AMBA Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
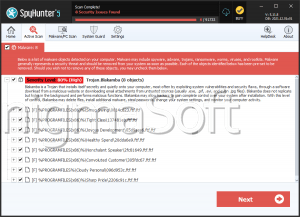
| Threat Level: | 80 % (High) |
| Infected Computers: | 23 |
| First Seen: | June 30, 2016 |
| Last Seen: | May 11, 2020 |
| OS(es) Affected: | Windows |
The AMBA Ransomware is an encryption ransomware threat that is designed to target websites in the Russian server. The AMBA Ransomware has been used in attacks against Web servers rather than against individuals as with most encryption ransomware Trojans. However, the type of attack in the case of the AMBA Ransomware is still the same as with other similar threats. After the AMBA Ransomware enters a Web server, the AMBA Ransomware encrypts all files it finds that match a list of file extensions contained in its configuration files. Whenever the AMBA Ransomware encrypts a file, it adds the extension '.the AMBA' to identify those files that have been encrypted. Apart from encrypting the victims' files, the AMBA Ransomware creates a text file named 'ПРОЧТИ_МЕНЯ.txt' which contains a ransom note written in Russian. The AMBA Ransomware's ransom note asks the victim to contact its perpetrators at a specific email address to obtain assistance with decrypting the files. Essentially, the AMBA Ransomware takes the victim's files hostage and demands the payment of a large ransom to return access to the encrypted files.
How the AMBA Ransomware Attacks a Computer User
According to the AMBA Ransomware's directions, the victim is instructed to contact the AMBA Ransomware's developers to receive instructions on how to decrypt this threat. Victims of the AMBA Ransomware are warned not to attempt to restore the files, or they risk losing access to their files permanently (this is a common threat associated with these kinds of infections). When victims contact the people responsible for the AMBA Ransomware, the reply will claim that it is necessary to pay a large ransom to obtain the decryption key. Most ransomware demand ransoms between 0.5 and 1.5 BitCoin (between $400 and $1000 USD on average). Currently, it seems that the con artists responsible for the AMBA Ransomware attack vary their ransom depending on the victim's situation. The reason why the ransom for the AMBA Ransomware is paid in BitCoins is that this payment method allows the con artists to remain anonymous. Computer users should avoid paying the AMBA Ransomware's ransom. In most cases, the con artists will ignore the victims and will not provide the decryption key after the payment is made. Even if they were to keep their promise, paying the AMBA Ransomware ransom enables them to continue creating and distributing these threats.
Unfortunately, it may not be possible to recover files encrypted by the AMBA Ransomware without access to the decryption key currently Because of this, the best method is to recover the affected files from a backup. It is, of course, strongly recommended to use a reliable security program that is fully up-to-date to prevent the AMBA Ransomware from entering a computer in the first place.
The following is the full text of the AMBA Ransomware's ransom note:
--------------------------------------------------------------------------------
Место для Вашей рекламы
--------------------------------------------------------------------------------
Вся Ваша информация (документы, базы данных, бэкапы)
на этом компьютере была зашифрована.
Для расшифровки обратитесь по нижеуказанным контактам.
Ни в коем случае не изменяйте файлы!
И не используйте чужие дешифраторы, Вы можете потерять Ваши файлы навсегда.
Каждый дешифратор - уникален, чужой - просто испортит Ваши файлы.
Благодоря нам - вы можете усилить свою безопасность
и предотвратить подобные ситуации!
--------------------------------------------------------------------------------
e-mail: the AMBA(@)riseup.net
-----------------------------------
Ваш код для разблокировки: [-]
---------------------------------------------------------------
Внимание! В первом письме не прикрепляйте файлы для дешифровки.
Все инструкции вы получите в ответном письме.
---------------------------------------------------------------
Preventing the AMBA Ransomware Attack
The AMBA Ransomware is identical to numerous other ransomware threats. All of them carry out a similar attack, using an asymmetric encryption algorithm to encrypt the victim's files without providing a decryption key. The main difference between variants of these threats is the amount of the ransom and some details in the ransom notes and distribution methods. The most common method for distributing the AMBA Ransomware is through corrupted email attachments and embedded links. These threats also are found on peer-to-peer file-sharing networks quite commonly, and it is not uncommon for computer users to become infected after opening a torrent downloaded from one of these sources. The best method for prevention in the case of the AMBA Ransomware is to avoid these sources, use a reliable security program, and have backups of all files on an off-site device.