Dont_Worry Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | April 11, 2018 |
| OS(es) Affected: | Windows |
The Dont_Worry Ransomware is an encryption ransomware Trojan that seems to attack Russian-speakers. The Dont_Worry Ransomware was released on April 1st, 2018, and seems to be a variant of a ransomware family that includes AMBA and the CryptoLab Ransomware. The Dont_Worry Ransomware is the third variant in this threat family to have been released at the date of writing. The Dont_Worry Ransomware and its variants all use the same ransom note, with slight differences tin the contact information and the marks used to identify the encrypted files.
Table of Contents
What are the Consequences of a Dont_Worry Ransomware Infection
The Dont_Worry Ransomware will target the user-generated files, which may include images, videos, texts, databases and music. The Dont_Worry Ransomware will mark the files encrypted by the attack with the file extension '.wog@onionmail.info-.' The Dont_Worry Ransomware will make the files it encrypts show up as blank icons since Windows or the victim’s applications will not recognize them. The following are examples of the types of files that are targeted in attacks like the Dont_Worry Ransomware:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
Attacks like the Dont_Worry Ransomware tend to avoid the Windows system files or executable files since they depend on the victim still being able to use Windows and their Web browsers to carry out the payments.
The Dont_Worry Ransomware’s Ransom Note
The different threats in the Dont_Worry Ransomware's family use the same ransom notes with different names. The Dont_Worry Ransomware delivers its ransom note in a text file named 'Dont_Worry.txt' that is dropped in various locations on the infected computer, including the Startup folder. The text for the Dont_Worry Ransomware's ransom note reads as follows:
'Вся Ваша информация на этом компьютере была зашифрована.
Для расшифровки обратитесь по нижеуказанным контактам.
------------------------------------------------------------
e-mail: wog@onionmail.info
Ваш код для разблокировки: [RANDOM NUMBER]
-----------------------------------
Если Вам приходит ответ, что почтовый адрес не существует:
1. Вам не повезло. Адрес заблокировали.
---------
Все инструкции вы получите в ответном письме.'
Below is a translation into English of the Dont_Worry Ransomware's ransom note:
'All your information on this computer has been encrypted.
To decrypt refer to the contacts listed below.
------------------------------------------------------------
e-mail: wog@onionmail.info
Your code for unlocking: [RANDOM NUMBER]
-----------------------------------
If you receive an answer that the mailing address does not exist:
1. You are unlucky. The address was blocked.
---------
You will receive all instructions in the reply letter.'
Protecting Your Data from the Dont_Worry Ransomware
Ransomware Trojans like the Dont_Worry Ransomware can be removed with the help of a malware removal program that is fully up-to-date. However, the files encrypted by the attack will not be recoverable without the decryption key, which the cybercrooks hold in their possession. Malware researchers, as always, are against payments to these threats, though, since it is very unlikely that the cybercrooks will help victims recover their files. Instead, computer users should use backup copies of their files to restore any data lost in the attack. In fact, having backup copies of your files on secured places is the single most effective measure that computer users can take to ensure that their data is safe from threats like the Dont_Worry Ransomware, which rely on taking the victims' data hostage through the use of encryption algorithms.
SpyHunter Detects & Remove Dont_Worry Ransomware
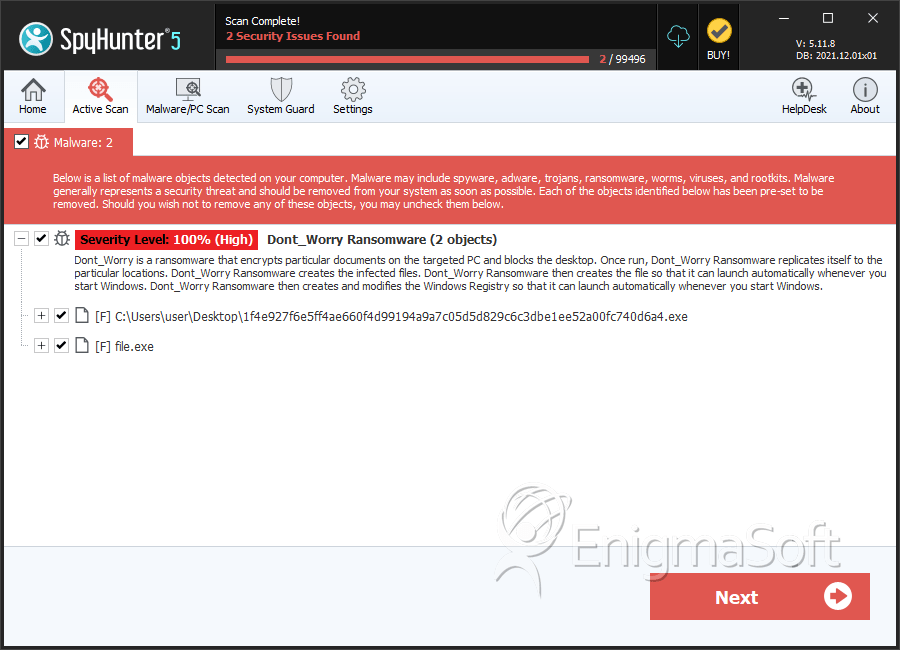
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 1f4e927f6e5ff4ae660f4d99194a9a7c05d5d829c6c3dbe1ee52a00fc740d6a4.exe | f5f2f6c370db4b38bdf8032ea3ef2a64 | 1 |
| 2. | file.exe | 81a3ea6e7019e3c4d12d5f1353166385 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.