Devos Ransomware
Devos Ransomware Image
Cybersecurity experts spot new ransomware threats daily, as this is one of the most popular malware types online. Ransomware threats are often regarded as an easy way to make a quick buck with minimum fear of any negative repercussions. Furthermore, the entry barrier is rather low as even inexperienced cyber crooks can create a data-locking Trojan with the help of a ransomware building kit. One of the newest uncovered threats of this class is the Devos Ransomware. The authors of the Devos Ransomware have based their creation on the infamous Phobos Ransomware.
Propagation and Encryption
Spam email campaigns are the most commonly used propagation methods regarding ransomware threats. Normally, the targeted users would receive an email that consists of a bogus message that attempts to convince them to execute the attached file. The email often appears to be sent by a legitimate party such as a well-known company or a government body. If the users launch the macro-laced attachment, their computers will be compromised. Of course, there are other infection vectors that the authors of ransomware often rely on – fake software updates and downloads, fraudulent pirated variants of popular applications and media, malvertising campaigns, etc.
Regardless of the propagation method, the attack gets carried out in an identical manner, usually. The Devos Ransomware would scan the users' computers to locate their data. Next, the data-locking Trojan would trigger its encryption process. The Devos Ransomware applies an encryption algorithm to lock all the targeted files securely. All the files that have undergone the encryption process of the Devos Ransomware will have their names altered because this Trojan adds a '.id[-].[qq1935@mail.fr]. Devos' extension to their names. As you can see by the Devos Ransomware's extension, this threat generated a new and unique ID for each victim. This helps the attackers differentiate between the various users who have fallen victim to their data-locking Trojan.
The Ransom Note
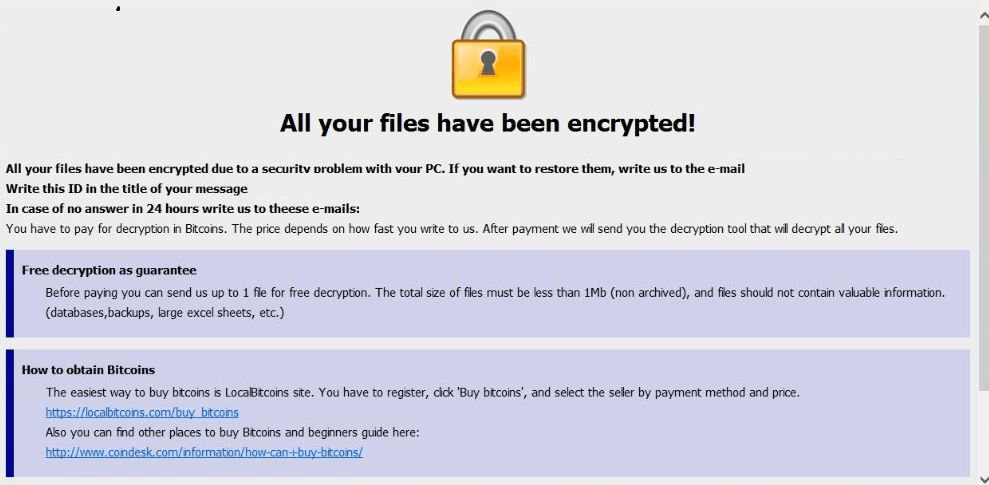
Like most threats of this type, the Devos Ransomware would drop its ransom note on the victim's desktop. The ransom message of the attackers is located in a file named 'info.txt' and in a pop-up window with the name 'info.hta.' In the note, the authors of the Devos Ransomware do not make it clear what the ransom fee is but mention that it will be required in the shape of Bitcoin. They also state that the price would depend on how quickly the victim gets in touch with them. To convince the victims that they are in possession of a working decryption key, the creators of the Devos Ransomware state that they are willing to unlock up to five files free of charge, as long as their total size does not exceed 4MB. The authors of the Devos Ransomware provide the users with instructions on how to obtain Bitcoin. To contact the attackers, the victim has to send an email to the ‘qq1935@mail.fr' email address.
Despite the attackers not mentioning a specific ransom fee, be sure that the amount will be no less than several hundred dollars. Oftentimes, even users who pay up may end up empty-handed as cybercriminals are not the most trustworthy of individuals and would take your money gladly without providing you with the decryption tool promised. This is why it is worth considering investing in a genuine anti-spyware tool that will rid you of the Devos Ransomware and ensure your system's safety in the future.

