware attack, victims rarely have any option to recover their files, since paying the ransom for these attacks is highly discouraged by PC security analysts. Because of this, it is necessary to take preventive measures to ensure that you do not become a victim of ransomware Trojans more threatening than the FenixLocker Ransomware. The following are some steps you should take to make you invulnerable to these kinds of attacks:
- The single most important step you can take to stop the FenixLocker Ransomware and other ransomware Trojans preemptively is to backup all of your files. Having good backups that are regularly updated on an external memory device or the cloud means that con artists can no longer threaten you with withholding your files. You can simply recover your files by restoring them from the backup after deleting the FenixLocker Ransomware infection.
- Use a reliable security program that is fully up-to-date to intercept threats like the FenixLocker Ransomware before they initiate their attacks.
- Exercise caution when dealing with any email attachment, since this is the most common distribution method for ransomware Trojans.
SpyHunter Detects & Remove FenixLocker Ransomware
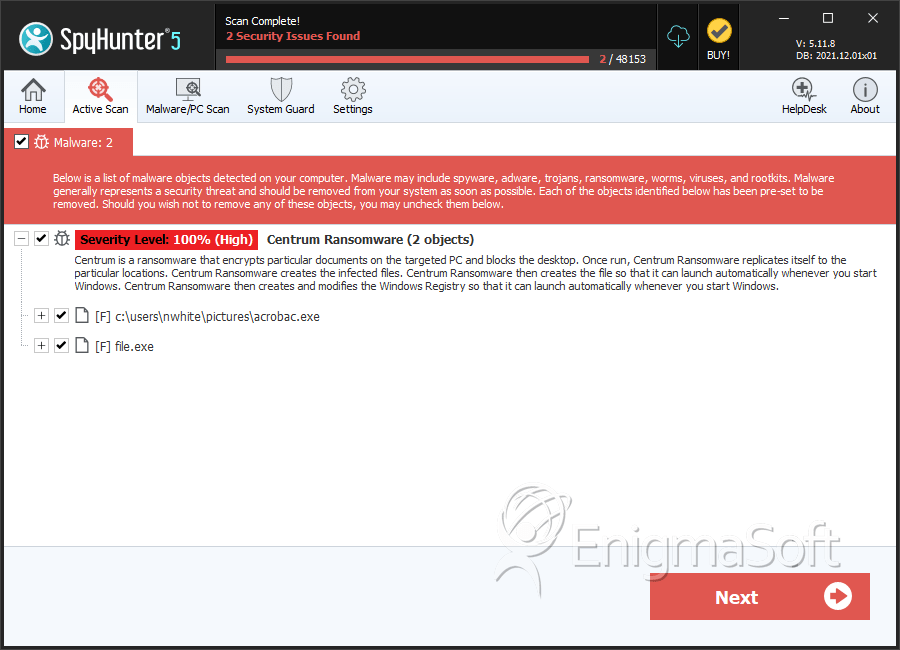
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | acrobac.exe | ebcbe216ab4c5281026c39e8e489ea93 | 1 |
| 2. | file.exe | de1c76810f1b55a169bedd84033816ff | 1 |
| 3. | file.exe | 2e6031a3acd6905b97c5ed88a60bfac4 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.