WindTail
The WindTail infostealer is a macOS threat that was developed by the WindShift APT (Advanced Persistence Threat), a hacking group that operates mainly in the Middle East. The WindShift APT specializes in malware targeting Apple products, whose security features have often been touted beyond their actual capabilities.
Many Mac users are under the impression that their computer is virus-proof, but – as malware like WindTail shows us – this isn’t the case. WindTail is an infostealer developed by the WindShift APT (Advanced Persistent Threat) to target macOS. WindShift is a hacking group based out of the Middle East. The group specializes in targeting Apple devices with their malware, computers that are marketed as, and believed to be, far more secure than they really are.
Table of Contents
Who Does WindTail Target?
There is a bit of potential good news for the average Mac user; it seems like WindShift is primarily targeting Middle East government targets. There is evidence that the group was running surveillance on their targets for several years before launching their infection campaign.
The group conducted surveillance across several phases and used a variety of techniques to gather information, according to a report from Taha Karim, a security researcher. The initial phase of reconnaissance involved the use of fake online personas. The group used the personas to communicate with the target organizations on social networks. LinkedIn was their primary point of contact, but they also interacted with targets over Facebook, Instagram, Google Plus, and Twitter.
The goal of the interactions was to gather personally identifiable information about their targets, such as emails, contacts, and phone numbers. The second phase began after the data collection was completed. This phase involved sending the targets spoof emails that appeared to be from legitimate sources. The emails contained scripts that allowed attackers to track their target’s location, clicking habits, interests, and what type of computer they were using.
While the initial phases took several years to pull off, the third phase was completed relatively quickly in under a day. The third phase was when the attackers issued fake password recovery and reset emails, as well as SMS redirects, that sent users to fake credential harvesting pages. The pages were designed to look like legitimate login portals for services, including Gmail, Outlook, iCloud, and Etisalat, the primary ISP for the UAE.
If the third phase had failed, the group would have resorted to hacking to get the information they wanted. This would be where WindTail came in.
How Does WindTail Bypass Protections?
Macs are made with robust security features that make people think they are impenetrable. The truth is that Xprotect and Gatekeeper aren’t as infallible as the general public has been led to believe. These defenses don’t mean much in the face of a serious threat actor with the right skills and motivation.
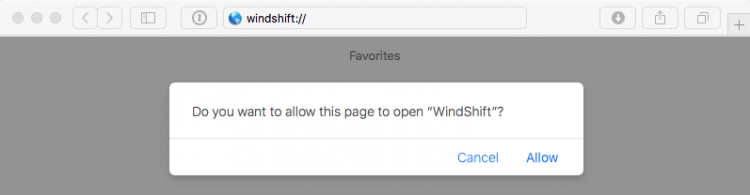
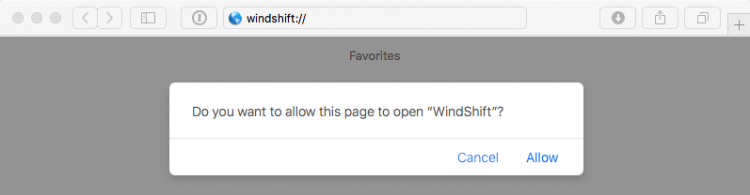
WindTail can get around Mac security features by abusing custom URL schemes propagated through connection vectors established with victims during the recon phase. While this kind of infection can rely on user interaction, the user interaction necessary is minimal, and attackers can easily influence their targets into doing it. All it takes is a simple approval request, as shown below;
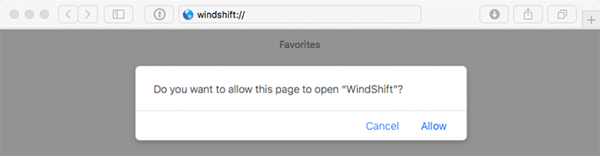
Approval Request
Those using an older version of Safari won’t even receive an approval request when trying to load a custom URL. The system will launch the malicious application without any input from users. If this were to happen with WindTail or another similar threat, it would grant those malicious applications persistence on the device as a Login item. Even in cases where the system is up to date and asks users to allow for the application to open, the hackers can just change the content in the message to make it seem benign. Users will allow the malicious link without a second thought because they don’t understand how dangerous it is.
Even though WindTail was initially designed for a specific target, the virus has no made its way into the wild. This is proof that the ATP behind the great was able to effectively bypass security and install their malicious applications on target devices.
What Does WindTail Do?
The first thing WindTail does is establish persistence on a target computer. After that, it will get to work finding specific file types – such as .pdf, .doc, .rtf, .ppt, .xls, .db, and more. The virus archives any files that fit these criteria using the zip utility built-in to Mac computers and sends them to the command and control (C2) server of the threat actor.
The main goal of WindTail is to establish persistence and exfiltrate data continuously to a remote server. That purpose fits neatly into the idea of a cyber-espionage campaign, such as the campaign launched by the WindShift group.
Experts have also issued warnings that some samples of the virus they found and tested had another module. This other module would allow the infostealer to work like a trojan and install additional malware onto an infected system.