Zenis Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 10 |
| First Seen: | March 18, 2018 |
| Last Seen: | August 1, 2019 |
| OS(es) Affected: | Windows |
The Zenis Ransomware is an encryption ransomware Trojan that was first observed on March 14, 2018. The Zenis Ransomware is being used to attack medium and small businesses, as well as Web servers. The Zenis Ransomware behaves in a way similar to most encryption ransomware Trojans, using a strong encryption algorithm to make the victim's files inaccessible and then demanding the payment of a ransom in exchange for the decryption key needed to restore the affected files.
Table of Contents
The Zenis Ransomware can Compromise Countless Files on a Computer
Threats like the Zenis Ransomware use strong encryption methods to take the victim's files hostage. The following are examples of the file types typically compromised by attacks like the Zenis Ransomware:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
The Zenis Ransomware identifies the files encrypted by the attack by adding the file extension '.Zenis-<2_chars>' to the end of each affected file's name. The Zenis Ransomware will target files on all local hard drives, as well as files shared on a network. The Zenis Ransomware will deliver a ransom note in the form of an HTML file named 'Zenis-Instructions.html,' which is dropped on the infected computer's desktop. The full text of the Zenis Ransomware's ransom note reads:
'*** All your files has been encrypted ***
I am ZENIS. A mischievous boy who loves cryptography, hardware and programming. My world is full of unanswered questions and puzzles half and half, and I'm coming to discover a new world.
A world in digital space that you are supposed to play the role of my toys.
If you want to win in this game, you have to listen carefully to my instructions, otherwise you will be caught up in a one-step game and you will become the mam loser of the story.
My instructions are simple and clear. Then follow these steps:
1. Send this file (Zenis-Instructions.html) to my email with one your encrypted file less than 2 MB to trust to the game.
2. I decrypt your file for free and send for you.
3. If you confirm the correctness of the files, verify that the files are correct via email
4. Then receive the price of decrypting files
5. After you have deposited, please send me the payment details
6. After i confirm deposit, i send you the "Zenis Decryptor" along with "Private Key" to recovery all your files.
Now you can finish the game. You won the game, congratulations.
Please submit your request to both emails:
TheZenis@Tutanota.com
TheZems@MailFence.com
If you did not receive an email after six hours, submit your request to the following emails:
TheZenis@Protonmail. com
TheZenis@Mail2Tor.com (On the TOR network)
Warning: 3rd party and public programs. It may cause irreversible damage to your files And your files will be lost forever.'
Protecting Your Data from Threats Like the Zenis Ransomware
PC security researchers strongly advise computer users to refrain from contacting the people responsible for the Zenis Ransomware attack or following the instructions in the Zenis Ransomware's ransom note. Instead of doing this, computer users are advised to have file backups on the cloud or an external memory device. These backup copies can be used to restore the files compromised by the Zenis Ransomware attack.
SpyHunter Detects & Remove Zenis Ransomware
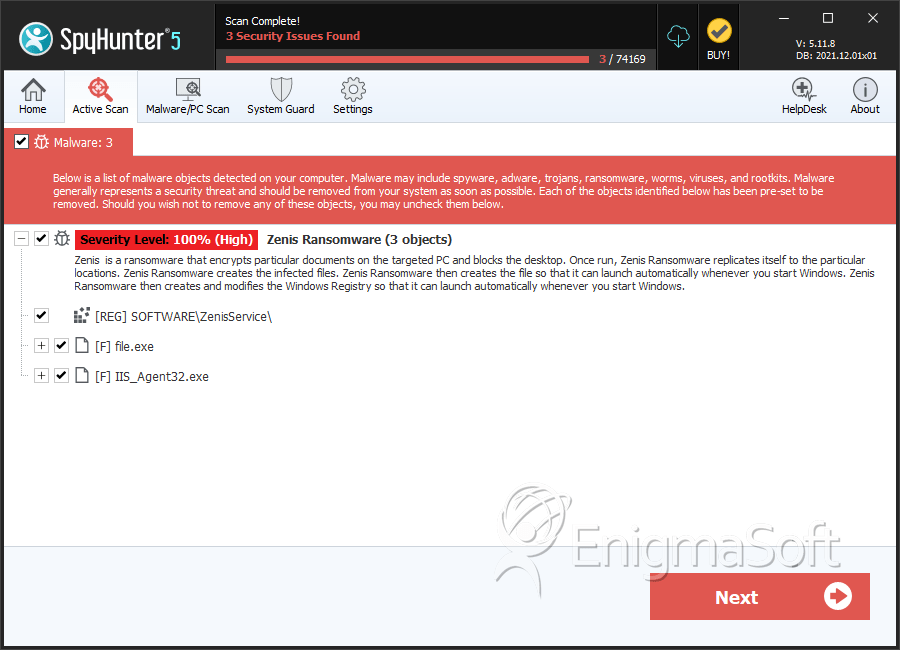
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 8cd8d46cd6c7e336d2baa2f78d8d0ab4 | 0 |
| 2. | IIS_Agent32.exe | 6957db401ce1f7edd1db9816b9430973 | 0 |

