Win32.HLLW.Phorpiex.54
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 115 |
| First Seen: | April 5, 2013 |
| Last Seen: | March 25, 2023 |
| OS(es) Affected: | Windows |
Win32.HLLW.Phorpiex.54 is a worm, which proliferates via spam email attachments or copies itself to removable data storage devices and enables attackers to obtain full remote access and control of an affected PC. Win32.HLLW.Phorpiex.54 may also be distributed via via instant messaging programs, such as Skype, Google Talk, Paltalk, Xfire, ICQ, and Windows Live Messenger. PC users may unknowingly download Win32.HLLW.Phorpiex.54, thinking it is a legal program. Win32.HLLW.Phorpiex.54 sends a message to all of the affected computer owner's contacts, and strives to attract or fool him/her into downloading and opening a picture, which may be a copy of Win32.HLLW.Phorpiex.54. The message is localized, and Win32.HLLW.Phorpiex.54 selects which message to send depending on the set language of the compromised PC. Win32.HLLW.Phorpiex.54 may drop malevolent files, which may be found as security infections.
Table of Contents
Aliases
12 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| AVG | Generic_r.BUT |
| Ikarus | Trojan.Win32.Bublik |
| Comodo | Heur.Corrupt.PE |
| eSafe | Suspicious File |
| F-Prot | W32/Damaged_File.B.gen!Eldorado |
| Fortinet | W32/Injector.FJX!tr |
| Ikarus | Trojan.SuspectCRC |
| McAfee-GW-Edition | Artemis!E896CEEF1DCB |
| DrWeb | Win32.HLLW.Phorpiex.54 |
| Kaspersky | UDS:DangerousObject.Multi.Generic |
| Symantec | Trojan.Fakeavlock |
| McAfee | BackDoor-FAQI |
SpyHunter Detects & Remove Win32.HLLW.Phorpiex.54
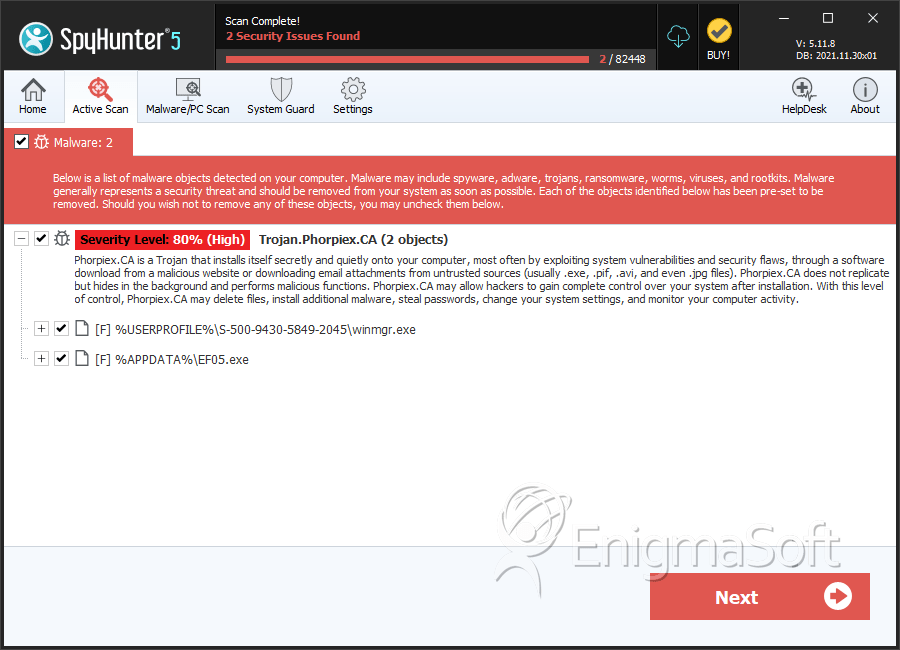
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | winmgr.exe | e896ceef1dcbcfc491a7fa02084fe6db | 6 |
| 2. | EF05.exe | b62dd064d09cc254792121a95d822dd8 | 1 |
| 3. | %HOMEPATH%\S-10-5765-8772-1584\winmgr.exe | ||
| 4. | [SYSTEM32]\wbem\Performance\WmiApRpl_new.ini |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.