WORM_KOLAB.SMQX
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 50 % (Medium) |
| Infected Computers: | 1 |
| First Seen: | September 26, 2011 |
| OS(es) Affected: | Windows |
WORM_KOLAB.SMQX is a malicious computer worm, which circulates by replicating via removable drives, flash drives and instant messaging applications. The copies of WORM_KOLAB.SMQX use the names of the folders located on the said drives for their file names. WORM_KOLAB.SMQX propagates from one computer to another as a file dropped by other malware infections or as a file downloaded unknowingly by web users when visiting dubious websites. WORM_KOLAB.SMQX adds its registry entries to run automatically each time your Windows boots up. WORM_KOLAB.SMQX can connect to Internet Relay Chat (IRC) servers and fulfill instructions given from remote attackers to corrupt the affected computer system. Uninstall WORM_KOLAB.SMQX as early as possible.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Panda | W32/Dorkbot.A.worm |
| AVG | Injector.EQT |
| Fortinet | W32/Ruskill.AFP!tr.bdr |
| Ikarus | Gen.Trojan.Heur |
| AhnLab-V3 | Trojan/Win32.FakeAV |
| Antiy-AVL | Backdoor/Win32.Ruskill.gen |
| AntiVir | TR/Crypt.XPACK.Gen3 |
| Comodo | UnclassifiedMalware |
| BitDefender | Trojan.Generic.KDV.295922 |
| Kaspersky | Backdoor.Win32.Ruskill.afp |
| eSafe | Win32.TRCrypt.XPACK |
| Avast | Win32:Kryptik-DVB [Trj] |
| Symantec | Trojan.Gen.2 |
| NOD32 | a variant of Win32/Injector.HXM |
| McAfee | Generic BackDoor!dlp |
SpyHunter Detects & Remove WORM_KOLAB.SMQX
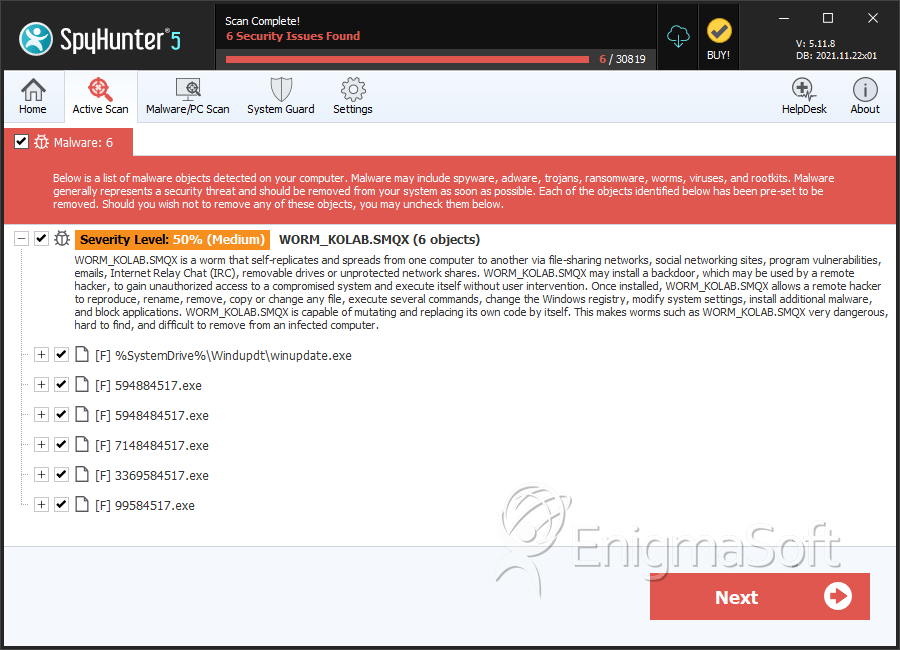
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | winupdate.exe | f6c1a5f929fbcc99f45862e86ae6d916 | 1 |
| 2. | %User Temp%\{RANDOM CHARACTERS}.exe | ||
| 3. | %Application Data%\E-73473-3674-74335 | ||
| 4. | 594884517.exe | 5a52d6dca7abeecf6967c8bfaf4a3dc6 | 0 |
| 5. | 5948484517.exe | 1c3168ca0ddaa02557b0da7ebf254d41 | 0 |
| 6. | 7148484517.exe | eb21d02faab39472c98598638634b10c | 0 |
| 7. | 3369584517.exe | 3480086d167fce1ff67e86cd9fb02be3 | 0 |
| 8. | 99584517.exe | 9f96305404f22fcccbf2d9cda5283f66 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.