BitCryptor Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 8 |
| First Seen: | May 14, 2015 |
| Last Seen: | August 17, 2022 |
| OS(es) Affected: | Windows |
The BitCryptor Ransomware is a threat designed to encrypt files. Using RSA-2048 key (AES CBC 256-bit encryption algorithm) to encrypt the victims' files, the BitCryptor Ransomware essentially takes their computers hostage. The BitCryptor Ransomware displays a message indicating that the victim has 96 hours to pay a ransom of 1 BitCoin (approximately $240 at the time of writing), or the files will be deleted. Unfortunately, recovering the encrypted files without the decryption key is nearly impossible with current technology. In some cases, computer users may be able to recover some of their files through the Shadow Volume. However, the BitCryptor Ransomware does have functionality that deletes Shadow copies, so this option isn't open to everyone.
Table of Contents
How the BitCryptor Ransomware may Enter a Computer
The BitCryptor Ransomware is distributed using typical threat delivery methods. Some examples of how the BitCryptor Ransomware is distributed include corrupted email attachments and links, attack websites and social engineering techniques. The BitCryptor Ransomware also may be delivered by other threats, which may drop the BitCryptor Ransomware and other threats on a computer. In many cases, computer users may download and install the BitCryptor Ransomware thinking that the BitCryptor Ransomware is a legitimate program. For example, PC security researchers have observed copies of the BitCryptor Ransomware disguised as Adobe Flash Player updates.
How the BitCryptor Ransomware Works
The BitCryptor Ransomware may affect all versions of the Windows operating system, including Windows 8, Windows 7, Windows Vista and Windows XP. The BitCryptor Ransomware uses a strong encryption method to leave computer users with no choice but to pay for the decryption key if they wish to recover access to their files. The BitCryptor Ransomware is part of a large family of ransomware known as CryptoGraphic Locker. These ransomware infections are characterized by the fact that their payment system is not located online but is integrated into the BitCryptor Ransomware executable. The BitCryptor Ransomware and other threats in this family offer to decrypt a single file (with a size limit) to prove to the computer user that the BitCryptor Ransomware is capable of decrypting the affected files. The BitCryptor Ransomware targets files with extensions corresponding to productivity programs specifically, meaning that the BitCryptor Ransomware is likelier to encrypt an important work or personal files. The following is the full list of extensions targeted by the BitCryptor Ransomware attack:
.sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .odt.
The BitCryptor Ransomware also hijacks executable files on the infected computer so that they will delete Shadow Volume Copies whenever they are executed. Right after the Shadow Volume Copies are erased, the BitCryptor Ransomware returns executable files to normal. This means that the time window for accessing Shadow Volume Copies is very short and generally unavailable to most computer users.
As part of its attack, the BitCryptor Ransomware will change the victim's desktop image, include a window with a countdown timer and display the following message:
Your personal documents and files on this computer have just been encrypted.
The original files have been deleted and will only be recovered by following the steps described below.
Click on "Show encrypted files" to see a list of files that got encrypted.
The encryption was done with a unique generated encryption key (using AES-256).
This means that encrypted files are of no use until they get decrypted using a key stored on a server.
This server will only release the key if the amount of Bitcoins (displayed left of this window) is send to the Bitcoin address shown on the left of this window.
The initial cost is 1 BitCoin, and it increases each time the countdown restarts.
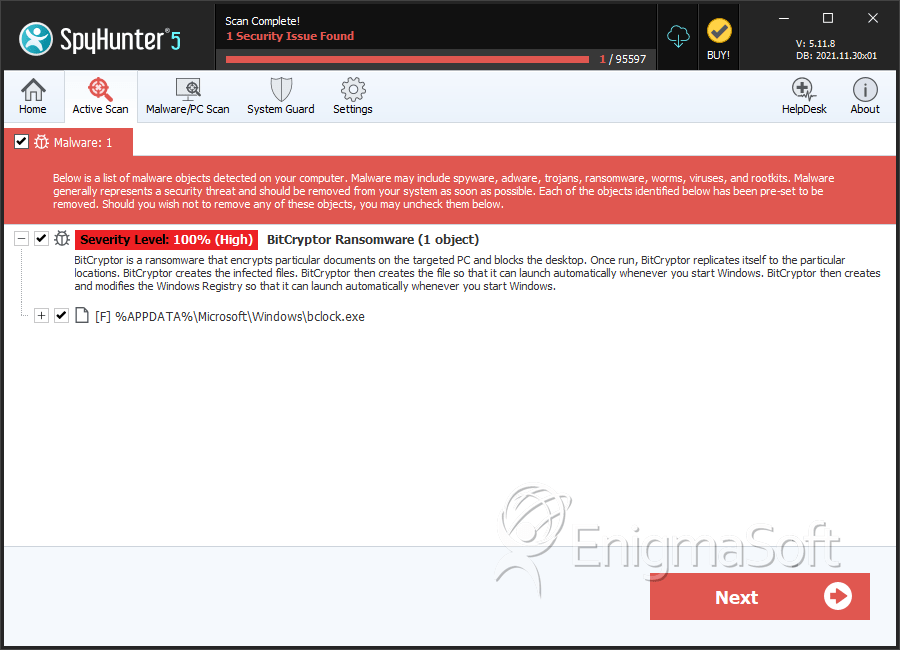
SpyHunter Detects & Remove BitCryptor Ransomware
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | bclock.exe | 289b43d3c234585285a38b2a0f4db2e3 | 3 |
| 2. | %UserProfile%\sfile | ||
| 3. | %UserProfile%\filelist.locklst | ||
| 4. | %Temp%\wallpaper.jpg | ||
| 5. | %Temp%\BitCryptorFileList.txt |

