APT35
 The APT35 (Advanced Persistent Threat) is a hacking group that is believed to originate from Iran. This hacking group is also known under several other aliases – Newscaster Team, Phosphorus, Charming Kitten and Ajax Security Team. The APT35 hacking group is usually involved both in politically motivated campaigns, as well as financially motivated ones. The APT35 hacking group tends to concentrate their efforts against actors involved in human rights activism, various media organizations, and the academic sector mainly. Most of the campaigns are carried out in the United States, Israel, Iran and the United Kingdom.
The APT35 (Advanced Persistent Threat) is a hacking group that is believed to originate from Iran. This hacking group is also known under several other aliases – Newscaster Team, Phosphorus, Charming Kitten and Ajax Security Team. The APT35 hacking group is usually involved both in politically motivated campaigns, as well as financially motivated ones. The APT35 hacking group tends to concentrate their efforts against actors involved in human rights activism, various media organizations, and the academic sector mainly. Most of the campaigns are carried out in the United States, Israel, Iran and the United Kingdom.
Table of Contents
Popular APT35 Campaigns
One of the most notorious APT35 operations is the one carried out against HBO that took place in 2017. In it, the APT35 leaked over 1TB of data, which consisted of staff personal details and shows, which were yet to be aired officially. Another infamous APT35 campaign that put them on the map is the one that also involved a U.S. Air Force defector. The individual in question aided APT35 in getting access to classified government data. In 2018, the APT35 group built a website that was meant to mimic a legitimate Israeli cybersecurity company. The only difference was that the fake website had a slightly altered domain name. This campaign helped the APT35 get the login details of some of the company’s clients. The latest infamous campaign involving the APT35 was carried out in December 2018. In this operation, the APT35 group operated under the Charming Kitten alias. This operation targeted various political activists who had influence in the economic sanctions, as well as military sanctions placed on Iran at the time. The APT35 group posed as high-ranking professionals involved in the same fields as their targets. The attackers used tailored phishing emails carrying fake attachments, as well as bogus social media profiles.
Phishing With Bogus Interview Emails
Targeted phishing campaigns are part of Charming Kitten's modus operandi, with the hackers using fake emails and social engineering as execution methods. In one 2019 campaign, the Charming Kitten group impersonated former Wall Street Journal (WSJ) journalists and approached their intended victims with a fake interview scenario. The group has also been spotted using different scenarios, such as ''CNN Interview'' and ''Invitation to a Deutsche Welle Webinar'', usually around topics of Iranian and international affairs.
In one particular case, the attackers created a bogus email in Arabic, using the identity of Farnaz Fassihi, currently a New York Times journalist, who had previously worked for The Wall Street Journal for 17 years. Interestingly enough, the hackers presented Farnaz Fassihi as working for her former employer, The Wall Street Journal.
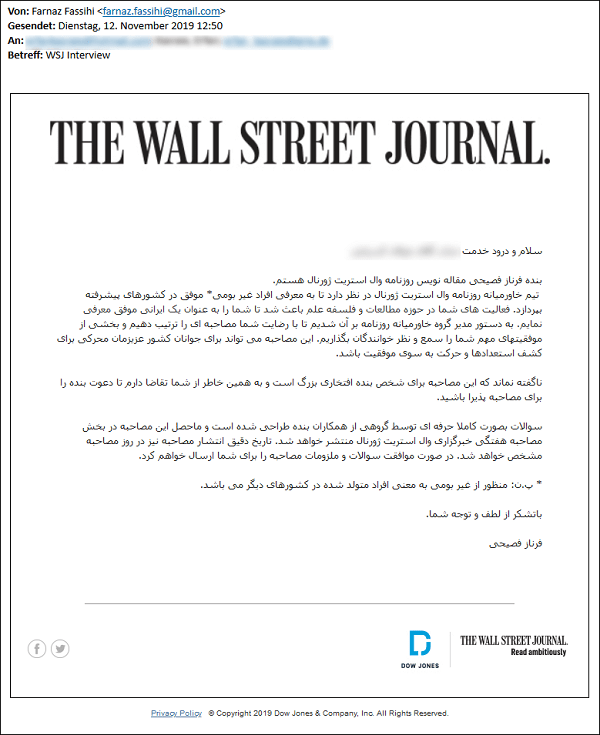
Fake interview request email - Source: blog.certfa.com
Email translation:
Hello *** ***** ******
My name is Farnaz Fasihi. I am a journalist at the Wall Street Journal newspaper.
The Middle East team of the WSJ intends to introduce successful non-local individuals in developed countries. Your activities in the fields of research and philosophy of science led me to introduce you as a successful Iranian. The director of the Middle East team asked us to set up an interview with you and share some of your important achievements with our audience. This interview could motivate the youth of our beloved country to discover their talents and move toward success.
Needless to say, this interview is a great honor for me personally, and I urge you to accept my invitation for the interview.
The questions are designed professionally by a group of my colleagues and the resulting interview will be published in the Weekly Interview section of the WSJ. I will send you the questions and requirements of the interview as soon as you accept.
*Footnote: Non-local refers to people who were born in other countries.
Thank you for your kindness and attention.
Farnaz Fasihi
All the links contained in the emails were in shortened URL format, which was used by hackers to guide their victim to legitimate addresses, while gathering essential information about their devices, such as operating system, browser, and IP address. This information was needed from the hackers in preparation for the main attack on their targets.
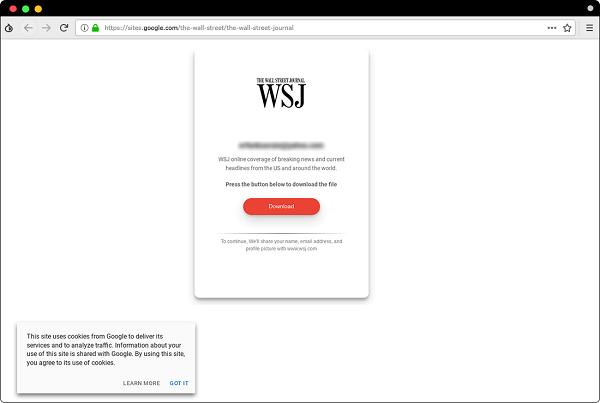
Sample of fake WSJ page hosted on Google Sites - Source: blog.certfa.com
After establishing relative trust with the intended target, the hackers would send them a unique link, that allegedly contains the interview questions. According to samples tested by the Computer Emergency Response Team in Farsi (CERTFA), the attackers are using a relatively new method that has gained a lot of popularity with phishers over the past year, hosting pages on Google Sites.
Once the victim clicks the ''Download'' button on the Google Site page, they will be redirected to another fake page that will attempt to harvest login credentials for their email address and their two-factor authentication code, using phishing kits like Modlishka.
APT35’s DownPaper Malware
The DownPaper tool is a backdoor Trojan, which is mostly used as a first-stage payload and has the capabilities to:
- Establish a connection with the attacker’s C&C (Command & Control) server and receive commands and harmful payloads, which are to be executed on the infiltrated host.
- Gain persistence by tampering with the Windows Registry.
- Gather information about the compromised system, such as hardware and software data.
- Execute CMD and PowerShell commands.
The APT35 hacking group is a very persistent group of individuals, and it is unlikely that they plan on halting their activities any time soon. Keeping in mind that the political climate around Iran has been heating up for a while, it is likely that we will keep hearing about the APT35 group’s campaigns in the future.
Update May 10th, 2020 - APT35 Involved In COVID-19 Hacking Campaign
A set of publicly available web archives reviewed by cybersecurity experts revealed that the Iranian hacking group known as Charming Kitten, among other names, was behind an April cyber-attack against Gilead Sciences Inc California-based drug company involved in COVID-19 research.
In one of the instances that the security researchers came across, the hackers used a bogus email login page that was specifically designed to steal passwords from a top Gilead executive, involved in corporate and legal affairs. The attack was found on a website that is used to scan web addresses for malicious activity, but the researchers weren't able to determine whether it was successful.
Trending APT Hacker Groups Chart - Source: Securitystack.co
One of the analysts that researched the attack was Ohad Zaidenberg from Israeli cybersecurity firm ClearSky. He commented that the April attack against Gilead was an effort to compromise corporate email accounts with a message that impersonated a journalist inquiry. Other analysts, who weren't authorized to comment publicly have since confirmed that the attack used domains and servers that were previously used by the Iranian hacking group known as Charming Kitten.
Iran's diplomatic mission to the United Nations has denied any involvement in such attacks, with spokesman Alireza Miryousefi stating that "The Iranian government does not engage in cyber warfare," adding "Cyber activities Iran engages in are purely defensive and to protect against further attacks on Iranian infrastructure."
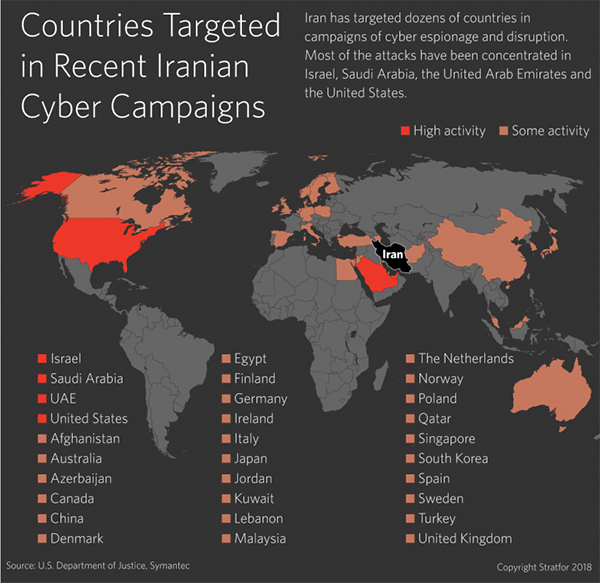
Countries Targeted in Recent Iranian Cyber Campaigns - Source: Stratfor.com
Gilead has followed company policy on discussing cybersecurity matters and declined to comment. The company has received a lot of attention recently, as it is the manufacturer of the antiviral drug remdesivir, which is currently the only treatment proved to help patients infected with COVID-19. Gilead is also one of the companies leading the research and development of a treatment for the deadly disease, making it a prime target for intelligence-gathering efforts.

