Win32/Helompy
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 50 % (Medium) |
| Infected Computers: | 1,559 |
| First Seen: | December 14, 2011 |
| Last Seen: | August 24, 2021 |
| OS(es) Affected: | Windows |
Win32/Helompy is a dangerous worm that circulates by replicating itself to the root of removable drives. The main payload of Win32/Helompy is to record account credentials and login information and forward them to a remote server, where the attacker could retrieve them for use. At its roots, Win32/Helompy is a compiled AutoIt script and presents itself in an innocent way by using the icon of a folder, thus tricking computer users into trusting they are purely opening a folder once double-clicked on it. When Win32/Helompy is initiated, it creates a directory with the same name and opens the folder using a new instance of Explorer. Win32/Helompy creates a file folder and replicates itself to that directory with 'hidden', 'system' and 'read-only' file attributes, to disguise itself. The new copy of Win32/Helompy may be named 'configuration.exe', '1.exe' or 'lsass.exe'. Win32/Helompy modifies the registry so that it can run each time you start up Windows. As a payload, Win32/Helompy awaits login information to be entered for various web pages or services. Remove Win32/Helompy as soon as possible.
SpyHunter Detects & Remove Win32/Helompy
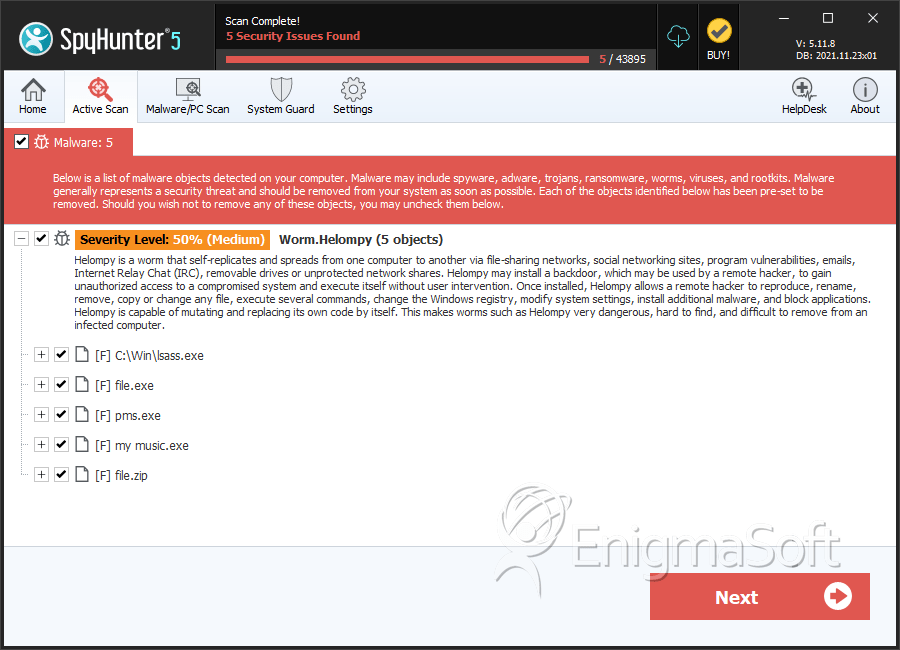
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | lsass.exe | fe7b2805aefc92f49a79db6b0948a7d7 | 75 |
| 2. | file.exe | 3512cc2170cb31ce188306bc8e322425 | 0 |
| 3. | pms.exe | 59d54c2871cf9799c8dcb6d05b94925c | 0 |
| 4. | my music.exe | 98fd894ea9904174b4827544714b66e6 | 0 |
| 5. | file.zip | 907568045e17dea5d11a20a279a241c6 | 0 |
