Enigma Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 3,349 |
| First Seen: | May 11, 2016 |
| Last Seen: | November 24, 2021 |
| OS(es) Affected: | Windows |
The Enigma Ransomware is a ransomware Trojan that is designed to attack computer users located in Russian-speaking countries. The Enigma Ransomware was first observed in late April of 2016. The Enigma Ransomware encrypts the victim's data using an AES encryption algorithm and then demands the payment of 0.4291 BitCoin, which is about $200 USD in exchange for the decryption key. This is a common approach linked to most ransomware Trojans. What makes the Enigma Ransomware unique is that its ransom note and attack are in Russian and seem to target specific countries where this language is spoken. The Enigma Ransomware also uses an installer based on HTML and JavaSCript, which contains a corrupted executable file that is embedded inside. Some versions of the Enigma Ransomware are unsuccessful in deleting Shadow Volume Copies of encrypted files, giving computer users the possibility of recording their files through that method.
Table of Contents
The Enigma that can be Solved with Money
The Enigma Ransomware may be distributed using a compromised JavaScript installer that contains an embedded executable file. The Enigma Ransomware may be distributed through HTML malicious attachments that launch the victim's Web browser so that it will execute this threatening JavaScript, which in turn delivers the corrupted executable code. The JavaScript will create a file with a Russian name: Свидетельство о регистрации частного предприятия.js, which translation means 'The certificate of registration of private predpriyatiya.js.' After creating this file, the HTML file will download it and claim that the victim should execute it. When executed, this JavaScript creates an executable file called 3b788cd6389faa6a3d14c17153f5ce86.exe, which is executed automatically. This executable file encrypts the files on the victim's computer, changing their extension to '.the Enigma' and delivers a ransom note to the victim. The ransom note instructs the victim on how to pay using TOR and informs the victims about what has happened to their files. The text of the Enigma Ransomware ransom note in the original Russian reads as follows:
Мы зашифровали важные файлы на вашем компьютере: документы, базы данных, фото, видео, ключи.
Файлы зашифрованны алгоритмом AES 128(https://ru.wikipedia.org/wiki/Advanced_Encryption_Standard) с приватным ключем,который знаем только мы.
Зашифрованные файлы имеют расширение .the Enigma . Расшифровать файлы без приватного ключа НЕВОЗМОЖНО.
Если хотите получить файлы обратно:
1)Установите Tor Browser https://www.torproject.org/
2)Найдите на рабочем столе ключ для доступа на сайт the Enigma_(номер вашего ключа).RSA
3)Перейдите на сайт http://f6lohswy737xq34e.onion в тор-браузере и авторизуйтесь с помощью the Enigma_(номер вашего ключа).RSA
4)Следуйте инструкциям на сайте и скачайте дешифратор
Если основной сайт будет недоступен попробуйте http://ohj63tmbsod42v3d.onion/
Which can be translated as:
We encrypt sensitive files on your computer: documents, databases, photos, videos and keys.
Files encryption algorithm AES 128 (https://ru.wikipedia.org/wiki/Advanced_Encryption_Standard) with a private key that only we know.
Encrypted files have .the Enigma extension. It decrypts files without the private key IMPOSSIBLE.
If you want to get the files back:
1) Install the Tor Browser https://www.torproject.org/
2) Locate the desktop key to access the site the Enigma_ (your room key) .RSA
3) Go to the website http: //f6lohswy737xq34e.onion into a torus-browser and log in using the Enigma_ (your room key) .RSA
4) Follow the instructions on the website and download the decoder
If the primary site is unavailable, try http: //ohj63tmbsod42v3d.onion/
Paying the Enigma Ransomware Ransom
Computer users are advised against paying the Enigma Ransomware ransom. The best method for preventing and dealing with the Enigma Ransomware attacks is to backup all files on an external drive. This way, these files can be recovered from the backup after they have been encrypted. When computer users connect to the Enigma Ransomware payment site, they will be presented with the amount of BitCoins that must be paid as a ransom, as well as the additional payment information. Victims will be allowed to decrypt one file for free as proof that the con artists do hold the decryption key. The payment site also includes a chat box where threat developers can communicate directly with the victim.
SpyHunter Detects & Remove Enigma Ransomware
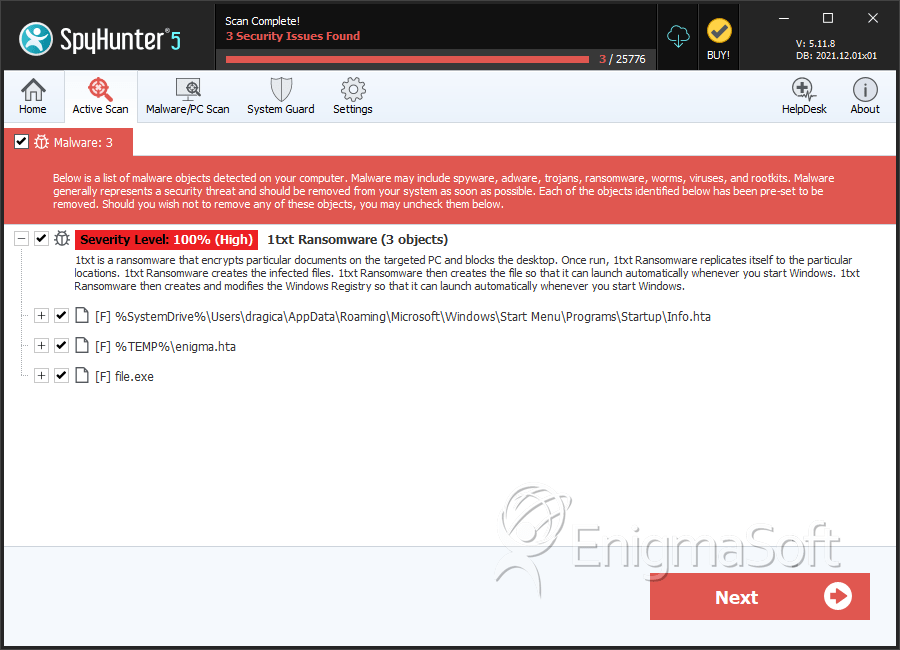
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Info.hta | 8abb764072580caad67085ef2c4fb4a9 | 1,437 |
| 2. | Info.hta | 3647f1ac41fdcf3d7474f8e033c03806 | 316 |
| 3. | Info.hta | 07a76a8680b8808be73cd7022281c8bb | 304 |
| 4. | Info.hta | e585f947d71d447687511180879d7a51 | 300 |
| 5. | enigma.hta | 83fe6340c1ba2df0763ff586ea0f078e | 162 |
| 6. | Info.hta | 98fd00612916c2e33a642ba205e34a7b | 132 |
| 7. | Info.hta | 0b9fde0b4c2c9f830140055fb38d800b | 131 |
| 8. | Info.hta | 9831132083f2ee030af1d98b9c14f154 | 105 |
| 9. | Info.hta | 5ab602dabd31d41dcc73f8aa6d03e93f | 82 |
| 10. | Info.hta | 1056d034a70bf36662e7c650109b90ba | 63 |
| 11. | Info.hta | 242857b841c36464078f93af40399c57 | 63 |
| 12. | Info.hta | e489ebda293c48de8ee210e92fe95292 | 35 |
| 13. | Info.hta | 83dcb8080a188b89a888a40f1fcd6a4b | 33 |
| 14. | Info.hta | 274a1fa63544f08eb916a3cc47b3e7a4 | 29 |
| 15. | Info.hta | 62c420c70071c316b61a920f3db27752 | 23 |
| 16. | Info.hta | f66247bf5c7f9ad62b5368ed5313805b | 21 |
| 17. | enigma.hta | 49834055020adf056f86bd6b786bc698 | 19 |
| 18. | Info.hta | 71132bd628fc3b1cf3eac606730f3d4a | 17 |
| 19. | enigma.hta | cafe36615aaff4c3ef741567c1c3a567 | 12 |
| 20. | Info.hta | 6db61e8081ea89a3a8eade528252e4a2 | 9 |
| 21. | Info.hta | 32d637476a64a2e440d1269185f3e673 | 8 |
| 22. | Info.hta | 9a8f9782336bd1a4c1877c190badee78 | 8 |
| 23. | enigma.hta | a69798cb9a41ea7fe7833d90a55c6c70 | 6 |
| 24. | enigma.hta | e3e8e2139749fcce0bf00cb16df8ead3 | 5 |
| 25. | enigma.hta | 0d69dee6cfc97dd423eec213ab650795 | 5 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.