Trojan.Win32.CoinStealer.i
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 8,867 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 4,883 |
| First Seen: | April 11, 2014 |
| Last Seen: | September 16, 2023 |
| OS(es) Affected: | Windows |
Trojan.Win32.CoinStealer.i is a Trojan used to collect Bitcoin wallets from victims. Trojan.Win32.CoinStealer.i was recently distributed by appending Trojan.Win32.CoinStealer.i to an archive containing records for the recently defunct Bitcoin exchange Mt. Gox. This archive was already suspect because it was distributed by hackers that compromised the Mt. Gox blog in a 620MB ZIP file containing Mt. Gox' transaction records. Trojan.Win32.CoinStealer.i is disguised as a Windows or Mac application for accessing the transactions of Mt. Gox, which had to apply for insolvency after losing nearly a million Bitcoins after becoming the victim of online attacks. Since the people that use to view these types of files are also likely to own Bitcoin wallets, this makes Trojan.Win32.CoinStealer.i particularly effective since Trojan.Win32.CoinStealer.i will almost always find Bitcoin wallet files on the victims' computers.
Table of Contents
Trojan.Win32.CoinStealer.i Cleans Up Your Bitcoin Wallet
Trojan.Win32.CoinStealer.i is linked to Windows and Mac LiveCode binaries associated with Mt. Gox. When these are executed, they display what seems to be a database graphical interface. This interface supposedly allows computer users to access Mt. Gox' database. Unfortunately, in the background they launch TibanneSocket.exe, detected as Trojan.Win32.CoinStealer.i, which searches the victim's computer for bitcoin.conf and wallet.dat files, both of which contain critical data about the victim's Bitcoin wallet. After the files are unencrypted, the persons behind Trojan.Win32.CoinStealer.i may collect the victim's Bitcoins. Trojan.Win32.CoinStealer.i has two versions, one designed to infect Windows and the other targeted towards Mac OSX. This second variant is particularly threatening because Mac users tend to be less careful about protecting their computer from threats due to the mistaken notion that non-Windows systems are invulnerable to threats.
Trojan.Win32.CoinStealer.i and the Mt. Gox Bankruptcy
It is very common for cybercrooks to take advantage of breaking news to target specific sectors of the population with threats. Taking advantage of the Mt. Gox bankruptcy scandal, third parties can specifically deliver Trojan.Win32.CoinStealer.i to computers that are more vulnerable to these attacks. This is especially true because a wider distribution of Trojan.Win32.CoinStealer.i may not be as effective because the persons that use Bitcoins regularly are still a tiny minority of total computer users.
SpyHunter Detects & Remove Trojan.Win32.CoinStealer.i
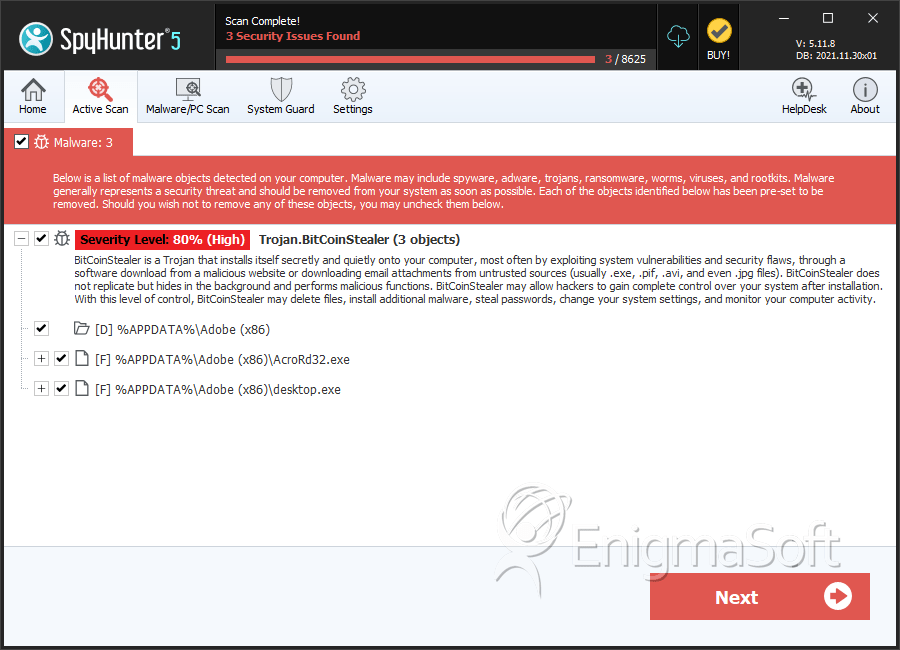
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | AcroRd32.exe | 4e5e2d3c73a48530b0b790456e0fabea | 4 |
| 2. | AcroRd32.exe | 4c3bd3eaa231550ffbc4865424ef82fc | 1 |
| 3. | desktop.exe | 3745e7d03914a446953c886a18d20c5a | 1 |
| 4. | MtGox2014Leak.zip | ||
| 5. | TibanneSocket.exe |
Registry Details
Directories
Trojan.Win32.CoinStealer.i may create the following directory or directories:
| %APPDATA%\Adobe (x86) |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.