WininiCrypt Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 15 |
| First Seen: | August 11, 2017 |
| Last Seen: | September 11, 2021 |
| OS(es) Affected: | Windows |
The WininiCrypt Ransomware is an encryption ransomware Trojan. The WininiCrypt Ransomware is mainly being distributed through the use of spam email attachments. The WininiCrypt Ransomware was first observed in the wild on August 10, 2017. The WininiCrypt Ransomware is programmed using the Microsoft .NET Framework. This allows the WininiCrypt Ransomware to be delivered in a package smaller than usual and to avoid certain detection tools by commonly used anti-virus programs. The WininiCrypt Ransomware is being used to attack both individual computer users and small business networks and servers. There is very little to differentiate the WininiCrypt Ransomware from the countless other encryption ransomware Trojans that are active currently. However, the WininiCrypt Ransomware does not seem to be based on any specific ransomware Trojan's code or to belong to a large threat family.
Table of Contents
Windows Users should be Aware of the WininiCrypt Ransomware
Due to its use of .NET Framework, the WininiCrypt Ransomware is especially effective in attacking the latest versions of the Windows operating system. In its attack, the WininiCrypt Ransomware will scan the victim's computer for certain file types associated with commonly used software, including Microsoft Office, media players, etc. the WininiCrypt Ransomware will use the AES encryption to make the victim's files unreachable, connecting with its Command and Control server to relay the decryption key, encrypt it using additional encryption, and make the victim's files inaccessible. The WininiCrypt Ransomware's Command and Control server, unlike many other ransomware Trojans, is not hosted on the Dark Web. The files encrypted by the WininiCrypt Ransomware will be marked with the addition of the file extension '.[cho.dambler@yandex.com],' added to the end of each affected file. The email address included in this file extension is the one used by the con artists to contact the victims and demand a ransom payment.
How the WininiCrypt Ransomware Tries to Extort Its Victims
The WininiCrypt Ransomware will drop a ransom note named 'HOW_TO_BACK_FILES.html,' which is displayed by the victim's default web browser after encrypting the victim's files. This HTML file contains the following text:
'All your files have been encrypted!
Your personal ID [RANDOM CHARCTERS]
All your files have been encrypted due to a security problem with your PC.
If you want to restore them, write us to the e-mail: cho.dambler@yandex.com
How to obtain Bitcoins
• The easiest way to by bitcoins is LocalBitcoins site. You have to register, click By bitcoins', and select the seller by payment method and price.
• hxxps://localbitcoins.com/buv bitcoins
• Also you can find other places to buy Bitcoins and beginners guide here:
• hxxp://mvw.coindesk.com/information/how-on-i-buv-bitcoins/
Free decryption as guarantee • Before paying you can send to us up to 1 No for No decryption.Please note that NO must NOT contain valuable information and their total size must be lot than 5Mb
Attention!
• Do not rename encrypted files. • Do not try to decrypt your data using third party software, it may cause permanent data loss.
• Decryption of your No with the help of third pates may cause increased price (they add their fee to our) or you can become a victim of a scam.'
PC security researchers counsel computer users to abstain from following the instructions in the WininiCrypt Ransomware's ransom note, despite that it is not possible to decrypt files that are compromised by the WininiCrypt Ransomware attack currently. Paying the WininiCrypt Ransomware ransom will rarely result in the return of the affected files and allows the people behind this attack to continue developing and creating threats like the WininiCrypt Ransomware in the future. Having file backups on independent devices or the cloud is the best protection against ransomware Trojans like the WininiCrypt Ransomware. File backups undo the WininiCrypt Ransomware attack completely since it removes the con artists' power to demand a ransom payment from the victim. Combining file backups with an anti-malware program should be enough to protect you from the WininiCrypt Ransomware and other ransomware.
SpyHunter Detects & Remove WininiCrypt Ransomware
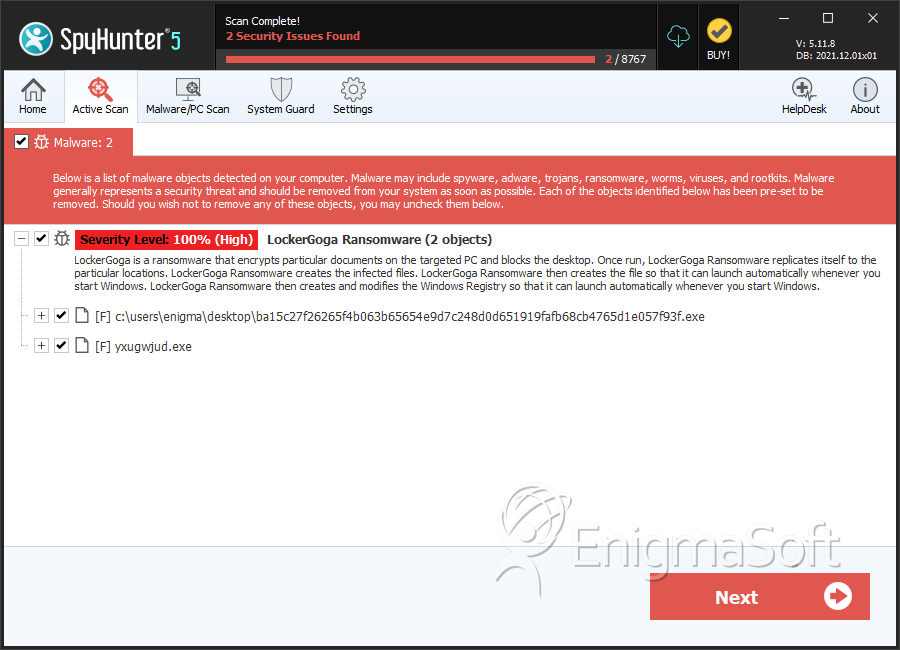
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ba15c27f26265f4b063b65654e9d7c248d0d651919fafb68cb4765d1e057f93f.exe | 3b200c8173a92c94441cb062d38012f6 | 3 |
| 2. | yxugwjud.exe | 16bcc3b7f32c41e7c7222bf37fe39fe6 | 2 |

