W32/AutoIt-JY
W32/AutoIt-JY is a malware threat that is designed to self-replicate and to spread as widely as possible. Unlike viruses, W32/AutoIt-JY has the ability to spread through a network or through peer-to-peer applications. Unlike Trojans, W32/AutoIt-JY also has the ability to infect a computer and install its malicious components by itself. ESG security researchers consider W32/AutoIt-JY dangerous threat to a computer's security. The presence of W32/AutoIt-JY can severely impact a computer's performance, disk space and functionality. It also makes changes to a computer's security components, making it more vulnerable to further malware infections.
W32/AutoIt-JY is installed as a default debugger. This means that a specific application can be corrupted to launch W32/AutoIt-JY each time W32/AutoIt-JY Worm is run. Other malware also does this to replace an application with an error message or with a fake version. In the case of W32/AutoIt-JY, this is done to ensure that W32/AutoIt-JY is launched as many times as possible in the infected computer. W32/AutoIt-JY creates two kinds of directories. It creates a directory named "GoodNight" and, inside it, a directory named "Fucking_Hero". It will also create an extremely large number of directories in the system32 folder, all named with what are seemingly random numbers. These will continually grow in quantity as W32/AutoIt-JY gradually infiltrates the infected computer.
A W32/AutoIt-JY Worm infection must be treated systemically, rather than focusing on each individual computer that has been infected with this harmful invader. It is not enough to treat the infected computer, it is also important to seek out all other computers on the same network, every computer that may have come into contact with the infection through peer-to-peer applications, contacts on that computer's email and IM list of contacts and any computer that may have come into contact indirectly through a removable storage device. It is also important to scan and disinfect all external memory devices that may have come into contact with the infected computer (such as writable CDs, memory cards, external hard drives, and USB memory sticks.) Failing to perform this kind of search raises the risk for a possible future re-infection with W32/AutoIt-JY. ESG security advisers recommend using a legitimate, up-to-date anti-malware tool to remove W32/AutoIt-JY automatically. Manual removal is not recommended due to this worm's self-replicating abilities.
Table of Contents
SpyHunter Detects & Remove W32/AutoIt-JY
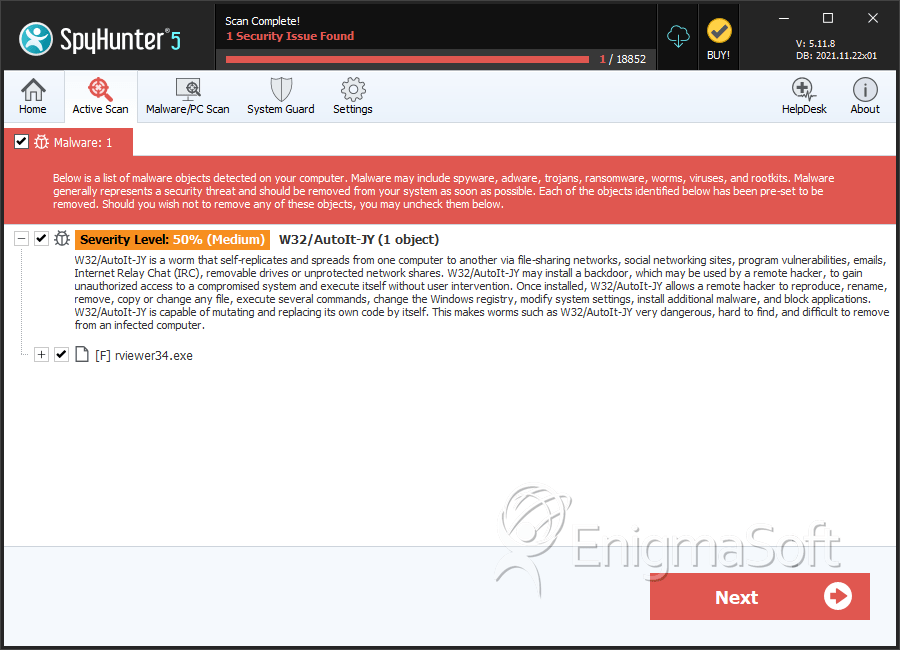
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | c:\system32\system.com | ||
| 2. | c:\system32\ctfmon.com | ||
| 3. | c:\system32\891249\154\2\4\52\34\5\5\2\34\5\234\5234\523452345\234\52345\23462\362\34\6523\452\346\234\52\345\24\624\36\234\62\346\2346\23\46\services.exe | ||
| 4. | c:\system32\cmd.com | ||
| 5. | c:\system\service.exe | ||
| 6. | rviewer34.exe | 2eaf3df25c9b4ba300dde0ed540c8739 | 0 |
| 7. | rviewer34.exe | fbaf4b18d7b31047e2e90eba81c97865 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.