Worm.Win32.Carrier.gv
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 60 % (Medium) |
| Infected Computers: | 1,318 |
| First Seen: | July 24, 2009 |
| Last Seen: | December 9, 2025 |
| OS(es) Affected: | Windows |
Worm.Win32.Carrier.gv is a network-aware worm which spreads using existing networks. Worm.Win32.Carrier.gv often requests other malicious files from the Internet to download them on the targeted system. Worm.Win32.Carrier.gv may send out email messages with a built-in SMTP client engine which sends emails to a recipient mail server. Worm.Win32.Carrier.gv should be removed using effective anti-malware software immediately.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| AVG | Generic25.CJCV |
| Fortinet | W32/BDoor.CEP!tr.bdr |
| AhnLab-V3 | Trojan/Win32.ADH |
| AntiVir | BDS/Bifrose.A.394 |
| Kaspersky | Trojan.Win32.Midgare.bbsz |
| ClamAV | Trojan.Midgare-167 |
| CAT-QuickHeal | Trojan.Midgare.bbsz |
| Panda | Trj/Thed.M |
| AVG | Generic5_c.BUVP |
| TrendMicro | TROJ_SPNR.11I612 |
| F-Secure | Gen:Variant.Barys.1607 |
| eSafe | Win32.GenVariant.Kaz |
| McAfee | BackDoor-FACW!FEA05B1E642B |
| AVG | Generic5_c.AUMF |
| AhnLab-V3 | Backdoor/Win32.Buzy |
SpyHunter Detects & Remove Worm.Win32.Carrier.gv
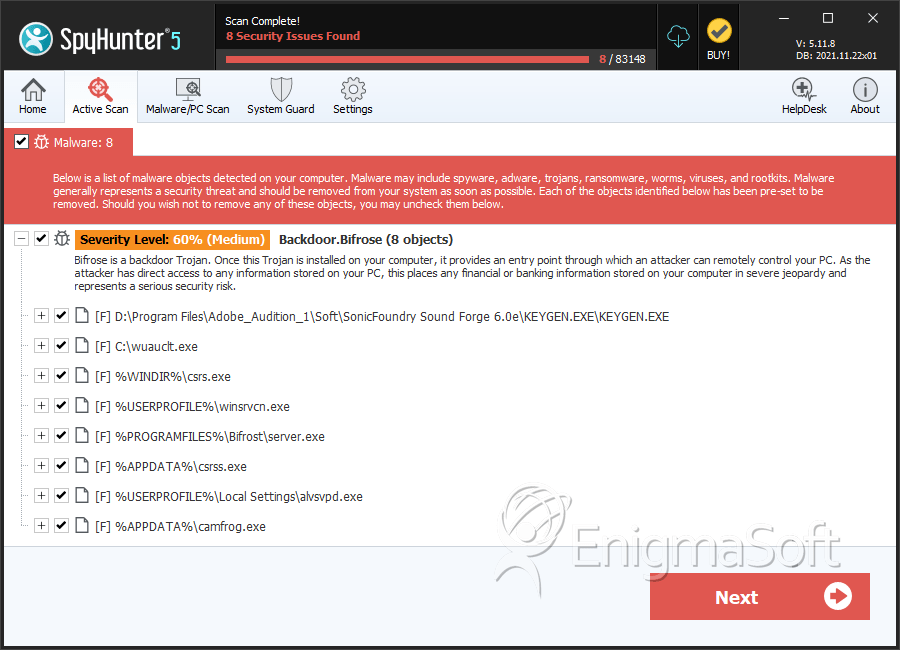
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | KEYGEN.EXE | c78823c750512ab280b62ec17ee2173a | 565 |
| 2. | wuauclt.exe | 2e2d0c602a60fba0ee1f3c68d2532237 | 76 |
| 3. | csrs.exe | a94dc5a0361bb54f4c40abf404441379 | 34 |
| 4. | update.exe | 4b63963bcc580f48f5a40bda656ebd51 | 6 |
| 5. | winsrvcn.exe | f75a8c506ed70d465e15065146843385 | 4 |
| 6. | server.exe | 1bf5e02e439c6cf09c220d5710b46ad5 | 4 |
| 7. | csrss.exe | b6c30f087bb3cbc38c7abb3e2ca4eaf2 | 2 |
| 8. | alvsvpd.exe | 61e2355a9bc4d852c06571b51f084448 | 2 |
| 9. | camfrog.exe | c8b0f1482d5026134d4be7f3b906b21f | 1 |
| 10. | system32.exe | e83b9b6a0f906ad6564afc890ea5c6bd | 1 |
| 11. | file[1].exe | 9b1b8011f18ac6b95c87cc5c115514e7 | 0 |
| 12. | ffx.exe | 905d88c67659fe04a35ec2c0f86c4ed0 | 0 |
| 13. | winsystem.exe | 4920b9bcc50cac48ce4cb3f4ce4c527e | 0 |
| 14. | svchost.exe | 624f45f8ef3f192e8eb09a529fe0e3fe | 0 |
| 15. | spoolsv.exe | c665a55e56966c44171d9c8900fbb529 | 0 |
| 16. | ccdrive32.exe | 39f2c3805d88cf76c5d79c54c1e37349 | 0 |
| 17. | rundll32.exe | 8d08b75195561ed02caa6f0abb3b4fd8 | 0 |
| 18. | msn.exe | 2afb4ee104bc1d0be383845845a9b511 | 0 |
| 19. | H2sfasH.exe | 31eb4ff720d93075a2fcbb203c590ff2 | 0 |
| 20. | msvmcls64.exe | ae7fa2384864f34947ac24f45ca9e4bf | 0 |
| 21. | win23.exe | f2e2909a1aa1ba25357768061979b621 | 0 |
| 22. | file.exe | d948009c57aa4ef2d0e1944b561c12ba | 0 |
Registry Details
Analysis Report
General information
| Family Name: | Backdoor.Bifrose |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
8b6450f6d43a9e848f6d33b06b3411c3
SHA1:
1f677ad0abcfe8f0c4c694c7732c7f95a94d08f6
SHA256:
8150596BCBBE51058C6988D0278A1AB14DC14F02700639E771D420726A81BA9A
File Size:
3.17 MB, 3166208 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have relocations information
- File doesn't have security information
- File has exports table
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
Show More
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Comments | Modified by an unpaid evaluation copy of Resource Tuner 2 (www.heaventools.com) |
| Company Name | Hanbitsoft corp. |
| File Description | Tantra Client |
| File Version | 6, 9, 0, 6 |
| Internal Name | HTLaunch |
| Legal Copyright | Copyright (c) - 2003 Hanbitsoft corp. |
| Original Filename | HTLaunch.exe |
| Product Name | Tantra Client |
| Product Version | 1, 0, 0, 1 |
File Traits
- 00 section
- 2+ executable sections
- HighEntropy
- RT
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 4 |
|---|---|
| Potentially Malicious Blocks: | 0 |
| Whitelisted Blocks: | 3 |
| Unknown Blocks: | 1 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- BadJoke.LMG
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Other Suspicious |
|
| User Data Access |
|
