Webalta
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 10,919 |
| Threat Level: | 20 % (Normal) |
| Infected Computers: | 5,076 |
| First Seen: | February 13, 2012 |
| Last Seen: | November 13, 2025 |
| OS(es) Affected: | Windows |
Webalta is a computer web browser hijacker that is known to change the default settings or internet settings of an infected system. Through Webalta a computer's web browser applications may load a different pre-set default home page and later cause website redirects. In some cases the redirects from Webalta may land user's on unwanted pages or ones hacked where they may spread malware. The home.Webalta.ru web page is a known culprit of installing toolbars and making internet settings changes. The Webalta toolbar is also installed from some of the related sources, which will perform the same malicious functions in addition to potentially displaying annoying pop-up alerts or advertisements. The Webalta.ru creators are in the business of generating money from collecting site clicks, which is part of the redirect scheme rendered by the Webalta virus.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| Panda | Generic Malware |
| AVG | Generic4.CLPB |
| Fortinet | W32/Toolbar_Webalta.A |
| Ikarus | AdWare.Win32.Webalta |
| GData | Win32:Ivelog-F |
| AntiVir | TR/Ivelog.F.10 |
| eSafe | Win32.TRIvelog.F |
| Symantec | Trojan.ADH.2 |
| NOD32 | Win32/Adware.Toolbar.Webalta.A |
| McAfee | Artemis!0FCB75E9981D |
| AVG | Proxy.ASMH |
| Ikarus | Backdoor.Win32.ProxyBot |
| Sophos | Mal/Proxy-E |
| BitDefender | Gen:Variant.Kazy.50862 |
| McAfee | Artemis!AE9F73DF396B |
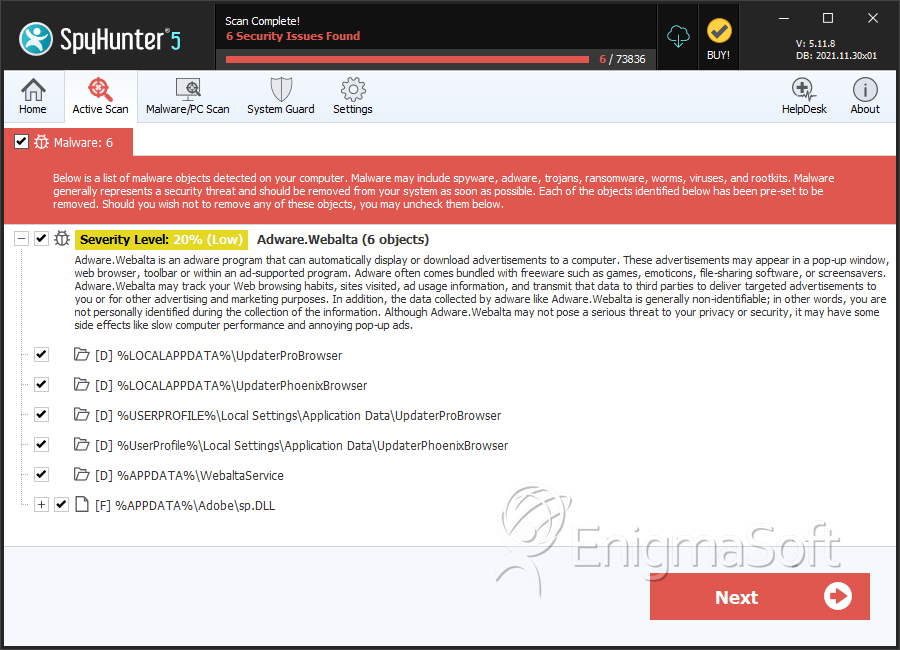
SpyHunter Detects & Remove Webalta
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | sp.DLL | ae9f73df396bfbec4873567a859276da | 8 |
Directories
Webalta may create the following directory or directories:
| %APPDATA%\WebaltaService |
| %LOCALAPPDATA%\UpdaterPhoenixBrowser |
| %LOCALAPPDATA%\UpdaterProBrowser |
| %USERPROFILE%\Local Settings\Application Data\UpdaterProBrowser |
| %UserProfile%\Local Settings\Application Data\UpdaterPhoenixBrowser |
Analysis Report
General information
| Family Name: | Adware.Webalta |
|---|---|
| Signature status: | Modified signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
c9699da5a538e285ffaf15fa206ba28d
SHA1:
f42fb198eb4d7f65c874b8ef6403d25062783224
File Size:
1.14 MB, 1137720 bytes
|
|
MD5:
9ef30c2c8228532a96465975df536be5
SHA1:
d94e54bb88c16fc949569b9e04f7b0c3c8cabf17
File Size:
1.15 MB, 1149496 bytes
|
|
MD5:
0f7401bda6434ed760623de4c4de5157
SHA1:
8273be933c14ffabac0db68d153c870d6fb6cc52
SHA256:
079E4CB28DEEE8DF83BCF503645DA5C9A322772DF479D973B2AE60B5A0E332CF
File Size:
1.14 MB, 1142840 bytes
|
|
MD5:
2b018ab83fa35eada45ed64bca87f367
SHA1:
2eb208a8303509a87c5e54be471722b6401f80b0
SHA256:
92C08B8F424139C02AC2D4242268B02C82DC89EB99F78E39D59D86233050ADD7
File Size:
1.15 MB, 1150008 bytes
|
|
MD5:
e616823f4c0db975577079fb48238079
SHA1:
f3129b850a6d62b2e6ca984767ce4fa19d188d8a
SHA256:
D164BFC9D6655B9BF2B85947987E10B1FABE76313B0B931F4D4771D4BEA6E199
File Size:
1.15 MB, 1154616 bytes
|
Show More
|
MD5:
1499d5039b85befce278b835fb21c3b3
SHA1:
a1b8e94f5dc33a04a0534ce2bf99b85763e0db6f
SHA256:
BDA8CCED7749980D525E0E89775602672DDBD58810A77B6A16FBABD4E9F6E70F
File Size:
1.15 MB, 1150008 bytes
|
|
MD5:
1795bc6597940dc70c18773c6cbeadd3
SHA1:
5d2147cf4392ad4d82e6a8f7662e14eaf7cd20ff
SHA256:
75BB275845D5CBC27CB01156A29ADFA2D73A83E1C8F890DEAE14765CEF2354F6
File Size:
1.15 MB, 1148472 bytes
|
|
MD5:
8356d45ae8c78f075687232f360f090f
SHA1:
6ccb99a42b7d4c8032aefde35c47cce450ac208e
SHA256:
568FE9B565B186F329540899F0EB79AE1E320F5DD7D95562E4FBFB929D73C41F
File Size:
1.13 MB, 1134648 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File has TLS information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
Show More
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Show More
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 3,430 |
|---|---|
| Potentially Malicious Blocks: | 36 |
| Whitelisted Blocks: | 3,355 |
| Unknown Blocks: | 39 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- Hupigon.DA
- Injector.DFF
- Injector.GPB
- Injector.GSD
- Keygen.XC
Show More
- SchwarzeSonneRAT.A
- Videspra.A
