Charming Kitten APT
Charming Kitten, also known as APT35, is an advanced persistent threat, a hacker group with suspected Iranian ties. The group is also known under other names: Phosphorus, Ajax Security Team, and Newscaster Team. Charming Kitten has been observed to have politically motivated campaigns, but also ones motivated by financial reasons. They're aiming for human rights activists, media organizations, and the academic sector. The majority of their campaigns were pushing for attacks on the United Kingdom, United States, Iran, and Israel.
Table of Contents
Charming Kitten Campaigns
One of the more expansive operations undertaken by the hacker group was carried out against HBO in 2017. The cybercriminals leaked about a terabyte of data with personal information on the company staff, upcoming shows, and more. Other attacks staged by Charming Kitten, a.k.a. APT35 included access to detailed data through a US Air Force defector and spoofing the website of an Israeli cybersecurity company to steal login details. The attack that tied them to Iran was a 2018 operation aimed at political activists that influenced the sanctions aimed against the country. Charming Kitten operatives used phishing emails with malicious attachments and social engineering to pose as high ranking professionals.
The Iranian Angle for Charming Kitten
Targeted phishing campaigns were part of the way the APT35 (Charming Kitten) do business, as could be seen with their 2019 campaign that aimed at impersonating ex-Wall Street Journal journalists. They used that approach to sink their claws into their victims with the promise of interviews or invitations to webinars, often on the topics of Iranian and international affairs at the time.
In one of these cases, the attackers composed an email in Arabic under the fake identity imitating the real-life Farnaz Fassihi, an ex-Wall Street Journal employee with 17 years working for the publication. The Charming Kitten operatives presented this fake persona as still working for WSJ.
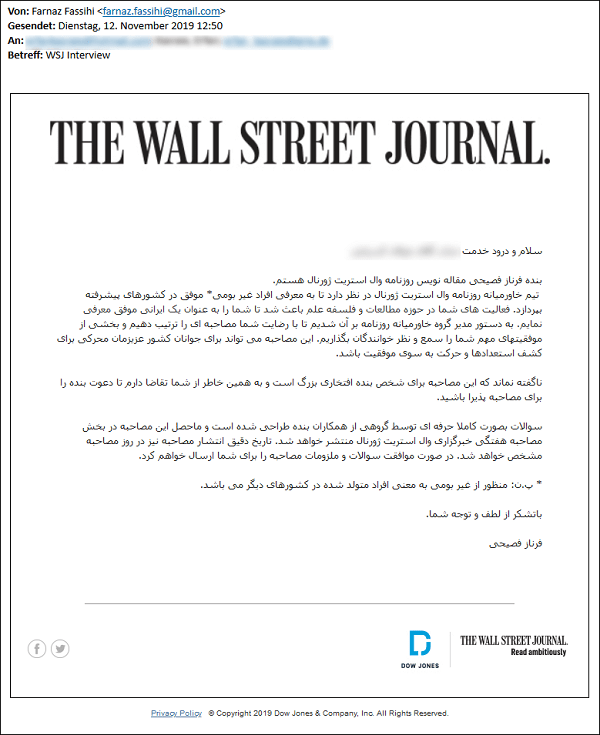
Fake interview request. Source: blog.certfa.com
The email's contents were as follows:
Hello *** ***** ******
My name is Farnaz Fasihi. I am a journalist at the Wall Street Journal newspaper.
The Middle East team of the WSJ intends to introduce successful non-local individuals in developed countries. Your activities in the fields of research and philosophy of science led me to introduce you as a successful Iranian. The director of the Middle East team asked us to set up an interview with you and share some of your important achievements with our audience. This interview could motivate the youth of our beloved country to discover their talents and move toward success.
Needless to say, this interview is a great honor for me personally, and I urge you to accept my invitation for the interview.
The questions are designed professionally by a group of my colleagues and the resulting interview will be published in the Weekly Interview section of the WSJ. I will send you the questions and requirements of the interview as soon as you accept.
*Footnote: Non-local refers to people who were born in other countries.
Thank you for your kindness and attention.
Farnaz Fasihi
The links within the emails were in a short URL format, often used by threat actors to disguise legitimate links behind them, aiming at data collection of IP addresses, browser, and OS versions and more. That helped pave the way to further attacks by building trust with repeated communication and preparing for the moment to act.
Once trust is established over time, the hackers send off a link that contains the alleged interview questions. The Computer Emergency Response Team in Farsi (CERTFA) samples showed the attackers were using a method used by phishers in recent years, with Google Sites-hosted pages.
Once the victim opens the link, they may be redirected to another fake page that attempts to record their login credentials and two-factor authentication code through the use of a phishing kit.
Summary of Charming Kitten Operations
In 2015 the first wave of phishing attacks was discovered by researchers, with later espionage operations on a massive scale being discovered from 2016 to 2017 by researchers at ClearSky. The Charming Kitten operators used impersonation, spear-phishing, and watering hole attacks.
In 2018 Charming Kitten cybercriminals went after ClearSky with a fraudulent website impersonating the security company's portal. More attacks were identified that year against Middle Eastern targets with a fake email campaign and fake websites.
In 2019 Charming Kitten (APT35) activities expanded by targeting of non-Iranians in the US, Middle East, and France, with targeting of public figures outside the academic fiends they were going for initially. They began attaching a tracker to their email correspondence to follow emails forwarded to other accounts, intending to obtain geolocation data.
>>>Update May 10th, 2020 - APT35 (Charming Kitten) Involved In COVID-19 Hacking Campaign
A set of publicly available web archives reviewed by cybersecurity experts revealed that the Iranian hacking group known as Charming Kitten, among other names, was behind an April cyber-attack against Gilead Sciences Inc California-based drug company involved in COVID-19 research.
In one of the instances that the security researchers came across, the hackers used a bogus email login page that was specifically designed to steal passwords from a top Gilead executive, involved in corporate and legal affairs. The attack was found on a website that is used to scan web addresses for malicious activity, but the researchers weren't able to determine whether it was successful.
One of the analysts that researched the attack was Ohad Zaidenberg from Israeli cybersecurity firm ClearSky. He commented that the April attack against Gilead was an effort to compromise corporate email accounts with a message that impersonated a journalist inquiry. Other analysts, who weren't authorized to comment publicly have since confirmed that the attack used domains and servers that were previously used by the Iranian hacking group known as Charming Kitten.
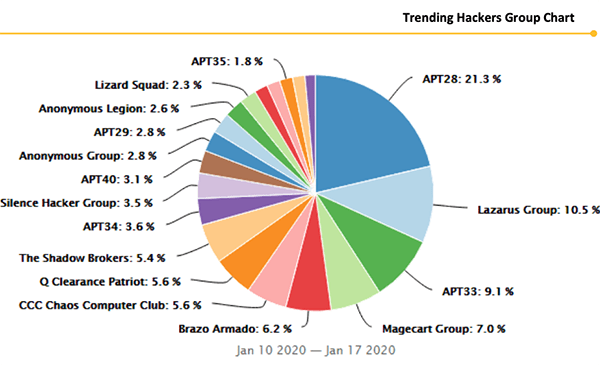
Trending APT Hacker Groups Chart - Source: Securitystack.co
Iran's diplomatic mission to the United Nations has denied any involvement in such attacks, with spokesman Alireza Miryousefi stating that "The Iranian government does not engage in cyber warfare," adding "Cyber activities Iran engages in are purely defensive and to protect against further attacks on Iranian infrastructure."
Gilead has followed company policy on discussing cybersecurity matters and declined to comment. The company has received much attention recently, as it is the manufacturer of the antiviral drug remdesivir, which is currently the only treatment proved to help patients infected with COVID-19. Gilead is also one of the companies leading the research and development of a treatment for the deadly disease, making it a prime target for intelligence-gathering efforts.

