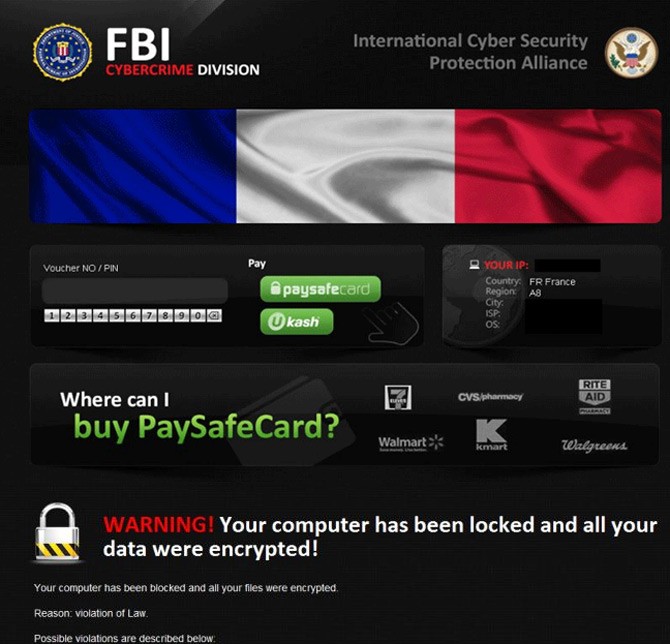
'Your Computer Blocked, Data Encrypted' Virus (Ransomware) Image
The so-called 'Your Computer Blocked, Data Encrypted' Virus is not actually a virus at all but a ransomware Trojan. Trojans cannot spread on their own or corrupt files like viruses; rather, they rely on social engineering or other malware to spread from one computer to another. The 'Your Computer Blocked, Data Encrypted' Virus is one of the many variants of the infamous Reveton ransomware Trojan. There are dozens of variants of this malware infection, typically infecting computers specific to a country or region. The 'Your Computer Blocked, Data Encrypted' Virus itself is a variant of the Reveton Trojan that targets computers located in the United States. To carry out its attack, the 'Your Computer Blocked, Data Encrypted' Virus displays a fake message from the FBI (Federal Bureau of Investigation of the United States) and demands payment of two hundred dollars via MoneyPak, an online payment service with an American customer base.
Like other Police Ransomware Trojans, the 'Your Computer Blocked, Data Encrypted' Virus carries out a version of a well known online scam. Basically, the 'Your Computer Blocked, Data Encrypted' Virus makes the victim believe that the infected computer was blocked by the FBI due to illegal activities. To do this, the 'Your Computer Blocked, Data Encrypted' Virus prevents the user from accessing the PC and displays a message that claims that the FBI blocked the infected computer and encrypted its data. It is important to note that this is entirely false; the 'Your Computer Blocked, Data Encrypted' Virus has no connection to the FBI, and the 'Your Computer Blocked, Data Encrypted' Virus does not have the ability to encrypt data. Rather, the 'Your Computer Blocked, Data Encrypted' Virus makes changes to the infected computer' settings that prevent the victim from bypassing the 'Your Computer Blocked, Data Encrypted' Virus message or access their Desktop or files.
The main difficulty in dealing with a 'Your Computer Blocked, Data Encrypted' Virus infection is bypassing its ransom message so it will be possible to access the infected machine. The best way to achieve this is using Safe Mode or other alternate start-up methods (such as using an external memory device.) Once the 'Your Computer Blocked, Data Encrypted' Virus message has been bypassed, a reliable anti-malware tool that has been properly updated should be able to remove this malware infection completely.
Messages
The following messages associated with 'Your Computer Blocked, Data Encrypted' Virus (Ransomware) were found:
FBI Cybercrime Division
International Cyber Security Protection Alliance
WARNING! Your computer has been blocked and all your data were encrypted
Reason: violation of Law.
Possible violations are described below:
Title 17- COPYRIGHTS
Chapter 10, Subchapter B – COPYING CONTROLS
(a) Prohibition on Importation, Manufacture, and Distribution.— No person shall import, manufacture, or distribute any digital audio recording device or digital audio interface device that does not conform to—
(1) the Serial Copy Management System;
(2) a system that has the same functional characteristics as the Serial Copy Management System and requires that copyright and generation status information be accurately sent, received, and acted upon between devices using the system’s method of serial copying regulation and devices using the Serial Copy Management System; or
(3) any other system certified by the Secretary of Commerce as prohibiting unauthorised serial copying.
Title 18 – CRIMES AND CRIMINAL PROCEDURE Title 18, Part I Chapter 117 § 2427
Inclusion of offences relating to child pornography in definition of sexual activity for which any person can be charged with a criminal offence.
Title 18 Part I Chapter 110, § 2258C Inclusion of offences relating to child pornography in definition of sexual activity for which any person can be charged with a criminal offence.
a) Elements.—
(1) In general— The National Center for Missing and Exploited Children may provide elements relating to any apparent child pornography image of an identified child to an electronic communication service provider or a remote computing service provider for the sole and exclusive purpose of permitting that electronic communication service provider or remote computing service provider to stop the further transmission of images.
(2) Inclusions.— The elements authorised under paragraph (1) may include hash values or other unique identifiers associated with a specific image, Internet location of images, and other technological elements that can be used to identify and stop the transmission of child pornography.
(3) Exclusion— The elements authorised under paragraph (1) may not include the actual images.
(b) Use by Electronic Communication Service Providers and Remote Computing Service Providers.— Any electronic communication service provider or remote computing service provider that receives elements relating to any apparent child pornography image of an identified child from the National Center for Missing and Exploited Children under this section may use such information only for the purposes described in this section, provided that such use shall not relieve that electronic communication service provider or remote computing service provider from its reporting obligations under section 2258A.
(c) Limitations.— Nothing in subsections [1] (a) or (b) requires electronic communication service providers or remote computing service providers receiving elements relating to any apparent child pornography image of an identified child from the National Center for Missing and Exploited Children to use the elements to stop the further transmission of the images.
(d) Provision of Elements to Law Enforcement.— The National Center for Missing and Exploited Children shall make available to Federal. State, and local law enforcement involved in the investigation of child pornography crimes elements, including hash values, relating to any apparent child pornography image of an identified child reported to the National Center for Missing and Exploited Children.
(e) Use by Law Enforcement.— Any Federal, State, or local law enforcement agency that receives elements relating to any apparent child pornography image of an identified child from the National Center for Missing and Exploited Children under section [1] (d) may use such elements only in the performance of the official duties of that agency to investigate child pornography crimes.
Title 18 Part I Chapter 110 § 22524
§ 2252A – Certain activities relating to material constituting or containing child pornography
Title 26 Subtitle F Chapter 78 > Subchapter A § 7612 Special procedures for summonses for computer software
To unlock your computer you must pay a penalty within 24 hours and input voucher axle to a form below. It will take up to 24 hours to check voucher code and decrypt your data. |




Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.