Adame Ransomware
 Some highly skilled cyber crooks prefer to build and tailor unique malware and take great pride in this. Others, however, would rather take it easy and still cash in some profits, preferable with minimum effort involved. Such individuals like to base their malware creations on the code of already existing, well-established threats. This is the case with the creators of the Adame Ransomware. This file-encrypting Trojan is a variant of the infamous Phobos Ransomware.
Some highly skilled cyber crooks prefer to build and tailor unique malware and take great pride in this. Others, however, would rather take it easy and still cash in some profits, preferable with minimum effort involved. Such individuals like to base their malware creations on the code of already existing, well-established threats. This is the case with the creators of the Adame Ransomware. This file-encrypting Trojan is a variant of the infamous Phobos Ransomware.
Table of Contents
An Offshoot of the Phobos Ransomware
Upon close examination of its code, security researchers have now tied Adame's structure to that of the nasty Phobos ransomware family. However, the group of hackers behind the attacks has largely concealed its identity so that security analysts have no way of knowing if Adame is being utilized by the same criminal gangs as those behind Phobos. While Adame's code is similar to that of Phobos, Adame appends a different extension – all encrypted files are renamed using the following patterns:
- [File_name].id.[victim_ID][supportcrypt2019@cock.li].Adame
- [File_name].id.[victim_ID][ raynorzlol@tutanota.com].Adame
At this stage, there are no free decryptors available to reverse an Adame Ransomware encryption.
Infection Vectors
Identical to other Phobos Ransomware incarnations, the Adame Ransomware deploys a mix of phishing attacks based on spam email campaigns, web malvertising, and file-sharing platforms to spread far and wide among thousands of PC systems. In spam emails, the Adame Ransomware launches as soon as unsuspecting PC users agree to enable macros to view the content of the attached document, be it a spreadsheet, a text file, or a presentation file. Alternatively, the email may contain a URL to a software bundle containing the Adame Ransomware payload alongside the software advertised in the spam. Malvertising attempts, on the other hand, prompt site visitors to install a specific browser add-on to commence the ransomware assault. Last but not least, file sharing services provide plenty of room for further malware distribution, as well.
The Damage is Done
Once launched, Adame Ransomware performs a series of unstoppable actions. First, it collects whatever personal and system configuration details it comes across. Should it find any AV software, Adame creates a shield against it so as to evade detection. Finally, the ransomware modifies the system's registry and boot settings to make sure it launches during system startup every time. While earlier Adame Ransomware attacks mainly focused on encrypting user rather than system data, more recent reports suggest that Adame's developers have tweaked it a bit. As a result, Adame now spreads to all mapped drives when attacking network-connected PCs, encrypting both user and Windows system files alike. As soon as Adame has finished encrypting the data, it draws up a pair of documents – a pop-up HTML called Info.hta and an Info.txt Notepad file – on the victim's desktop.
Infection and Encryption
It is not yet clear what propagation method have the authors of the Adame Ransomware chosen to employ in the spreading of their creation. However, some speculate that the most common methods of propagating ransomware threats may be at play here, namely spam email campaigns, infected pirated applications, and bogus software updates. When the Adame Ransomware manages to worm its way into a system, it starts the attack by triggering a scan. This scan is meant to locate all the file which the Adame Ransomware was programmed to target. Once the scan is through, the Adame Ransomware will begin encrypting the targeted files. Upon encryption, the files have their names altered. The Adame Ransomware adds a '.id[
The Ransom Note
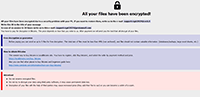
Next, the Adame Ransomware drops a ransom note named 'encrypted.hta.' The ransom note reads:
'All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail supportcrypt2019@cock.li
Write this ID in the title of your message 1E857D00-2275
In case of no answer in 24 hours write us to this e-mail:supportcrypt2019@protonmail.com
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 4Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
hxxps://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
hxxp://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.'
The authors of the Adame Ransomware do not mention a specific ransom fee. Instead, they claim that the price depends on how quickly the victim gets in touch with them, which sounds like a common social engineering technique. The attackers offer to decrypt up to five files free of charge provided that the total size does not exceed 4MB. This is usually done to prove to the victim that the attackers have a working decryption key. The authors of the Adame Ransomware make it clear that they want the ransom fee in the shape of Bitcoin which is a common request when dealing with cybercriminals because the cryptocurrency helps them protect their anonymity and avoid getting in trouble. The attackers give out two email addresses where they would like to be contacted – 'supportcrypt2019@cock.li,' and 'supportcrypt2019@protonmail.com.'
We advise you strongly to stay away from the authors of the Adame Ransomware, and from cyber crooks in general. Nothing good can come out of attempting to negotiate with such individuals. Instead, make sure to download and install a reputable antivirus software suite which will rid you of the Adame Ransomware and keep your system secure going forward.

