Willow Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | October 29, 2021 |
| OS(es) Affected: | Windows |
The Willow Ransomware threat is a new potent malware uncovered by infosec researchers. The threat operates as typical ransomware - it aims to lock the files of its victims through a strong encryption algorithm. The targeted file types will become inaccessible, and victims will no longer be able to use their documents, databases, archives, photos, images, etc. The hackers responsible for deploying the threat will then extort the affected users for money to help restore access to the locked data.
As part of its nefarious functionality, the Willow Ransomware changes the names of the encrypted files by appending '.willow' as a new extension. To make sure that the affected users see the instructions of the hackers, the threat delivers two ransom notes with nearly identical messages. The first one will be displayed in an image that will replace the current desktop background. The second note will be contained inside a newly-created text file named 'READMEPLEASE.txt.'
Table of Contents
Ransom Note’s Details
The two notes have very minor differences in the text but all of the important details are the same. The hackers want to be paid a ransom of exactly $500. However, victims must send the money using the Bitcoin cryptocurrency to the provided crypto-wallet address. At the current Bitcoin exchange rate, the ransom stands at 0.1473766 BTC. Keep in mind that Bitcoin is volatile inherently and its valuation can change rapidly. The Willow Ransomware hackers warn that if their demands are not fulfilled, the encrypted files will be deleted and users will lose their data completely.
The full text of the message found inside the 'READMEPLEASE.txt' file is:
'Hello lad. I, Willow Wolf, encrypted your files yet again.
But as I'm good now, I done it because I think you are an threat to The Silver Paw
and The Safe Place. Most of your files are encrypted.
Pay me $500 in some way. If not - I'm sorry, you'll lose your files, and any
decryptor key is totally useless.Payment information:
Amount: 0.1473766 BTC
Bitcoin Address:'
SpyHunter Detects & Remove Willow Ransomware
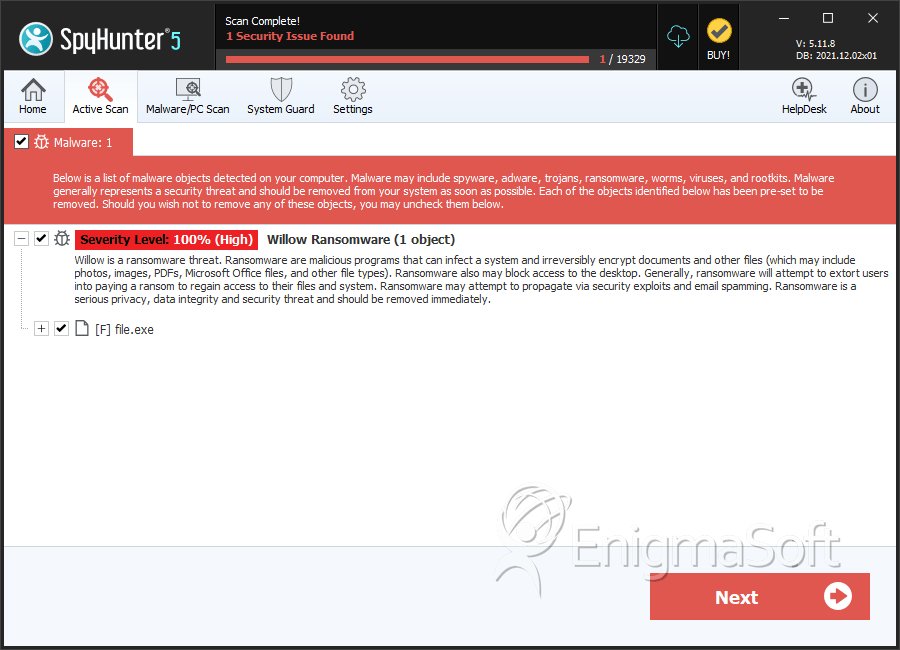
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | a31b18f6f5e28a05b92e29d3f2feb6e8 | 1 |

