Vortex Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | March 10, 2017 |
| OS(es) Affected: | Windows |
The Vortex Ransomware infection is designed to target computer users in Poland. The Vortex Ransomware was first observed on March 9, 2017, and carries out a typical ransomware attack on infected computers. The Vortex Ransomware has been linked to two executable files on infected computers, which may be named 'AESxWin.exe' or 'polish.exe.' The most common way of distributing the Vortex Ransomware is through the use of corrupted email attachments that may be delivered using spam email messages. The Vortex Ransomware is installed on victim's computers by tricking them into opening a corrupted text document that uses macros to execute corrupted code on the infected computer. These files may be associated with social engineering techniques used to trick computer users into opening the file attachment. Opening the file reveals a blank page with a yellow message that reads 'Please, enable macro to load the document properly.' Of course, enabling macros (if they are not already enabled), allows the Vortex Ransomware to be installed and carry out its attack.
Table of Contents
This Vortex will Prevent You from Accessing Your Files
The Vortex Ransomware scans the victim's computer and determines which files will be encrypted. The Vortex Ransomware uses the AES 256 encryption to make the victim's files inaccessible completely. The Vortex Ransomware connects to a Web API to generate a random password that is 40 characters long for every infected computer. The Vortex Ransomware will encrypt the following file types on the infected computer:
.3GP, .7Z, .APK, .AVI, .BMP, .CDR, .CER, .CHM, .CONF, .CSS, .CSV, .DAT, .DB, .DBF, .DJVU, .DBX, .DOCM, ,DOC, .EPUB, .DOCX .FB2, .FLV, .GIF, .GZ, .ISO .IBOOKS,.JPEG, .JPG, .KEY, .MDB .MD2, .MDF, .MHT, .MOBI .MHTM, .MKV, .MOV, .MP3, .MP4, .MPG .MPEG, .PICT, .PDF, .PPS, .PKG, .PNG, .PPT .PPTX, .PPSX, .PSD, .RAR, .RTF, .SCR, .SWF, .SAV, .TIFF, .TIF, .TBL, .TORRENT, .TXT, .VSD,.WMV, .XLS, .XLSX, .XPS, .XML, .CKP, .ZIP, .JAVA, .PY, .ASM, .C, .CPP, .CS, .JS, .PHP, .DACPAC, .RBW, .RB, .MRG, .DCX, .DB3, .SQL, .SQLITE3, .SQLITE, .SQLITEDB, .PSD, .PSP, .PDB, .DXF, .DWG, .DRW, .CASB, .CCP, .CAL, .CMX, .CR2.
The files affected by the Vortex Ransomware encryption routine will be marked with the addition of the extension '.aes' to the end of the files' names. The Vortex Ransomware will drop a file named 'ODZSZYFRUJ-DANE.txt,' which translated into Polish means 'DECRYPT-DATA.txt.' This file, located on the victim's Desktop, asks the victim to pay $199 USD using BitCoins. The message is written in Polish, and can be translated as follows:
'the Vortex Ransomware
You can not find the necessary files on your hard drive? The contents of your files do not open?
This is a result of the program that encrypted the most of your data using strong algorithm aes-256 a minute ago. The uniformed service for disguising data transmitted electronically.
The only way to recover your files is buying a decryption program from us, with a single unique key generated for you!
Once you choose to recover your data, please contact us at e-mail: rsapl@openmailbox.org or poiskiransom@airmail.cc
2 Files Decrypted for free to prove that we are able to do so, for the rest, unfortunately, you have to pay!
Price for decryption of all files: $199
Warning! Do not waste your time, time is money for 4 days price will increase by 100%!
IP = [YOUR IP ADDRESS]
ID = [RANDOM CHARACTERS]'
Dealing with the Vortex Ransomware
Although the Vortex Ransomware is targeting Polish-speaking computer users clearly, it is not unlikely that computer users in other parts of the world will also be targeted by this attack. Malware analysts have the same advice for dealing with the Vortex Ransomware as with any other of the countless encryption ransomware Trojans that are active currently: computer users should refrain from following the instructions in the ransom note or paying the ransom amount. Instead, it will be necessary to recover the affected files from a backup after removing the Vortex Ransomware infection itself with the help of a reliable security program that is fully up-to-date.
SpyHunter Detects & Remove Vortex Ransomware
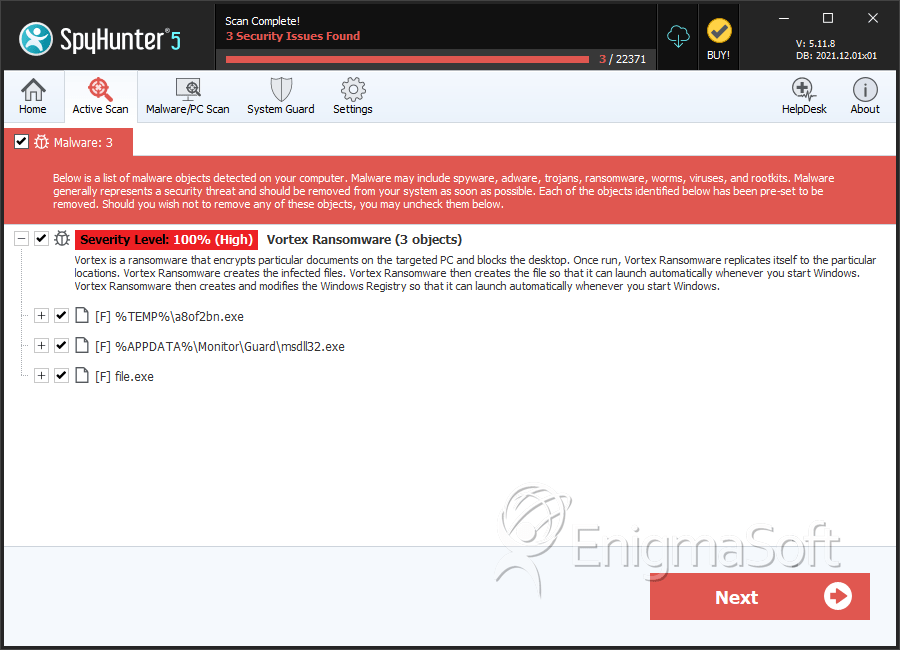
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | ac6a5927cc9ff8cfe821e73b0fc26cae | 0 |
| 2. | file.exe | f13428efe5bea3f2f413ded0940ff214 | 0 |
| 3. | file.exe | bf5eee6431e218b768c552676684b60f | 0 |
| 4. | file.exe | 642abb4ece3b3f21a6311b6af0dc43dc | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.