Chimera Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 16,640 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 52 |
| First Seen: | September 23, 2015 |
| Last Seen: | November 26, 2025 |
| OS(es) Affected: | Windows |
The Chimera Ransomware is a ransomware infection. Ransomware refers to threats that take the victim's computer or file hostage and then demands payment of a to return them. The Chimera Ransomware carries out a basic version of this attack, encrypting the victim's files. This means that, even if the Chimera Ransomware is removed, the encrypted files are not recoverable without the decryption key (which is not supposedly available until the victim pays a hefty ransom using BitCoins). Because of this, the best protection from the Chimera Ransomware is to backup all your files using Cloud or an external memory drive. That way, even if your files are encrypted by the Chimera Ransomware, the infection can be removed and the files restored from their backup without having to lose money and, at the same time, enabling the people responsible for the Chimera Ransomware to carry out more attacks.
Table of Contents
How the Chimera Ransomware Attack Works
The Chimera Ransomware is very similar to many other encryption ransomware threats that have multiplied in recent years. The Chimera Ransomware deletes itself from the victim's computer system as soon as the Chimera Ransomware finishes encrypting the victim's files. The Chimera Ransomware leaves behind a ransom note with instructions on how to pay the Chimera Ransomware's ransom. The Chimera Ransomware is a Trojan infection, meaning that the Chimera Ransomware cannot spread by itself, but relies on other threats or social engineering to trick inexperienced computer users into installing this Trojan themselves. In most cases, the Chimera Ransomware is delivered using corrupted spam email attachments or distributed through shady websites with poorly regulated advertising content or that have been compromised so that they may deliver threats to their visitors.
Once the Chimera Ransomware is installed, the Chimera Ransomware encrypts the user profiles on the affected computer and scans the victim's drives for files with certain extensions. The Chimera Ransomware changes the files' extensions to .CRYPT and displays a message with instructions on how to pay it. The following is the message that has been associated with the Chimera Ransomware:
" Sie wurden Opfer der Chimera Malware. Ihre privaten Dateien wurden verschlusselt und sind ohne eine spezielle Schliusseldatei nicht wiederherstellbar. Moglicherweise funktionieren einige Programme nicht mehr ordnungsemass!"
This message, written in German, reflects the fact that the Chimera Ransomware has mostly been used to target computers in Germany. The current ransom demanded by Chimera Ransomware is 0,93002414 Bitcoins using TOR to maintain anonymity. This ransom that amounts to several hundred dollars does not guarantee that the people responsible for the Chimera Ransomware will restore your files. Because of this, computer users should always back up essential files, preventing them from becoming a victim of these kinds of tactics.
Dealing with the Chimera Ransomware and Similar Encryption Ransomware
If the Chimera Ransomware has been installed on your computer, this will mean that your files have been encrypted. Unfortunately, the Chimera Ransomware will also delete shadow volume copies of files the Chimera Ransomware encrypts, meaning that tools like Shadow Explorer may not work to restore the files encrypted by the Chimera Ransomware. Affected computer users should ensure that all traces of the Chimera Ransomware have been removed before attempting to restore files from a backup. Otherwise, the entire encryption process may simply repeat itself. Although the Chimera Ransomware deletes itself after encrypting the victim's files, the source files or links for the Chimera Ransomware infection may still be present or accessed by the affected computer user. The best solution is to wipe the affected drives entirely and then restore them from their backed up location. If the encrypted files are not backed up then, unfortunately, there is no solution to restore them except paying the ransom and hoping for the best (PC security researchers strongly advise against paying the Chimera Ransomware's ransom; instead, computer users should initiate good backup policies to ensure that important files are always duplicated to be protected from these kinds of attacks).
Aliases
14 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| AVG | MSIL9.RN |
| Fortinet | MSIL/LXY.BIV!tr |
| Ikarus | Trojan.MSIL.Injector |
| Panda | Trj/CI.A |
| McAfee | Artemis!60FABD1A2509 |
| Microsoft | Trojan:Win32/Dynamer!ac |
| Antiy-AVL | Trojan[Spy]/Win32.Selltim |
| Sophos | Troj/Ransom-BIV |
| McAfee-GW-Edition | BehavesLike.Win32.BackdoorNJRat.dm |
| TrendMicro | TROJ_GEN.R00XC0RIM15 |
| Kaspersky | Trojan-Spy.Win32.Selltim.sl |
| Avast | Win32:Malware-gen |
| Symantec | Suspicious.Cloud.2 |
| K7AntiVirus | Trojan ( 004cfc921 ) |
SpyHunter Detects & Remove Chimera Ransomware
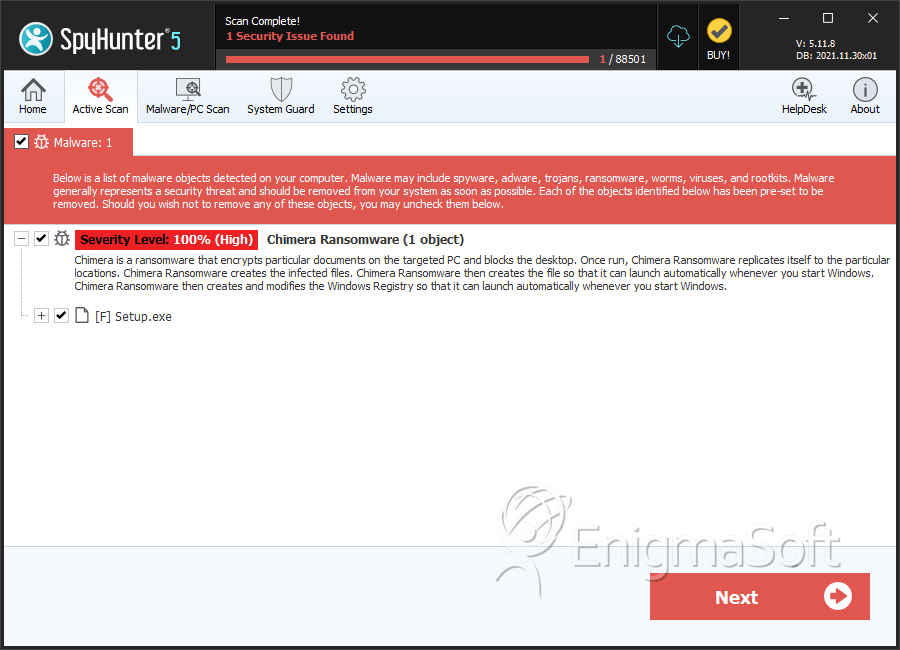
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | HawkEye.exe | 60fabd1a2509b59831876d5e2aa71a6b | 25 |