Vvoa Ransomware
Vvoa Ransomware Image
The Vvoa Ransomware is the latest crypto locker threat to be spawned from the infamous and quite prolific Stop/Djvu malware family. As such, Vvoa doesn't display any major deviations from a typical threat from the Stop/Djvu family, which doesn't mean that it is any less threatening.
When the Vvoa Ransomware infects a computer, it will proceed to lock it through a powerful encryption algorithm effectively. Victims will find that they can no longer either access or use the files stored on the compromised device. All encrypted files will have '.vvoa' added to their original names as a new extension. The threat delivers a ransom note from the cybercriminals in the form of text files named '_readme.txt' that will be placed in every folder containing locked files.
According to the instructions, users affected by the Vvoa Ransomware will be extorted $980 if they want to obtain the decryption key and tool from the hackers. This is not an insignificant sum, and the criminals appear to realize that too. So, they offer to slash the price in half to $490 depending on whether the victims initiate communication within the first 72 hours following the Vvoa infection. For that purpose, two email addresses are provided - the main one at 'helpmanager@mail.ch' and a reserve address at 'restoremanager@airmail.cc.' A single file can be attached to the email message to be decrypted for free.
No matter how shocking it might be to lose all of your precious files suddenly, sending any amount of money to the criminals is never a wise decision. There are absolutely no guarantees that the hackers will uphold their end of the bargain while the money they have received will just further fuel their threatening activities.
The full text of the ransom note delivered by the Vvoa Ransomware is:
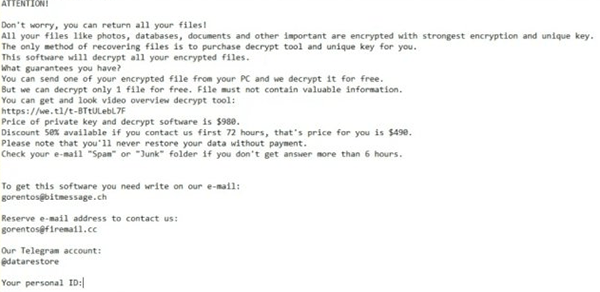
'ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-Dz5odBd07y
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your email "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our email:
helpmanager@mail.ch
Reserve email address to contact us:
restoremanager@airmail.cc
Your personal ID:'
Why Were My Files Encrypted?
Illegal software cracking tools are the primary distribution method for VVOA. Once the virus infects your system, it employs RSA encryption algorithms to modify your files and make them inaccessible. VVOA encrypts your files and holds them hostage, demanding you pay a ransom for the decryption.
The Ransom message explains the documents, photos, videos, and archive files on the computer have all been encrypted. Victims are told to write an email to the address in the note and include their personal ID to learn more. According to the message, The ransom demand will double if victims do not contact the attacker within 72 hours. In such a case, the ransom demand doubles from $490 to $980. As expected, the attackers demand that the money be paid in Bitcoin cryptocurrency to avoid it being traced back to them.
We recommend That victims never pay the ransom demand. Paying the demand could cause more problems than you are already dealing with right now. Hackers rarely deliver the decryption key. You would lose a lot of money on top of the encrypted data. Paying the criminals also makes you a potential target of future attacks and further funds the cybercrime industry and future malware development.
We recommend securely removing VVOA ransomware from your computer using a trustworthy antivirus program. You can use an external backup to restore your files once the virus is removed. If you don’t have a backup, you might be able to use file restoring software, but they are unreliable when it comes to ransomware damage.
How Does Ransomware Spread?
There are several popular distribution methods for ransomware. Many people are aware of the most common way but still choose to ignore it. We refer to illegal downloads and software cracking tools in particular. It’s common for users to turn to torrent sites when they want access to premium software without paying for a license. These people download illegal activation tools instead, which are commonly bundled with malicious software.
Hackers are aware that users want to get these programs for free. Attackers create bait by pairing cracks for popular software with ransomware executables. This method is effective because many people choose to ignore their antivirus when it flags a crack as malicious and proceed anyway, giving malware a free shot at their computer.
The other standard distribution method is to use spam emails. Hackers create legitimate-looking emails with attachments and links and send them to unsuspecting users. These messages are disguised as fake notices, proposals, tracking numbers, and invoices. Victims are compelled to open the attachment, which triggers a script to download the malware to their computer. Be on the lookout for malicious emails and only open email attachments if you are sure of the source.

