Ahihi Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 5 |
| First Seen: | January 15, 2019 |
| Last Seen: | January 16, 2019 |
| OS(es) Affected: | Windows |
The Ahihi Ransomware is an encryption Trojan that was identified by malware researchers on January 9th, 2019. The Ahihi Ransomware may compromise the users who open files attached to spam emails and install cracked shareware. The Ahihi Ransomware Trojan is reported to run as 'BangLuongThang02.exe' on the infected computers, and some computer security researchers may refer to the Trojan at hand as BangLuongThang02 Ransomware. There is no evidence to suggest there is a BangLuongThang01 Ransomware and the Ahihi Ransomware may be the first stable program to encrypt data on targeted devices successfully. The threat is built on the HiddenTear Ransomware platform and shares code with threats like the Sadly Ransomware and the Baliluware Ransomware. The Ahihi Ransomware is known to encrypt images, text, audio, video, PDFs, and eBooks, which are marked with the '.AHIHI' suffix. For example, 'Axwell Ingross-Sun Is Shining.mp3' is renamed to 'Axwell Ingross-Sun Is Shining.mp3.AHIHI.' The Ahihi Ransomware Trojan is reported to drop two messages on the desktop of the infected users. Both messages are displayed as 'README.txt,' but they offer different content. The slightly bigger version of 'README.txt' shows the following when loaded in Notepad:
'Your files have been encrypted. If you want to get your files back, please visit http://ripyon[.]me/decrypt and provide us the following information
Your computer name: [user-assigned device name]
Your username: [currently logged in account name]
Your token: [random characters]
CAUTION: DO NOT run this app again or your files will be encrypted permanently'
However, computer security experts warn that the Ahihi Ransomware does not connect to 'Command and Control' servers to report its activity and upload the decryption key. We should clarify that most encryption Trojans offer a way to decrypt the affected data in exchange for Bitcoins. A decryptor is said to be available at h[tt]p://ripyon[.]me/decrypt for the users compromised by the Ahihi Ransomware as indicated above. That is a lie, and the victims are unable to recover the encrypted content by navigating to h[tt]p://ripyon[.]me/decrypt. The smaller version of 'README.txt' supplied by the Ahihi Ransomware reveals the following:
'Your files have been encrypted. Unfortunately, you can't get your files back. We are sorry ^.^'
Malware researchers suspect that the Ahihi Ransomware may still be under development and the low infection ratio is interpreted as a test phase for the threat. The Ahihi Ransomware behaves as a simple data wiper at the time of writing. While the user's data remains on the local disks, it is unavailable and in a state that can be read by any program. The Ahihi Ransomware turns normal files into jumbled up lines of code, and you will need to use data backups to recover from potential attacks with this threat. AV scanners are known to mark the resources created by the Ahihi Ransomware as:
Artemis!9183C33C56B2
HEUR:Trojan-Ransom.MSIL.Encoder.gen
Malware@#3oxkjyv2drfpl
TR/Ransom.arobl
Trojan ( 00544cf41 )
Trojan-Ransom.FileCoder
Trojan.Generic.D1E050A4
Trojan.GenericKD.31477924
W32/Trojan.HXSQ-0239
Win32.Trojan.Agent.FI8LWG
Win32.Trojan.Fakedoc.Auto
Win32/Trojan.Ransom.d23
a variant of MSIL/Filecoder.QY
malicious.moderate.ml.score
malicious_confidence_90% (W)
SpyHunter Detects & Remove Ahihi Ransomware
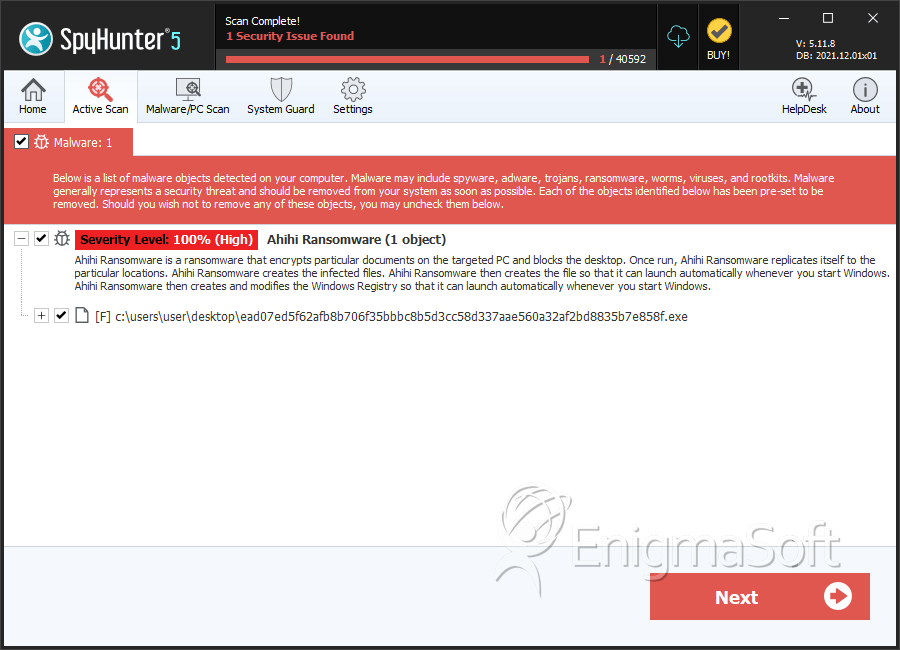
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ead07ed5f62afb8b706f35bbbc8b5d3cc58d337aae560a32af2bd8835b7e858f.exe | 9183c33c56b2315aa12967c1a6937b1c | 3 |
