Worm.Autorun
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 2,801 |
| Threat Level: | 90 % (High) |
| Infected Computers: | 23,898 |
| First Seen: | July 24, 2009 |
| Last Seen: | December 12, 2025 |
| OS(es) Affected: | Windows |
Worm.Autorun is a family of worms that spread through systems by altering the present autorun.inf file on any removable media sources, such as USB drives, DVDs and the like. It is made with the intent to infect any system where such media sources are connected.
Autorun worms are often distributed through the use of executable files. The file may be a copy created in a previous worm infection or it may have been dropped on a device or the computer by exploit kits or trojans. The executables are often saved to the root directory on a computer or a disk drive, USB flash drives, mobile devices and more.
Table of Contents
Creation of copies and infection spread
When the worm file is initially launched, it makes a copy of itself onto one or several drives on the device or computer it's present on. Some of the Autorun worms may also create copies of themselves over a shared network. As this keeps going on, the worm also creates an autorun.inf file in the root directory of any affected drive. The .inf file has the name and the location of the worm copy, and it also happens to be responsible for making more copies, even if the original file of the worm is never started up again.
If the affected drive or device gets opened, such as File Explorer, the .inf file is run automatically, which activates the worm copy, which makes more copies, repeating the cycle on and on again.
If the drive is a removable USB flash drive, then every time it is inserted in a clean computer or a device, that .inf file will launch the worm copy stored inside it, spread the infection onto the newly connected device or computer.
Autorun worms may also have a malicious payload that is used to distribute harmful software such as trojans and backdoors.
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| Panda | Trj/Passtealer.FZ |
| AVG | Worm/Delf.GOD |
| Fortinet | W32/AutoRun.LW!worm |
| AhnLab-V3 | Win-Trojan/Autorun.59392.B |
| Sophos | W32/SillyFDC-BP |
| AntiVir | TR/Agent.AGBR |
| Comodo | Worm.Win32.AutoRun.EY |
| BitDefender | Trojan.Agent.AGBR |
| Kaspersky | Worm.Win32.AutoRun.lw |
| ClamAV | Trojan.Autorun-220 |
| Avast | Win32:AutoRun-QM [Wrm] |
| F-Prot | W32/Worm.AXFI |
| NOD32 | Win32/AutoRun.EY |
| McAfee | W32/Autorun.worm.r |
| Panda | W32/Nuj.A.worm |
SpyHunter Detects & Remove Worm.Autorun
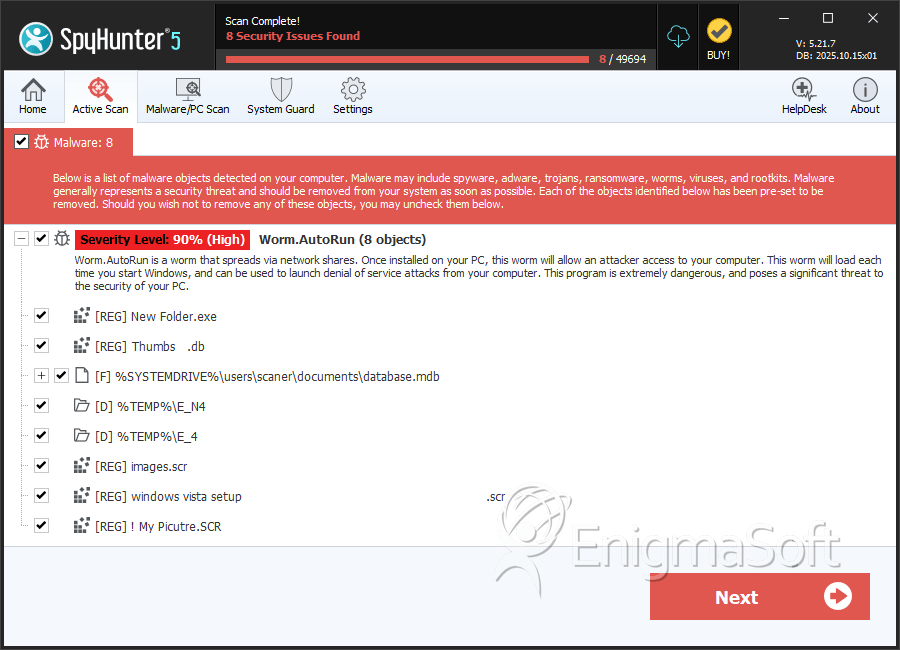
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | database.mdb | 0a456ffff1d3fd522457c187ebcf41e4 | 2,705 |
| 2. | Adobe .scr | 4798cecc36d9952ba73633c54f3468b6 | 33 |
| 3. | Alwil Software .scr | 877f32a2b7b611f4080f1ee1380c71ac | 32 |
| 4. | Kiray.exe | f22ae972aee081ec86faa30e73d9675f | 21 |
| 5. | kop .scr | 7a0b5674ec20b6455559ca1d70dc2c55 | 19 |
| 6. | Prolin.exe | 65eeb8a0fce412d7f236f8348357d1c0 | 19 |
| 7. | NAKEDWIF.EXE | da9dba70de70dc43d6535f2975cec68d | 17 |
| 8. | SgiBioSrv .scr | 13ae3be4d7ec63dc38b3e6dc94a20abc | 6 |
| 9. | musallat.exe | a66f4b8186ecb503170c8ffd7977cb93 | 5 |
| 10. | super cerame .scr | bafbe25d1051c4a2f42e2262538de8f5 | 3 |
| 11. | toil.exe | ec8a1659c7d67a3859d515130bae3c4c | 3 |
| 12. | ADORER AVEC NOUS .scr | 5421ad3e8fbe0f8a04e617224f4abbf0 | 2 |
| 13. | VirusShare_2ca27551e11bf054f7c5cb98eac11408 | 2ca27551e11bf054f7c5cb98eac11408 | 2 |
| 14. | magistr.exe | a8cfcfa06303168b5f94e0696882a3c8 | 2 |
| 15. | VirusShare_0eb3cca824da735aa040caa012450748 | 0eb3cca824da735aa040caa012450748 | 2 |
| 16. | InstallMate .scr | 9b85d177c939421dc4a4e7f3bee729a2 | 1 |
| 17. | LAPTOP DATA .scr | 349752fc724199059603073bacfa429e | 1 |
| 18. | FOUND.039 .scr | e64e104bd27c0e0c7eb7d1b528f45b06 | 1 |
| 19. | doc01 .scr | d3dd17b567bdc7e7daa1ab36495d1bcb | 1 |
| 20. | عععع .scr | 7ab70d44ec07d076ea7dc7e8aff6a011 | 1 |
| 21. | Application Data .scr | 3c59bd20783744e16f749127055b52de | 1 |
| 22. | stator.exe | 52a3b8dda9c9f1c87b77f9aa01e6777e | 1 |
| 23. | fintas.exe | 42b1eb959ce76f9013e8e9922305ca29 | 1 |
| 24. | paukor.exe | 7e20359dfc0b2291487f1a45c4471988 | 1 |
| 25. | VirusShare_15c2f7ece2c6647c5e45608e39b08e34 | 15c2f7ece2c6647c5e45608e39b08e34 | 1 |
| 26. | gip3.exe | 644814aa418a3ae1716daa7fb484a539 | 1 |
| 27. | naked.exe | da4371bc7347d3633c0eea308c9cb444 | 0 |
| 28. | gip1.exe | dbea1cc228c9353851e06599788a5a5e | 0 |
Registry Details
Directories
Worm.Autorun may create the following directory or directories:
| %PROGRAMFILES%\windows common files |
| %PROGRAMFILES(x86)%\windows common files |
| %TEMP%\E_4 |
| %TEMP%\E_N4 |
Analysis Report
General information
| Family Name: | Worm.AutoRun |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
1111624b088f25001bea55e62886a3e8
SHA1:
4c6d65ff66e94c23d7ec6f4edf14fc384cd5a345
SHA256:
0755BDA1CEAC9CFB2A09AF57756AF94B77EFC8AC32712E647EBD075E4F4B4CFE
File Size:
40.96 KB, 40960 bytes
|
|
MD5:
8167eb5715f41d3692faa51aac9694b2
SHA1:
5c966d2080173ab96fcca5be117bbd3d2b34cc91
SHA256:
32D5E07CB6EB1D5D1F2E117521E5DABE97EE73CB87B1E986322805DFA6A7826F
File Size:
23.55 KB, 23552 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File is 32-bit executable
- File is 64-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
Show More
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Arguments | xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
| Comments | Win64 (x64) Unicode Lib Rel |
| Company Name | xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
| xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx | |
| File Description | xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
| File Version | xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
| Internal Name | TSULoader |
| Legal Copyright | xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
| Original Filename | xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
| Package Code | {00000000-0000-0000-0000-000000000000} |
| Product Code | {00000000-0000-0000-0000-000000000000} |
| Product Name | xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
| Product Version | xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
| Special Build | xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
| Web Site | xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
File Traits
- Installer Manifest
- No Version Info
- x64
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 21 |
|---|---|
| Potentially Malicious Blocks: | 0 |
| Whitelisted Blocks: | 3 |
| Unknown Blocks: | 18 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Syscall Use |
|
| Anti Debug |
|
