Extractor Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 9 |
| First Seen: | May 3, 2017 |
| Last Seen: | July 23, 2019 |
| OS(es) Affected: | Windows |
The Extractor Ransomware was first observed in May 2017. The Extractor Ransomware will infect all version of the Windows operating system, going back to Windows Vista. The Extractor Ransomware carries out a typical ransomware attack, encrypting the victims' files and then asking for the payment of a ransom from the victim in exchange for the decryption key necessary to recover from the attack. The most probable way in which the Extractor Ransomware is being distributed is through spam emails. These emails will include corrupted attachments or links leading to attack websites, where the Extractor Ransomware is installed on the victim's computer. Judging the Extractor Ransomware ransom note, the Extractor Ransomware seems to target English speakers, although the Extractor Ransomware infections can appear anywhere in the world. Currently, it seems that the Extractor Ransomware distribution is limited, although it is not unlikely that its numbers will grow over time. PC security analysts advise PC users to take preventive measures to ensure that their computers are well-protected from the Extractor Ransomware. In its attack, the Extractor Ransomware is nearly identical to numerous other ransomware Trojans released in Spring, 2017.
Table of Contents
The Extractor Ransomware will Try to Extract Your Money
The Extractor Ransomware uses a combination of the AES and RSA encryptions to make the victim's files inaccessible. This is an approach that is used by most current ransomware threats. In its attack, the Extractor Ransomware is designed to prevent computer users from accessing their files. The Extractor Ransomware does not use intensive system resources, which allows it run in the background. The Extractor Ransomware also is designed to bypass many security programs, remaining undetected until the victim's files have been encrypted. Additionally, the Extractor Ransomware is written using Delphi, which gives it good integration with the Windows operating system, making its attack more effective. The Extractor Ransomware will use the executable file 'ip topoloji.exe.'
How the Extractor Ransomware Carries out It’s Infection
The Extractor Ransomware will target files generated by the user. This includes audio, video, text, spreadsheet, and other types of files. The Extractor Ransomware also will target files generated by other software such as Libre Office, Adobe Photoshop, and AutoCAD (among many others). The Extractor Ransomware will mark files that have been encrypted with the file extension '.xxx,' making it easy trecognize which files have been compromised in the Extractor Ransomware attack. After encrypting the victim's files, the Extractor Ransomware will deliver a ransom note named 'ReadMe_XXX.txt,' dropped on the infected computer's Desktop. This file, which will be opened by the default text editor (usually a Microsoft Notepad), will contain the following text:
'Hello,
I crypted all your important data
I stored the crypted data in your hard disk.
If you want to become your data back, send me an email containing your computer Number.
Your computer Number: [RANDOM NUMBER]
e-mail : serverrecovery@mail.ru'
Recovering from an Extractor Ransomware Infection
Computer users may be tempted to pay the Extractor Ransomware ransom to recover from the attack. However, malware researchers strongly advise computer users to refrain from making these payments. Apart from the fact that they seldom work, and extortionists will frequently ignore the payment or simply ask for more money, making these payments also finances the creation and development of more ransomware Trojans like the Extractor Ransomware. Instead of doing this, take preventive measures to ensure that your computer is well protected from the Extractor Ransomware and similar threats. The Extractor Ransomware infections can be avoided by using a reliable security program that is fully up to date and learning how to manage email safely. However, the best way to ensure that the Extractor Ransomware and similar threats can leave no lasting damage is to have good backups of all files on an external memory device or the cloud. Having the ability to recover the affected files from a backup copy completely undermines the Extractor Ransomware attack.
SpyHunter Detects & Remove Extractor Ransomware
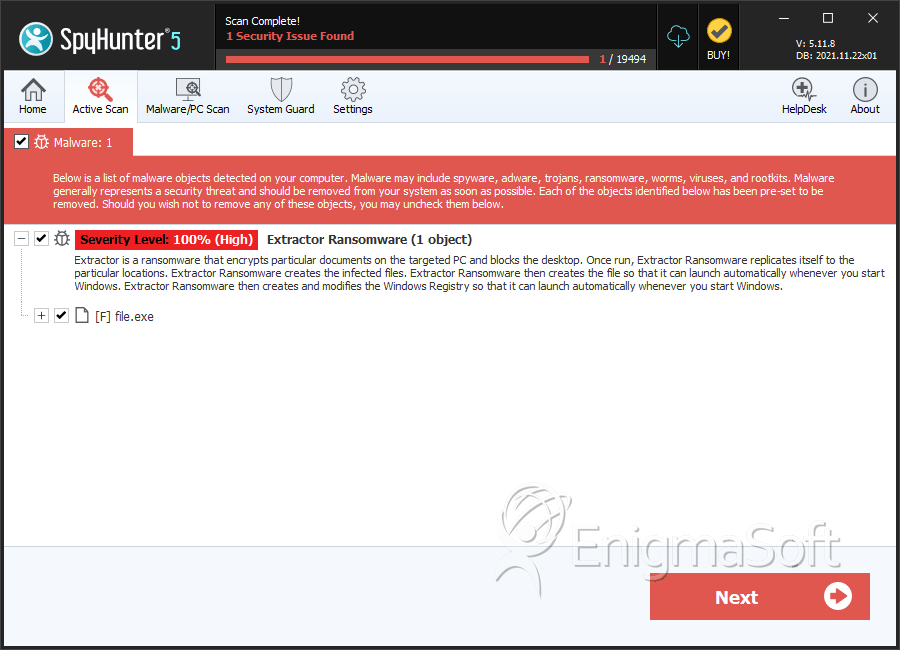
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | db8f3a38ec2bbf12700f19d5c7b1adbe | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.