FCrypt Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 3 |
| First Seen: | February 14, 2019 |
| Last Seen: | October 1, 2020 |
| OS(es) Affected: | Windows |
The FCrypt Ransomware is an encryption ransomware Trojan first observed by malware analysts on February 9, 2019. It seems that the FCrypt Ransomware is still in development. However, the FCrypt Ransomware is capable of carrying out an effective encryption ransomware attack, making the victim's files useless and then demanding a ransom payment in exchange for restoring access to the affected data. Threats like the FCrypt Ransomware are commonly delivered to the victims via spam email attachments, and computer users are advised to be careful when handling this content.
Table of Contents
How the FCrypt Ransomware Attack Works
The FCrypt Ransomware is similar to most encryption ransomware Trojans; it uses a strong encryption algorithm to take the victim's files' hostage. The FCrypt Ransomware changes the victims' files icons and adds the file extension '.Fcrypt' to each file it encrypts in its attack. The FCrypt Ransomware targets the user-generated files, which may include a wide variety of file types, such as media files, documents and databases. The files targeted by threats like the FCrypt Ransomware include:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
The FCrypt Ransomware delivers a ransom note in a text file named '#HELP-DECRYPT-FCRYPT1.1#.txt,' which contains the following message for the victims of the FCrypt Ransomware attack, once their files have been made inaccessible:
'FCRYPT V1.1
Warning!
All your important files are encrypted and have extension: .FCrypt
No one else can decrypt your file!
Please follow the steps below:
1. Send this file (#HELP-DECRYPT-FCRYPT1.1#.txt) to E-mail : fcrypt@qq.com
2. Uninstall all anti-virus software on your computer.
3. Waiting for reply.
You DON'T need to pay any money for decryption.
Note!
IN ORDER TO PREVENT DATA DAMAGE:
# DO NOT MODY ENCRYPTED FILES
# DO NOT CHANGE DATA BELOW
--BEGIN CERTIFICATE--
[random characters]
--END CERTIFICATE--'
Dealing with a FCrypt Ransomware Infection
Paying the FCrypt Ransomware ransom or contacting the criminals responsible for the FCrypt Ransomware attack is not recommended by the experts. Instead of paying the FCrypt Ransomware ransom, computer users should find safe ways to remove the FCrypt Ransomware and restore any data compromised by the attack, such as copying it from a backup copy. This is what makes the best protection against threats like the FCrypt Ransomware to have backup copies of all data, and store these backup copies on independent devices. Unfortunately, once the FCrypt Ransomware has encrypted the files, they will no longer be recoverable. However, by using a security application, the victims can remove the FCrypt Ransomware and even prevent it from carrying out its attack, although they will not be capable of restoring any data that has been compromised in the FCrypt Ransomware attack itself.
SpyHunter Detects & Remove FCrypt Ransomware
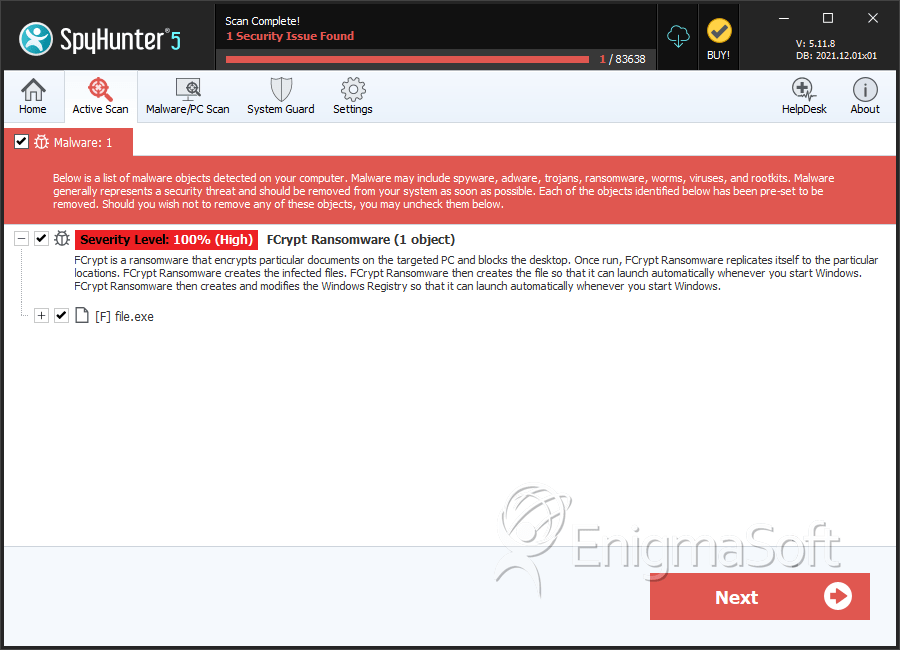
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 40e28f4ec185eae27a78c6ba005cedc0 | 1 |
| 2. | file.exe | ada50b802b8b2e3ef1dc496ec2d5eaf7 | 1 |

