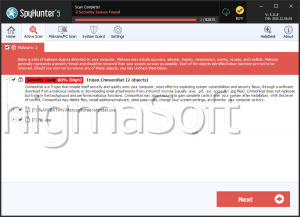
Crimson Ransomware
Crimson Ransomware is the name of a file-locking Trojan that appears to be propagated alongside a threatening malware called STRRAT. Users who have fallen victim to the Crimson Ransomware should not worry too much as they can undo the impairment that has been done to their data rather easily. Luckily, the Crimson Ransomware creators are not highly-skilled as this is not a threat, which is capable of encrypting files. The Crimson Ransomware does not encrypt any data – instead, it simply appends the '.crimson' extension to the names of the affected files. This means that the Crimson Ransomware users' systems have been compromised can simply remove the '.crimson' extension from the names of their files and they will be back to normal.
However, despite the fact that the Crimson Ransomware is not a very harmful threat, it is important to note that the STRRAT malware should not be underestimated. It would appear that every user who has been compromised by the Crimson Ransomware has the STRRAT installed on their computer automatically. The STRRAT is used to collect information regarding your activity and your system.
The Crimson/STRRAT infection chain starts with a rather plain spam email that contains a malicious attachment. The sample examined by security researchers contained no body text, which was either redacted or left blank by the threat actors. It contained a rather interesting attachment, which wasn't a document or a spreadsheet, but a .JAR (Java ARchive) file instead. It's important to note that Outlook prevents access to .jar attachments by default.
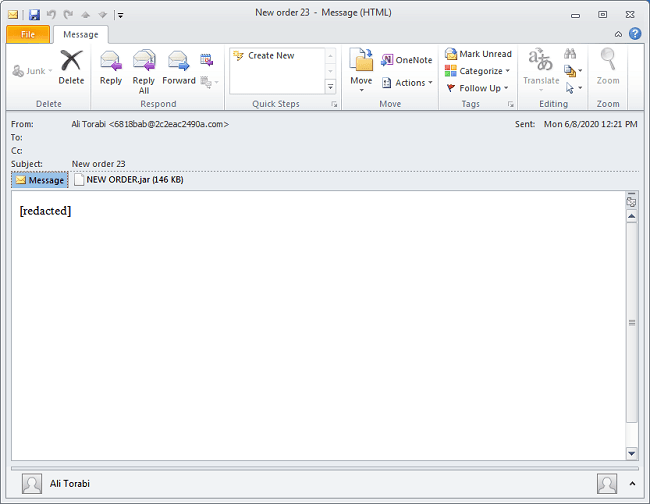
The attachment turns out to be a simple dropper that is used to retrieve a VBScript named bqhoonmpho.vbs, saving it in the home directory and executing it. The VBScript is decoded and executed by PowerShell. It unpacks yet another script that is used to download a Java Runtime Environment, likely a preparation step for the infection of systems that don't have Java installed.
When the STRRAT infects your system, its operators can launch the Crimson Ransomware in an attempt to trick you into thinking that all your data has been encrypted by a dangerous file-locking Trojan. The attackers are using an 'rw-encrypt' command to execute the Crimson Ransomware manually. The creators of this threat can also execute a decryptor manually by using the 'rw-decrypt' command.
Instead of carrying out a complex encryption process, the Crimson Ransomware can only rename the files present on the compromised host. After renaming the user's files, the threat would display a pop-up alert, which appears to have a manually written message for each affected user.
If you are one of the angry users that have been compromised by the Crimson Ransomware, you should not believe the claims of the attackers as they will state that they have encrypted your data. As we have already mentioned, this is not the case, and you should ignore their claims. It is advisable to remove the '.crimson' extension from all your files and install a genuine, up-to-date anti-virus software suite, which will help you remove the Crimson Ransomware and STRRAT from your PC safely.