Zayka Ransomware
The Zayka Ransomware is an encryption ransomware Trojan that uses a strong encryption algorithm to make the victim's files inaccessible. The Zayka Ransomware may spread through corrupted spam email attachments, which may often take the form of a bogus bill, invoice, or message from a social media service. When the recipient opens the attached file, the Zayka Ransomware will be downloaded and installed on the affected PC. Once the Zayka Ransomware is installed, it will encrypt the victim's data. The Zayka Ransomware does this to demand a ransom payment in exchange for the decryption key, necessary to recover the affected files.
Table of Contents
There are Numerous Versions of the Zayka Ransomware
The Zayka Ransomware will use a strong encryption algorithm to make the data inaccessible. The Zayka Ransomware will mark the encrypted files with a new file extension. Some versions of the Zayka Ransomware will mark the encrypted files with the file extension '.zayka' and others will use the file extension '.noob' to mark the affected files. In its attack, the Zayka Ransomware will target numerous file types, including the following:
.3gp, .7z, .apk, .avi, .bmp, .cdr, .cer, .chm, .conf, .css, .csv, .dat, .db, .dbf, .djvu, .dbx, .docm, ,doc, .epub, .docx .fb2, .flv, .gif, .gz, .iso .ibooks, .jpeg, .jpg, .key, .mdb .md2, .mdf, .mht, .mobi .mhtm, .mkv, .mov, .mp3, .mp4, .mpg .mpeg, .pict, .pdf, .pps, .pkg, .png, .ppt .pptx, .ppsx, .psd, .rar, .rtf, .scr, .swf, .sav, .tiff, .tif, .tbl, .torrent, .txt, .vsd, .wmv, .xls, .xlsx, .xps, .xml, .ckp, .zip, .java, .py, .asm, .c, .cpp, .cs, .js, .php, .dacpac, .rbw, .rb, .mrg, .dcx, .db3, .sql, .sqlite3, .sqlite, .sqlitedb, .psd, .psp, .pdb, .dxf, .dwg, .drw, .casb, .ccp, .cal, .cmx, .cr2.
Malware researchers have observed multiple versions of the Zayka Ransomware, most of which have been active since mid-July, 2017.
How the Con Artists may Profit Using the Zayka Ransomware
The people responsible for the Zayka Ransomware will demand that the victim contacts them via email to recover the affected files. The email address admin@zayka.pro has been associated with the Zayka Ransomware attack. Researchers advise computer users to refrain from contacting these people or paying the Zayka Ransomware ransom. The Zayka Ransomware ransom note is delivered in a text file named '_HELP_INSTRUCTION.TXT,' which is dropped to the infected computer's desktop and in multiple directories. The full text of the Zayka Ransomware ransom note reads as follows:
'[WHAT HAPPENED]
Your important files produced on this computer have been encrypted due a security problem If you want to restore them, write us to the e-mail: admin@zayka.pro
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
[FREE DECRYPTION AS GUARANTEE]
Before paying you can send to us up to 3 files for free decryption. Please note that files must NOT contain valuable information, and their total size must be less than 1Mb
[HOW TO OBTAIN BITCOINS]
The easiest way to buy bitcoin is LocalBitcoins site. You have to register, click Buy bitcoins and select the seller by payment method and price hxxps://localbitcoins.com/buy_bitcoins
[ATTENTION]
Do not rename encrypted files Do not try to decrypt your data using third party software, it may cause permanent data loss
NOOB'
Preventing the Zayka Ransomware Attacks
The best way to avoid the Zayka Ransomware attacks is to learn how to handle spam email messages safely, to prevent them from installing the Zayka Ransomware in the first place. The best protection against ransomware Trojans like the Zayka Ransomware is to have file backups. If computer users have the opportunity to recover their files quickly from a backup copy, then the people responsible for the Zayka Ransomware attack lose any leverage they have over the victim that would enable them to demand a ransom. The use of a reliable, fully updated anti-malware application is also highly recommended as a way to prevent the Zayka Ransomware and other threat attacks.
SpyHunter Detects & Remove Zayka Ransomware
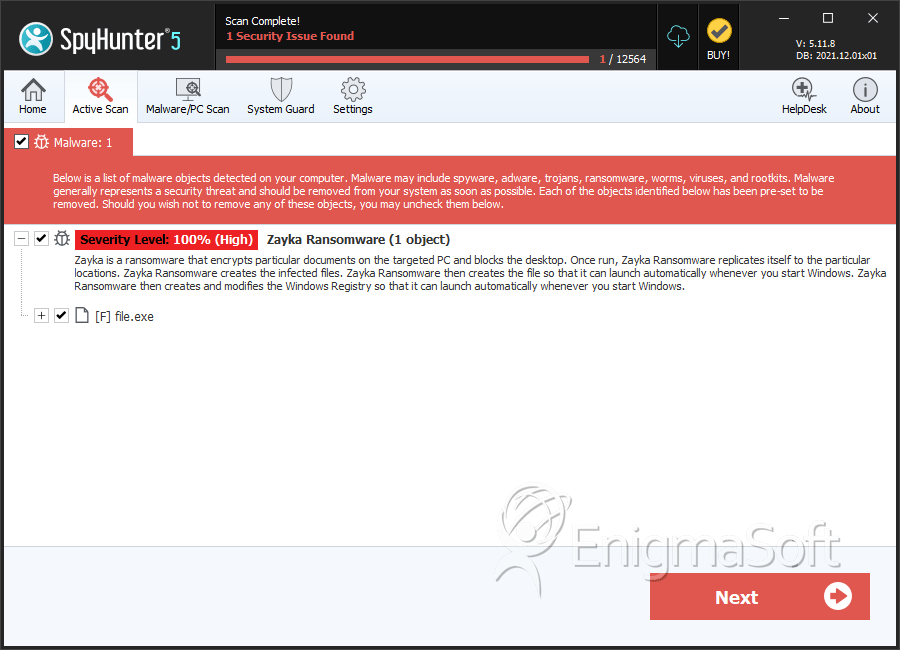
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 1c41143c85917d61537c91774ddf95f0 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.