UselessDisk Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 2 |
| First Seen: | March 29, 2018 |
| Last Seen: | May 3, 2023 |
| OS(es) Affected: | Windows |
The UselessDisk Ransomware is an encryption ransomware Trojan that PC security researchers first observed on March 24, 2018. The UselessDisk Ransomware is being delivered to victims as an executable file named 'DiskWriter.exe,' which has led to some PC security analysts referring to the UselessDisk Ransomware as 'DiskWriter Ransomware.' This executable file installs this Trojan onto the victim's computer, allowing it to carry out its attack while bypassing many security programs. The UselessDisk Ransomware is a severe threat, and it is important to take steps to protect your data from threats like the UselessDisk Ransomware immediately since an UselessDisk Ransomware infection can be quite destructive.
Table of Contents
Your Hard Drives will Become Inaccessible When Infected by the UselessDisk Ransomware
The UselessDisk Ransomware is designed to make the victim's drives inaccessible. The UselessDisk Ransomware is regarded as a wiper Trojan, a destructive threat designed to make the victim's data inaccessible specifically. The UselessDisk Ransomware will encrypt the victim's files and offers no way of recovering the affected data. The UselessDisk Ransomware infects a computer on a deep level by modifying the Master Boot Record on the main system drive on the affected computer and preventing it from starting up the operating system. Threats that target the Master Boot Record can be destructive and difficult to deal with especially. Alterations to the master boot record can make a drive unusable permanently, and the damage that the UselessDisk Ransomware may cause to a targeted computer is irreversible. However, the UselessDisk Ransomware does not upload any decryption key to Command and Control servers, or have the capacity to help victims restore their captured data.
How the People Responsible for the UselessDisk Ransomware may Generate a Profit
The UselessDisk Ransomware uses the command line tool to shut down the infected computer and restart it after making the victim's files inaccessible. The UselessDisk Ransomware delivers a ransom note in the form of an alarming message displayed in red text over a black background. The UselessDisk Ransomware message reads as follows:
'Ooops,your important files are encrypted.
If you see this text,then your files are not accessible,because they've been encrypted.Maybe you're busy looking for a way to recover your files,but don't waste your time.Nobody can recover your files without our decryption service.
In order to decrypt.Please Send $300 worth of Bitcoin to this address:
1GZCw453MzQr8V2VAgJpRmKBYRDUJ8kzco'
The payment of the ransom asked by the UselessDisk Ransomware note is highly discouraged. This money will be wasted completely, though, since the people responsible for the UselessDisk Ransomware attack have no way of delivering a decryption key to the victim after the payment is made. It is clear that the cybercrooks have no intentions of helping victims of the attack restore their files. Because of the high amount of ransomware Trojans that are active currently, it is more important than ever for computer users to take preemptive steps to ensure that their data is safe from threats like the UselessDisk Ransomware.
Protecting Your Data from Threats Like the UselessDisk Ransomware
Dealing with threats like the UselessDisk Ransomware is extremely difficult if your files have been affected already. The encryption used in these attacks is quite strong, and the damage cannot be undone with available technology. The same technology that enables computer users to communicate online anonymously and keeps programming code confidential is also used in these attacks to make the victim's files inaccessible. Because of this aspect of the UselessDisk Ransomware attack, the best protection against the UselessDisk Ransomware and similar threats is to take preemptive steps to protect your data, such as having file backups. A reliable file backup system stored on a place that the threat can't reach, such as a disk image stored on an external server, can help computer users recover their data after an attack such as the UselessDisk Ransomware. This, coupled with an updated security program, can help computer users stay safe from these attacks
SpyHunter Detects & Remove UselessDisk Ransomware
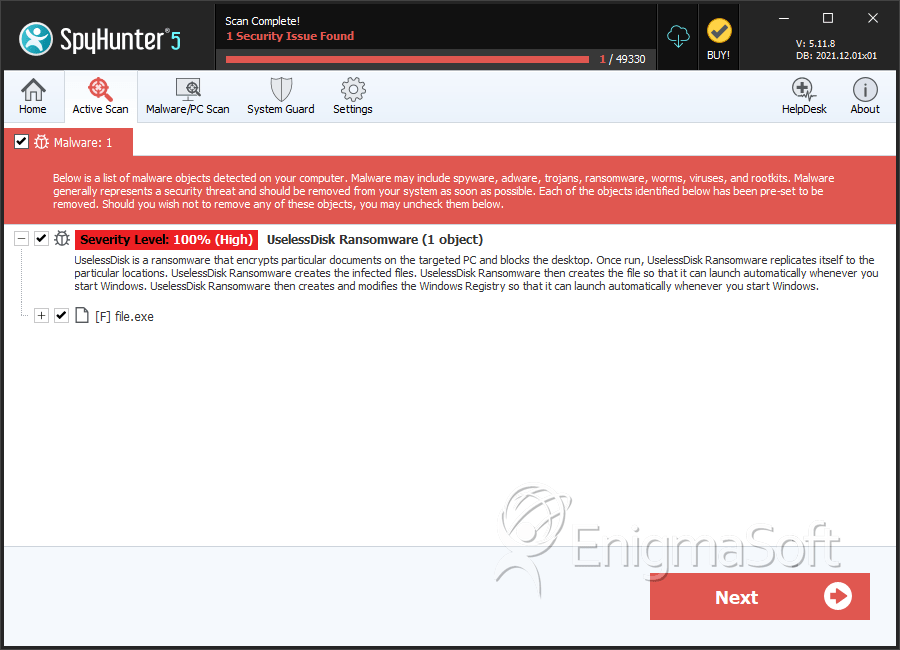
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | UselessDisk.bin.ex1 | 577be8c5b73e59fb71570f632349e5fe | 1 |

