Crypt0 Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | September 12, 2016 |
| OS(es) Affected: | Windows |
The Crypt0 Ransomware is an encryption ransomware Trojan that has appeared in several variants previously. The Crypt0 Ransomware belongs to the Detox family of ransomware, which included variants with horror and video game themes on its previous versions. The Crypt0 Ransomware includes large portions of code that have been recycled from other ransomware infections. This family of threats is a relative newcomer to the scene of ransomware Trojans. New variants of Detox, including the Crypt0 Ransomware, still in development currently. While the Crypt0 Ransomware attack is not particularly different from other encryption ransomware Trojans, the Crypt0 Ransomware and other Detox variants do have several unique characteristics that differentiate them from other threats.
Table of Contents
How the Crypt0 Ransomware may Attack a Computer
The earliest versions of the Crypt0 Ransomware leveraged the popularity of the Pokemon GO game to force computer users to pay a ransom. The Crypt0 Ransomware and its other variants will replace the victim's Desktop image with a ransom note that may include vivid images and pop culture references. Detox variants, including the Crypt0 Ransomware, have the ability to take a screenshot of the victim's Desktop, as well as to play an audio file that runs along with the ransom note displayed on the victim's computer. The Crypt0 Ransomware is delivered in an EXE file which will extract and drop four distinct files onto the victim's computer. This is a method that has been observed in other Detox ransomware variants. The different files that have been involved in the Crypt0 Ransomware attack include:
- The first of these files is an image file that is displayed on the victim's Desktop. The Crypt0 Ransomware uses a more generic ransom note image than other, more colorful variants of Detox.
- The second file associated with the Crypt0 Ransomware attack may include some audio content to be played in the background when a pop-up ransom note appears on the victim's computer.
- The Crypt0 Ransomware's encryption and attack is carried out by the executable file that is dropped during the attack. This file may have an innocuous name such as 'MicrosoftHost' to make it appear as just one more, harmless system file. Renaming files in this way is a common tactic used in threat attacks to mislead computer users attempting to find the attacker by searching for any suspicious executable files on their computers.
- There will be a second executable file named 'the Crypt0' or some variant of Detox that will cause the ransom note to appear in a pop-up window while playing the background audio.
Fortunately, a decryption utility is already available for the Crypt0 Ransomware and other Detox variants, allowing computer users to recover from a Crypt0 Ransomware infection by running the decryption utility to decrypt the files. This is not the case in most types of ransomware infections. Because of the availability of a decryption utility, computer users should never pay the Crypt0 Ransomware's ransom, since this would simply allow con artists to continue to develop and release new Crypt0 Ransomware variants, which could be more resilient to removal or no longer compatible with the available decryption utility.
The Crypt0 Ransomware may be Part of a Ransomware as a Service Campaign
Malware analysts suspect that the Crypt0 Ransomware and other Detox variants may be part of a RaaS service (Ransomware as a Service). RaaS allows con artists to create a ransomware Trojan that can be adapted to their particular attack method and specifications quickly. They can simply take the newly created Detox variant and distribute it using their preferred threat distribution method, such as using a botnet to send out large quantities of threatening spam emails or hacking websites to install the Crypt0 Ransomware on the victims' computers directly. The easy availability of RaaS services on underground forums has increased the number of ransomware Trojan attacks in the last few years.
SpyHunter Detects & Remove Crypt0 Ransomware
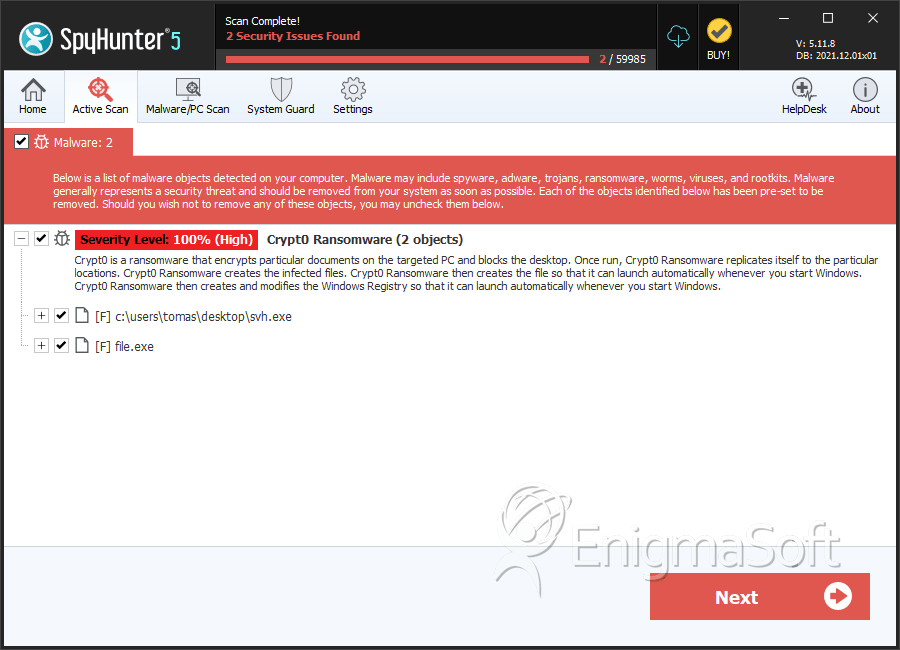
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | svh.exe | 4b6f0113007cddea4ad31237add23786 | 1 |
| 2. | file.exe | 4d178c383cc1e2551854398ee6faf684 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.