Worm: Win32/Bagsak.A
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 50 % (Medium) |
| Infected Computers: | 103 |
| First Seen: | April 18, 2016 |
| Last Seen: | September 18, 2021 |
| OS(es) Affected: | Windows |
The Worm: Win32/Bagsak family of cyber threats is comprised of computer worms that are designed to spread vertically and horizontally on an infected network. The Bagsak Worm may copy itself to remote servers that share a LAN and VPN connection. Additionally, the Bagsak Worm may disable built-in defenses and acquire elevated system privileges by editing the Windows Registry. The Bagsak Worm is a stand-alone cyber threat that does not require a continuous communication with its 'Command and Control' servers to achieve its goals. The Worm: Win32/Bagsak.A malware is deployed as a .COM file that may look like a Microsoft PowerPoint presentation. The Worm: Win32/Bagsak.A malware may be found attached to spam emails that are crafted to appear as reports from PayPal, Amazon and Facebook. The Bagsak malware may use files like IMJKAPI.DLL, mqsvc.exe, and rundll32.com, and features a digital certificate that is forged to resemble the public key used by Microsoft Corp.
The variants of the Worm: Win32/Bagsak malware may be detected under the alias Worm.Win32.WBNA and you should not overlook security alerts that involve Bagsak. The Bagsak Worm may make modifications to the file structure of the system root folder to ensure its operations and register itself as a Windows native file and evade detection. The Bagsak cyber threat may have the capability to gather information from the infected machine silently. The Bagsak Worm may be seen in campaigns launched at international conglomerates and government officials across the globe. The Bagsak malware may record keyboard input, data flow in industrial networks and encrypted communications. As stated above, the Bagsak Worm may operate independently and initiate transmissions at set intervals of time. The variants of the Bagsak malware are difficult to detect given that they may bypass most code signing scans successfully. You need to install a comprehensive anti-malware suite to upgrade your cyber defenses and maintain multi-layered runtime shield to prevent the Bagsak Worm from infiltrating your PC network and keep it clean.
Table of Contents
SpyHunter Detects & Remove Worm: Win32/Bagsak.A
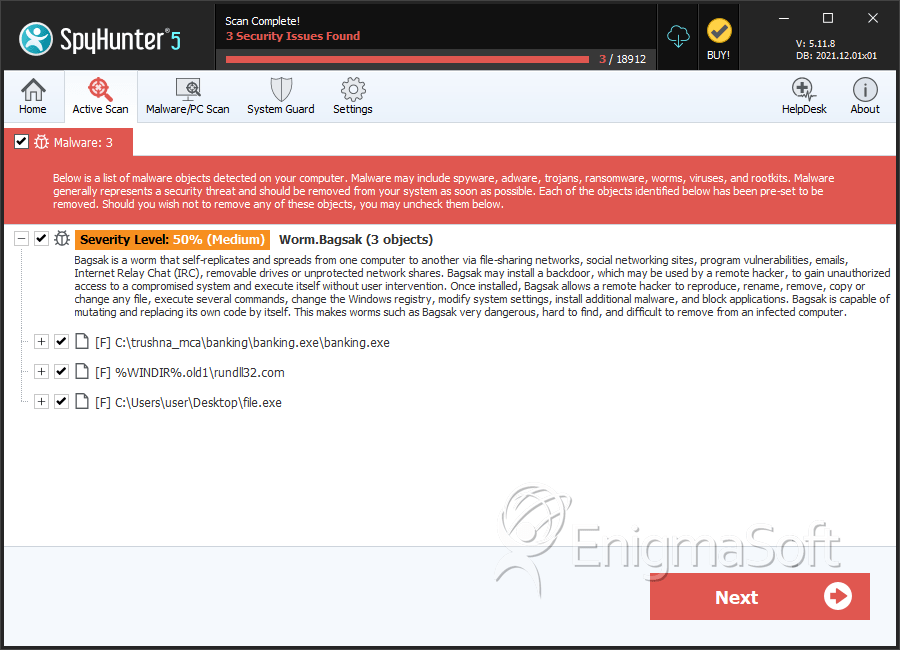
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | banking.exe | f5f591c4a88dceee6eee7f3b3c148613 | 24 |
| 2. | rundll32.com | cfc69c593ed25db076d6757a2df48c3b | 18 |
| 3. | rundll32.com | 29ec6a897b593257d51bfea6c6b7acea | 11 |
| 4. | rundll32.com | adadae70446a5f943d6e4841b4b29b0c | 9 |
| 5. | rundll32.com | b672153d8a0b0e31d4c51513b9748f43 | 6 |
| 6. | rundll32.com | 548d5fe26ae047109a2bba4db48eeda6 | 4 |
| 7. | rundll32.com | 47010127082bf2d15095da6900939804 | 3 |
| 8. | rundll32.com | de251bc7080233ccc2d54128872b83a3 | 3 |
| 9. | rundll32.com | c388a020000d16fab6de2398434eaa56 | 3 |
| 10. | rundll32.com | 908981ac63d5099d370062cc57a1b07f | 2 |
| 11. | rundll32.com | f40133163c4a656a5c22a0103bdf5884 | 1 |
| 12. | rundll32.com | 17a67f40659e74d52808afb21bd66fdc | 1 |
| 13. | rundll32.com | 010b804b98c47ba7bffdc70d2028378f | 1 |
| 14. | rundll32.com | 610754af4c82b92db3b88dfc019ffbf2 | 1 |
| 15. | file.exe | 7af65c07e474e3fa745f17e91953124b | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.