CoNFicker Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 43,217 |
| First Seen: | April 18, 2017 |
| Last Seen: | May 21, 2020 |
| OS(es) Affected: | Windows |
Although the CoNFicker Ransomware seems to draw its name from a threat infection that has been around for a while, there is no connection between the CoNFicker Ransomware and previous threats with similar names. The CoNFicker Ransomware is a ransomware Trojan released on April 17, 2017, which carries out a typical ransomware tactic. Like most ransomware Trojans, the CoNFicker Ransomware is designed to encrypt the victims' files and then ask for the payment of a ransom in exchange for the decryption key, needed to recover the affected files. The CoNFicker Ransomware may be distributed through corrupted email attachments that use corrupted scripts to execute a compromised code on the victim's computer. The CoNFicker Ransomware is being delivered to the victims' computers in the form of a fake version of WinRAR, software used to create, read, and manage RAR archive files currently.
Table of Contents
How the CoNFicker Ransomware will Attack Your Files
When the CoNFicker Ransomware is installed on a computer, it deletes the System Restore points, the Shadow Volume Copies, and other Windows recovery components. It then scans the infected computer's drives for files to encrypt in the attack. The CoNFicker Ransomware will encrypt numerous file types, looking for file formats that could be valuable to the victim. The following are some of the file types that are encrypted in the CoNFicker Ransomware attack:
.3GP, .7Z, .APK, .AVI, .BMP, .CDR, .CER, .CHM, .CONF, .CSS, .CSV, .DAT, .DB, .DBF, .DJVU, .DBX, .DOCM, ,DOC, .EPUB, .DOCX .FB2, .FLV, .GIF, .GZ, .ISO .IBOOKS,.JPEG, .JPG, .KEY, .MDB .MD2, .MDF, .MHT, .MOBI .MHTM, .MKV, .MOV, .MP3, .MP4, .MPG .MPEG, .PICT, .PDF, .PPS, .PKG, .PNG, .PPT .PPTX, .PPSX, .PSD, .RAR, .RTF, .SCR, .SWF, .SAV, .TIFF, .TIF, .TBL, .TORRENT, .TXT, .VSD, .WMV, .XLS, .XLSX, .XPS, .XML, .CKP, .ZIP, .JAVA, .PY, .ASM, .C, .CPP, .CS, .JS, .PHP, .DACPAC, .RBW, .RB, .MRG, .DCX, .DB3, .SQL, .SQLITE3, .SQLITE, .SQLITEDB, .PSD, .PSP, .PDB, .DXF, .DWG, .DRW, .CASB, .CCP, .CAL, .CMX, .CR2.
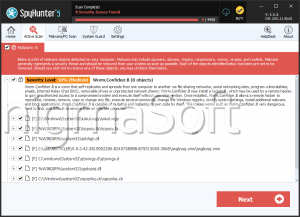
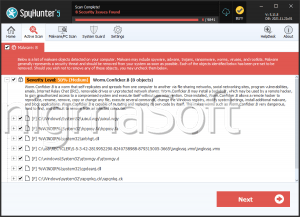
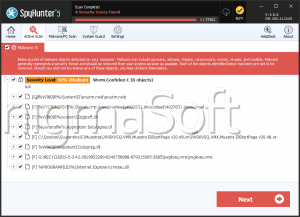
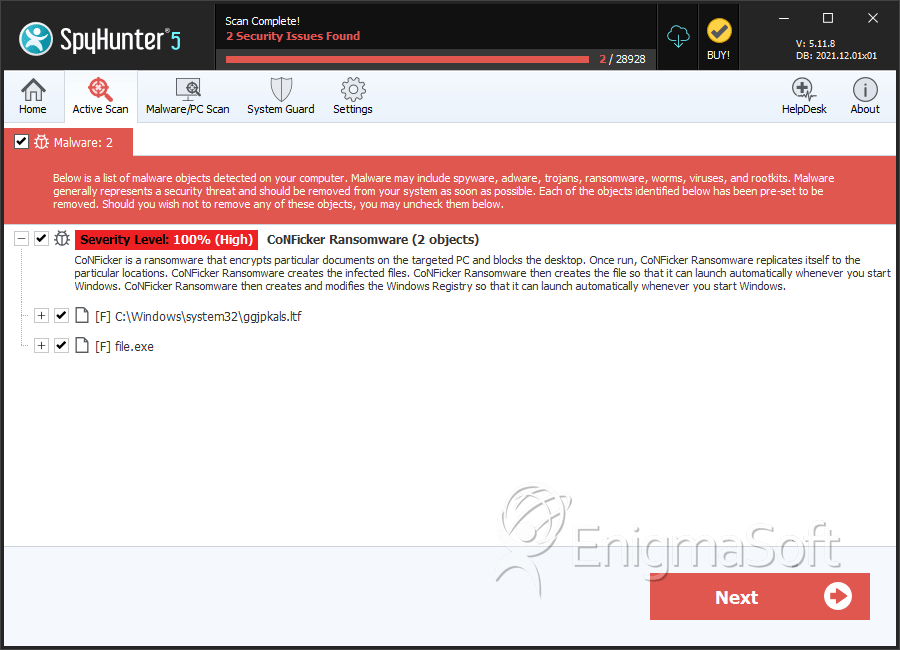
The CoNFicker Ransomware is installed in the AppData directory on the infected computer and may create the following files during its attack:
- C_o_N_F_i_c_k_e_r Decryptor.exe
- Decrypt.txt
- conficker.exe
- ransomwarefineched.exe
- winrar 2017.exe
- winrar Setup 2017.exe
To take the victim's files hostage, the CoNFicker Ransomware uses the AES 256 encryption to make the files inaccessible completely. The decryption key that should be used to recover the affected files is held on the CoNFicker Ransomware's Command and Control servers, away from the victim. This is an approach that is used by the vast majority of ransomware Trojans. The CoNFicker Ransomware then delivers a ransom note, demanding payment in exchange for the decryption key. The CoNFicker Ransomware demands a ransom of 0.5 BitCoin (approximately $600 USD at the exchange rate at the time of writing). The CoNFicker Ransomware delivers its ransom note in a text file named 'Decrypt.txt' and in the form of a Desktop wallpaper image that replaces the victim's Desktop image. The text that is contained in the CoNFicker Ransomware's ransom notes reads as follows:
- 'C_o_N_F_i_c_k_e_r R_A_N_S_O_M_W_A_R_E
#####
Attention! Attention! Attention! Your Files has been encrypted By C_o_N_F_i_c_k_e_r R_A_N_S_O_M_W_A_R_E
#####
Send 0.5 Bitcoin To @ 1sUCn6JYa7B96t4nZz1tX5muU2W5YxCmS @
#####
And Contact us By Email :
Conficker-decryptor@mail.ru
If Send 0.5 Bitcoin We will send you the decryption key C_o_N_F_i_c_k_e_r Decryptor'
Protecting Your Computer from the CoNFicker Ransomware
The best protection from ransomware Trojans like the CoNFicker Ransomware is to have backups of all files, preferably on an external memory device or the cloud. Being able to recover files from a backup quickly nullifies the CoNFicker Ransomware attack completely and takes away all power from the people responsible for these infections. Apart from having file backups, it is also primordial to have a reliable security program that is fully up-to-date that is capable of detecting and intercepting the CoNFicker Ransomware infection. Learning to recognize these tactics is also an essential part of dealing with these infections. A combination of caution when dealing with spam email, file backups, and a reliable security software can prevent most of the CoNFicker Ransomware infections and similar threats.
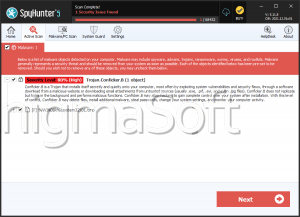
SpyHunter Detects & Remove CoNFicker Ransomware
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ggjpkals.ltf | 08f3ce046ff7efd50fd60bb3c6457a32 | 43,215 |
| 2. | file.exe | d9d3381b79fb6e35ba995b4a7ab58b4f | 0 |