BSS Ransomware
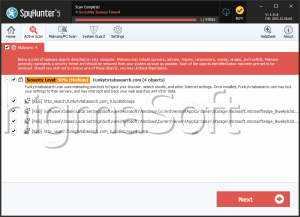
The BSS Ransomware is an encryption ransomware Trojan that is based on HiddenTear, an open ransomware platform that has been the basis for countless ransomware threats since it was first released in August 2015. The BSS Ransomware variant first appeared on January 23, 2019, and seems to be still in an unfinished state. However, at this time, the BSS Ransomware still poses a threat to computer users and is capable of executing an effective encryption ransomware attack.
Table of Contents
How the BSS Ransomware Infection Works
The BSS Ransomware, like other encryption ransomware Trojans, is designed to take over the victim's computer, enciphering the victim's files with a strong encryption algorithm and then demanding payment of a ransom. The BSS Ransomware targets the user-generated files such as media files, databases, documents and numerous others. The BSS Ransomware targets the files specified below in these attacks:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
The BSS Ransomware applies an AES encryption algorithm to make the affected files unusable, marking each compromised file with the file extension '.bss_locked,' which is added to the file's name. The BSS Ransomware delivers its ransom note in the form of an HTA application named 'Ransomware by BSS,' which displays the following text in a program window on the victim's computer after the victim's files have been taken hostage:
'Files has been encrypted with ransomware
Send me some bitcoins or kebap
And I also hate deers and coffee
by the way... the password is:'
Dealing with the BSS Ransomware Attack
There is no way for the victims to contact the criminals or pay the ransom. It also seems that the BSS Ransomware does not connect to Command and Control servers. This may indicate that the BSS Ransomware is unfinished. However, the BSS Ransomware is still capable of encrypting the victims' files, essentially functioning as a data wiper. Since it is not possible to restore files the encrypted by the BSS Ransomware, the best way of dealing with the BSS Ransomware is to take precautionary measures against the BSS Ransomware and other encryption ransomware Trojans that are active currently.
Preventing a BSS Ransomware Attack
The best protection against threats like the BSS Ransomware is to have file backups. This allows computer users respond to a BSS Ransomware infection by replacing the compromised files with a backup copy. Apart from file backups, it is basic to have a security program installed that is capable of intercepting and removing threats like the BSS Ransomware before they carry out their attacks.