Blocked2 Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 5 |
| First Seen: | August 31, 2017 |
| Last Seen: | February 15, 2019 |
| OS(es) Affected: | Windows |
The Blocked2 Ransomware is a variant of Xorist (also known as EnCiPhErEd), a ransomware family that is offered as a RaaS (Ransomware as a Service), which con artists can use to create their own customized version of the attack. The Blocked2 Ransomware variant marks the files encrypted by the attack by using the file extension 'Blocked2', which is added to each file's name after it has been enciphered by the Blocked2 Ransomware. There are numerous variants of Xorist, all nearly identical the Blocked2 Ransomware, and they have been observed to use the following file extensions to mark the encrypted files:
.error, .errorfiles, .@EnCrYpTeD2016@, .pa2384259, .Cerber_RansomWare@qq[dot]com, .hello, .brb, .RusVon, .fast_decrypt_and_protect@tutanota[dot]com, .antihacker2017.encoderpass, .fileiscryptedhard, .6FKR8d, .EnCiPhErEd, .xdata, .SaMsUnG, .zixer2, .73i87A, .p5tkjw, .PoAr2w, .ava.
Table of Contents
How the Blocked2 Ransomware Carries out Its Attack
The main purpose of the Blocked2 Ransomware is to encrypt the victims' files with a strong encryption algorithm. After doing this, the Blocked2 Ransomware delivers a ransom message, which alerts the victims about the attack and asks the victims to pay a ransom in exchange for the decryption key that is needed to restore the files encrypted by the Blocked2 Ransomware. There are various characteristics of the Blocked2 Ransomware and its variants, which can vary from one variant to the other. For example, in the original Xorist ransomware Trojan, SMS was used to contact the victim with the threat creator. Using the Encoder Builder, a ransomware builder that the con artists can purchase on the Dark Web or shady Web pages, creates the Blocked2 Ransomware and other ransomware Trojans in the Xorist family. Xorist variants support two encryption types, the XOR or TEA, unlike most active ransomware Trojans that tend to use the AES and RSA encryptions in their attack. The con artists will create their customized versions of Xorist and then receive the ransomware executable file that they can then distribute using different methods, such as spam email messages or by delivering it through unsecured Remote Desktop Protocol connections directly. Fortunately, there are variants of the Blocked2 Ransomware that can be decrypted with the use of an available decryption software. The Blocked2 Ransomware may be one of these.
The Blocked2 Ransomware’s Predecessors and the Original Xorist Ransomware
The default version of the Blocked2 Ransomware will deliver a ransom note named 'HOW TO DECRYPT FILES.txt' that is installed on the infected computer's desktop. The ransom note contains the following message:
'Attention! All your files are encrypted!
To restore your files and access them,
please send an SMS with the text XXXX to YYYY number.
You have N attempts to enter the code.
When that number has been exceeded,
all the data irreversibly is destroyed.
Be careful when you enter the code!'
The original Xorist ransomware Trojan and its many variants will target the file types (as this ransomware family has developed, it is likely that more file types have been added to this list):
*.zip, *.rar, *.7z, *.tar, *.gzip, *.jpg, *.jpeg, *.psd, *.cdr, *.dwg, *.max, *.bmp, *.gif, *.png, *.doc, *.docx, *.xls, *.xlsx, *.ppt, *.pptx, *.txt, *.pdf, *.djvu, *.htm, *.html, *.mdb, *.cer, *.p12, *.pfx, *.kwm, *.pwm, *.1cd, *.md, *.mdf, *.dbf, *.odt, *.vob, *.ifo, *.lnk, *.torrent, *.mov, *.m2v, *.3gp, *.mpeg, *.mpg, *.flv, *.avi, *.mp4, *.wmv, *.divx, *.mkv, *.mp3, *.wav, *.flac, *.ape, *.wma, *.ac3.
However, the Blocked2 Ransomware and other ransomware Trojans in the Xorist family are not sophisticated particularly, and it is possible for computer users to take steps to protect their data from these attacks. However, the fact that these threats can be customized and they are such adaptable means that they pose a significant threat to computer users. Because of this, PC security researchers advise computer users to take steps to protect their data. The best protection against the Blocked2 Ransomware and most encryption ransomware Trojans is to have a reliable backup system on the cloud or an external device, allowing an easy recovery of any encrypted files.
SpyHunter Detects & Remove Blocked2 Ransomware
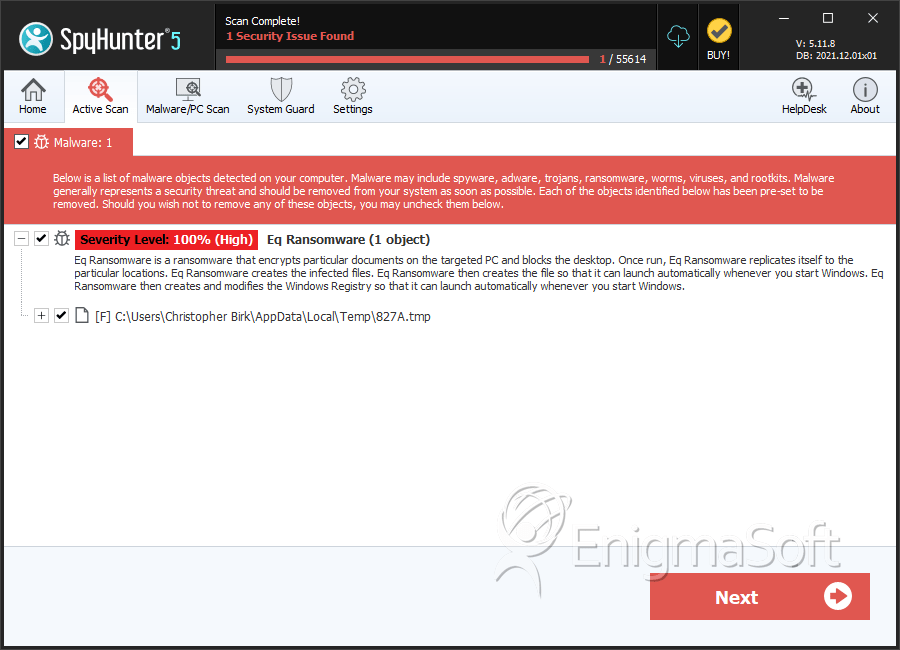
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 827A.tmp | ee5fa4a6c9be3b2adfff4ad6d7eb0a4d | 3 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.