Wana Decrypt0r 2.0 Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 8,282 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 15,183 |
| First Seen: | May 12, 2017 |
| Last Seen: | December 27, 2025 |
| OS(es) Affected: | Windows |
Although the Wana Decrypt0r 2.0 Ransomware appears to be a legitimate ransomware Trojan, it is a harmless copycat that was designed as a way to test peoples' online security habits originally. It is very unlikely that the Wana Decrypt0r 2.0 Ransomware has entered your computer, but if it has, then it is likely that someone is trying to teach you a lesson about preventing ransomware Trojan infections. The Wana Decrypt0r 2.0 Ransomware is harmless and is merely designed to test whether people will open a suspicious file attachment (which could lead to a severe threat infection potentially).
Table of Contents
The Roots of the Wana Decrypt0r 2.0 Ransomware
An admin at SysNative that goes by the online name Tom982 developed a copycat version of WannaCry named the Wana Decrypt0r 2.0 Ransomware to test whether his family could fall to a ransomware tactic. The Wana Decrypt0r 2.0 Ransomware, designed to resemble WannaCry, is designed to display a message on the infected computer. WannaCry is a ransomware infection that has managed to affect hundreds of thousands of computers around the world in a very short time span. Due to the media attention that WannaCry received and the high- profile of many of its targets, it has become more necessary than ever to learn how to protect your computer from online threats.
How the Wana Decrypt0r 2.0 Ransomware Infection Works
The Wana Decrypt0r 2.0 Ransomware is a tiny program that is merely designed to display a ransom image on the victim's Desktop. The Wana Decrypt0r 2.0 Ransomware message is a screenshot of the ransom notification that is used in a WannaCry attack. The Wana Decrypt0r 2.0 Ransomware displays this alarming image for about ten seconds and then switches it out, displaying instead a small text message that reads as follows:
'Fortunately for you, this is just a test (which you failed). You need to very careful opening unknown files, even from me. Call me.'
How the Wana Decrypt0r 2.0 Ransomware may Enter a Computer
To spread the Wana Decrypt0r 2.0 Ransomware to his family and friends, the Wana Decrypt0r 2.0 Ransomware developer created a fake Microsoft Word document, which had a double extension to hide its true nature (its extension would look something like '.docx.ex,' where the executable nature of the file would be hidden). When opening the file, a User Account Control message would appear, as tends to happen in the majority of these infections. When the victim clicks on OK to allow the file to load, it displays the fake ransom note on the victim's computer. Of course, this is a harsh way to teach people about ransomware and not recommended by PC security researchers. Despite their best of intentions, these educational ransomware Trojans tend to backfire in different ways. In the worst cases, a ransomware platform created for educational purposes or con artists creating threatening ransomware can modify proof of concept purposes easily. It is not difficult to think of a way in which con artists could adapt the Wana Decrypt0r 2.0 Ransomware to carry out actual tactics. By simply removing the portion with the text message, the Wana Decrypt0r 2.0 Ransomware could be turned into a functional scareware threat easily.
Protecting Yourself from the Wana Decrypt0r 2.0 Ransomware
Computer users should take care when opening any email attachment, even if it appears to have been sent by a trusted source. One must be especially careful with files that have double extensions like the fake Microsoft Word file that has been associated with the Wana Decrypt0r 2.0 Ransomware attack. Pay attention to User Account Control notifications like the one linked to the Wana Decrypt0r 2.0 Ransomware because they are designed to prevent threats and untrustworthy code from running on your computer.
SpyHunter Detects & Remove Wana Decrypt0r 2.0 Ransomware
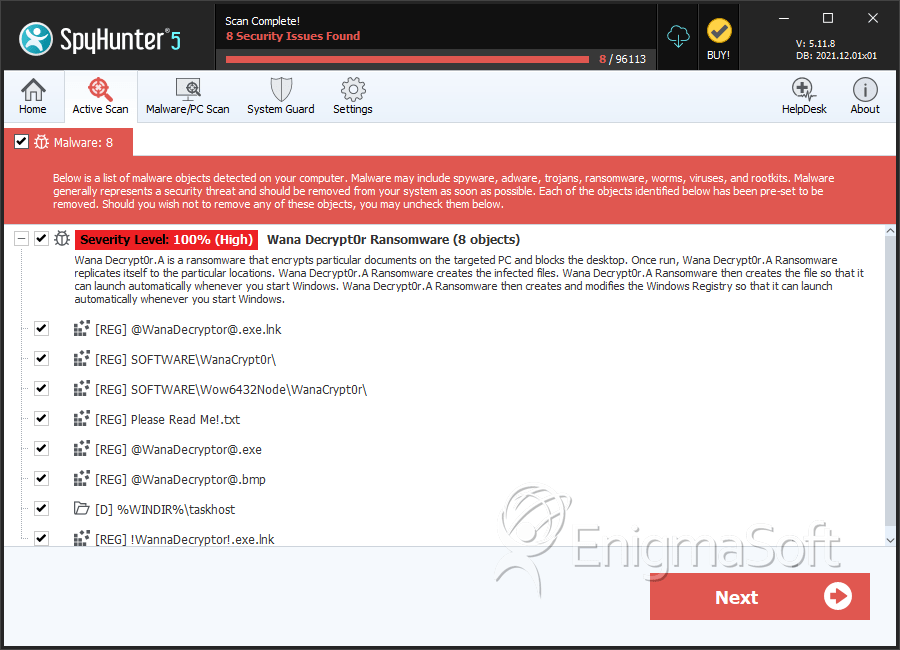
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | taskhcst.exe | 5c7fb0927db37372da25f270708103a2 | 104 |
| 2. | @WanaDecryptor@.exe | d724ea744f9056565c1dc235b8a37d3a | 3 |
| 3. | @WanaDecryptor@.exe.lnk | da694aa92d06c170e9bcebc540e3290f | 1 |
| 4. | 002f660b2867c78d57fa887549dd4df9ced41fc4e738f8d4a70e3cf555bd17c0.exe | 26b716a0017ea59f4a7e10f4045f8de6 | 0 |
| 5. | 0a73291ab5607aef7db23863cf8e72f55bcb3c273bb47f00edf011515aeb5894.exe | d5c0caf39de29dc769204d33e76c21fc | 0 |
| 6. | 0fc245e8a1134e31b7687fb7501faa05628813c87b9561ee26f2092cb76e5a36.exe | eac0133cec98c1338d721c6dff14128e | 0 |
| 7. | bb829a0394fb865eed381eb77ac9de039ad19e0f2318baaf9483b4f817250021.exe | cf7d967cf7f37075b74ae1956609f33b | 0 |
| 8. | bbf16aa9e9c3b697c1f4008a9087e2b3ed4298dbf62a607900d3b95324100327.exe | d2f5b8921d8b0ec80ca9d12a4628f4a0 | 0 |
| 9. | bc8136b40b4164afcbcb4e14f6fd54ca02275ff75b674eb6fd0a8f436f9b1181.exe | 05480f5a3237cb12416459c2660367b0 | 0 |
| 10. | c26e5eb8ec5b72e2c6368156f112f78906a57b393845233e727a8b2e3df790a4.exe | 0590e4be096701e650797f8969e3c2cf | 0 |
| 11. | c4291ec3eacfd145bbe75d7e7991753f4ea141768f6701e4bef4ca902ed58554.exe | aed6ed89e62f1cb059b5db200f30d203 | 0 |
| 12. | ca29de1dc8817868c93e54b09f557fe14e40083c0955294df5bd91f52ba469c8.exe | b0ad5902366f860f85b892867e5b1e87 | 0 |
| 13. | cd049fa3d5c193b82b13bc5c141696e7f862b448b9008a21c3c84030d5b00597.exe | d539b514ca46f0b33838a67778a4c92c | 0 |
| 14. | cd53771c1aa9d8b91d362feec69a03a02fbfcc8c922e2ed538854b77f9d806f2.exe | 994cfca9f4a14921684bd6a65997e22c | 0 |
| 15. | d849067bf9365d99088cbb935a98477cd38519e3ab8ac1bfe662588f8177d22d.exe | ae72a3d3b9ee295436ba281171c50538 | 0 |
| 16. | e28f2ee59621e1d9269213e2b5557b5066945774392b16bde3df9ad077bff107.exe | 03f75fc504c9845aaed29fdf66c13238 | 0 |
| 17. | e498f936eb56fb1f4300d973c1c869fa65e0ae368c74285dfc2feae3ae1a4f4e.exe | c1b5e18f78b644d5d59e8958fcfa8b0d | 0 |
| 18. | e5b9bfe333ee11538ae62cd9f34023d23e943970e771f74e088166e7c471166f.exe | 1eba841f8cb1d7703cecd5112bb2a3ea | 0 |
| 19. | e7a39735ee8777473c7405a70f470a0e00d6266d3126d3af59660e6a78dab2cf.exe | e8d2d6925c5581cff64670c829e5a473 | 0 |
| 20. | ea428033152445a507f4c1afb7734c8f801f27a687d8cb62bd8f393a2b0c466c.exe | 38a92fa34353ecb8777a8044248f56f2 | 0 |
| 21. | ea7974484b788d4c91044f32130159e1542bf079329179f4b1d42e93168dfdde.exe | 9873afd7cf2e1eb9e94bcbfc2dd74f40 | 0 |
| 22. | ec82b602d6389c4586730bd45302acf3366132ed63667cf8cfb24c7e72419fac.exe | b881c16467d6c3dbcb0b5a4db4d283ad | 0 |
| 23. | ed2e2be93f0dd70da08e6440521069931c0a9bbcaa1f64e88a6dd8b8953a72d7.exe | d38d30ed1bba3b9f76758eafcce71601 | 0 |
| 24. | f029548806c8074a36435241d5f5586cd7b37fc651dd2a9178e915d2cef27bae.exe | ac29e5bbe740c883baf1e83ba99eba85 | 0 |
| 25. | f5ea4c4f9a37bc84124a9ce114bb7b3dc7a35de498c6c50f457765cc7a3e7611.exe | 823564f14cdac838c31bbae713ff1ff6 | 0 |
| 26. | fecfd70406cbcd17fd17ccf4c635172249df13383d7f02fc9f0d3173da04a209.exe | a2592f41e67f1d0b9b795a3f4c71ad14 | 0 |
| 27. | home.exe | 4e259c5a7afe86eb08b45eead12d4af3 | 0 |
Registry Details
Directories
Wana Decrypt0r 2.0 Ransomware may create the following directory or directories:
| %WINDIR%\taskhost |
| %userprofile%\desktop\WannaCry |
| %userprofile%\downloads\WannaCry |
Analysis Report
General information
| Family Name: | Wana Decrypt0r Ransomware |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
27bb6e665f203c1614daab07a64a5fe5
SHA1:
f292c121b8be5aaf22c2d31d675b0396e9263d0c
SHA256:
A2ECC681C8A95A83E80E165A55E9E1D32DAFBB0A8D17534BEDA12FCDB3AC4C1F
File Size:
3.78 MB, 3778886 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
Show More
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Traits
- big overlay
- HighEntropy
- No Version Info
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 270 |
|---|---|
| Potentially Malicious Blocks: | 134 |
| Whitelisted Blocks: | 136 |
| Unknown Blocks: | 0 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- Wana Decrypt0r.A
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\windows\tasksche.exe | Generic Write,Read Attributes |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Network Wininet |
|
| Service Control |
|
| Process Shell Execute |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
C:\WINDOWS\tasksche.exe /i
|
