Yyto Ransomware
The Yyto Ransomware is a ransomware Trojan that is used to extort computer users. The Yyto Ransomware carries out a typical ransomware attack, encrypting the victim's data and demanding the payment of a sum in exchange for the decryption key that is necessary to recover the affected data. The files that become encrypted in the Yyto Ransomware attack will have the file extension 'read_to_txt_file.yyto' added to tend of each file's name. This extension refers the victim to a text file named 'help_to_decrypt.txt' that is created on the infected computer's desktop and in each directory where the Yyto Ransomware encrypted content. The text file contains the Yyto Ransomware's ransom note, which demands a ransom payment from the victim. This is an attack method that PC security researchers have observed countless times, used by numerous ransomware Trojans in the wild to infect victims' computers and threaten them so that they'll pay large amounts of money.
Table of Contents
To Recover the Files Encrypted by the Yyto Ransomware PC Users Need the Decryption Key
The Yyto Ransomware uses a ransom note that alerts the victim of the attack and tells them to contact the con artists via email using TOR, which allows computer users to become anonymous online. After the victims contact the con artists, they will receive further instructions. Unfortunately, the Yyto Ransomware uses a strong encryption method. Once the files have been encrypted, it is currently not possible to decrypt the files. Because of this, the best protection against ransomware attacks like the Yyto Ransomware is to have file backups, which allow computer users to restore the affected files without having to pay the ransom.
How Con Artists may Profit from the Yyto Ransomware Infections
Victims of the Yyto Ransomware attack are not told what the amount to pay is until they contact the con artists. However, most ransomware Trojans demand a payment between $500 USD and $1500 USD to be paid using BitCoin. PC security analysts strongly advise computer users, however, to refrain from contacting the con artists or carrying out any ransom payment. Paying these kinds of ransoms does not guarantee that you will recover the affected files and, furthermore, it allows the people responsible for the Yyto Ransomware to continue carrying out attacks and producing threat. Even if the files are decrypted after paying, con artists will frequently re-infect the victim's computer shortly after to continue demanding ransom payments. The following is the ransom note used in the Yyto Ransomware attack:
'If you don't have a email in TOR network:
1) Download and install the browser for the TOR network: https://www.torproject.org/download/download-easy.html
2) Launch browser and go to the link (create email in TOR network): torbox3uiot6wchz.onion
3) Write on email: cutterswish@torbox3uiot6wchz.onion
4) Wait for a response.
DON'T WRITE FROM NOT TOR EMAIL. MESSAGES WILL NOT BE RECEIVED AND YOU WILL NOT RECEIVE AN UNLOCK KEY.
Your personal key:
8f51a85f140*****'
Dealing with the Yyto Ransomware and Similar Ransomware Attacks
Encryption ransomware Trojans like the Yyto Ransomware are becoming increasingly common today. This is why computer users should take steps to protect their computers from these kinds of attacks. The most effective way to protect your files from the Yyto Ransomware infection is to safeguard your data by having backup copies of your files on an external memory device or on the cloud (not synchronized with your computer to prevent the backups themselves from becoming encrypted as well). Having backup copies allows computer users to recover from the Yyto Ransomware attacks easily by simply recovering the affected files from the backup copy. A reliable security program that is fully up to date can help computer users remove the Yyto Ransomware Trojan itself as well as intercept this ransomware Trojan before it carries out its attack. Finally, since the Yyto Ransomware and similar attacks are frequently distributed through the use of corrupted email spam attachments or other online tactics, learning how to go online safely and handle this kind of content is essential.
SpyHunter Detects & Remove Yyto Ransomware
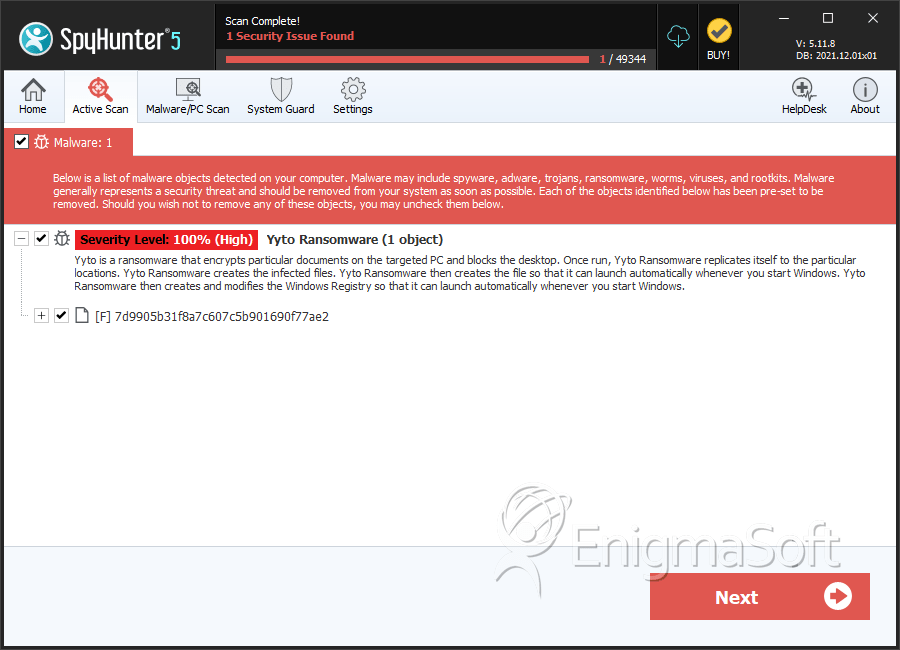
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 7d9905b31f8a7c607c5b901690f77ae2 | 7d9905b31f8a7c607c5b901690f77ae2 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.