Trojan.Ransomlock.G
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 21 |
| First Seen: | November 12, 2012 |
| Last Seen: | February 26, 2021 |
| OS(es) Affected: | Windows |
Trojan.Ransomlock.G is a large ransomware family better known as Reveton. These kinds of malware infections typically block access to the victim's computer and then demand that the victim pay a ransom in order to regain access to the infected computer. Trojan.Ransomlock.G and similar ransomware Trojans carry out this scam with the addition of a fake message from a law enforcement agency in order to make the scam more authentic and to scare novice PC users into paying the ransom. Trojan.Ransomlock.G's message claims that the victim's computer was used for illegal activities and that the ransom is actually a fine. Trojan.Ransomlock.G and its variants typically detect the victim's computer's location from its IP address in order to display a ransom message that is specific to that geographical location. Trojan.Ransomlock.G's ransom will typically be of one hundred Euro in its European variants and of about two hundred dollars in its variants that target computers in the United States.
Ransomware infections like Trojan.Ransomlock.G have been active since 2009. Although they first targeted computer users in the Russian Federation and in other Russian speaking countries, the problem first spread to the rest of Western Europe and, since Spring of 2012, has started targeting computers in the United States. There are numerous criminal organizations working simultaneously to produce ransomware infections like Trojan.Ransomlock.G and, due to the fact that these fake police messages are very similar, it is often difficult to tell one variant from another. ESG security researchers have observed that the criminal organizations responsible for ransomware infections are the same criminal organizations that are responsible for many rogue security programs and banking Trojans.
There is a reason why ransomware Trojans like Trojan.Ransomlock.G have increased in number so dramatically, they can be very lucrative. PC security researchers estimate that nearly three percent of all victims pay the ransom, which translates into hundreds of thousands of dollars considering the volume of infected computers that we are dealing with. Trojan.Ransomlock.G itself was used to infect more than half a million computers in little more than two weeks, resulting in a massive payout in a very short time. ESG malware analysts strongly advise against paying the ransom due to the fact that, in most cases, it will do nothing to remove the malware infection from the compromised computer.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Fortinet | W32/Foreign.CEVI!tr |
| Sophos | Mal/Generic-S |
| AntiVir | TR/Ransom.Foreign.cevi |
| Kaspersky | Trojan-Ransom.Win32.Foreign.cevi |
| Avast | Win32:Reveton-QK [Trj] |
| Panda | Generic Trojan |
| AVG | Ransomer.AOD |
| Fortinet | W32/Reveton.H |
| Ikarus | Trojan-Ransomer.AOD |
| AntiVir | TR/Agent.174080.21 |
| Sophos | Mal/EncPk-AHC |
| BitDefender | Gen:Trojan.Heur.LP.kq4@a4@xK4o |
| Kaspersky | HEUR:Trojan.Win32.Generic |
| Avast | Win32:Malware-gen |
| K7AntiVirus | Riskware |
SpyHunter Detects & Remove Trojan.Ransomlock.G
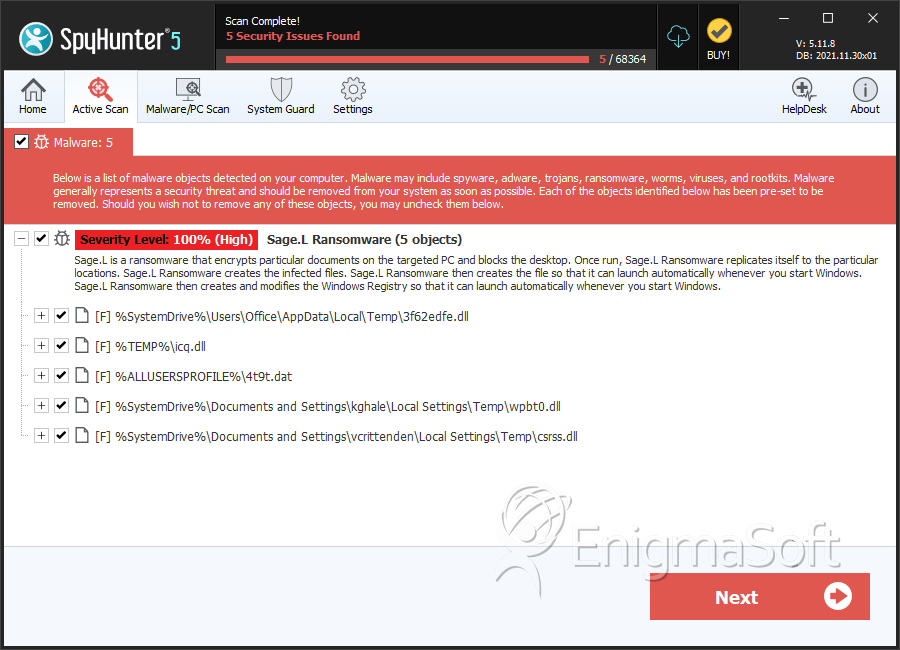
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 3f62edfe.dll | 48c1195feeefc0ea61db3e4960b55700 | 10 |
| 2. | icq.dll | 01752ce0be21fda7103c357c63c63d10 | 3 |
| 3. | 4t9t.dat | 2351741fb135a3c92951b12172f9b2ab | 3 |
| 4. | wpbt0.dll | 86d6eca1b5db9fb0fa554cc5cb26ec58 | 2 |
| 5. | csrss.dll | 4436e342dfd499331a2b883f903584c2 | 1 |
| 6. | %UserProfile%\Start Menu\Programs\Startup\ctfmon.lnk | ||
| 7. | %UserProfile%\Application Data\nur-xcp-sabb.pad |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.