Trojan-Downloader.Win32.Agent.ahoe
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 1,490 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 548,580 |
| First Seen: | July 24, 2009 |
| Last Seen: | January 30, 2026 |
| OS(es) Affected: | Windows |
Trojan-Downloader.Win32.Agent.ahoe is a trojan horse virus that typically infiltrates the computer from rogue websites or through file sharing programs. Trojan-Downloader.Win32.Agent.ahoe downloads malicious content from the Internet and executes them on the compromised machine without user knowledge or approval. Trojan-Downloader.Win32.Agent.ahoe creates its own registry entry to ensure that it begin running every time Windows starts up. Trojan-Downloader.Win32.Agent.ahoe typically appears listed in the scan results of the rogue anti-spyware program Windows Antivirus Pro.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| AVG | Downloader.Generic12.XJL |
| Fortinet | W32/Downloader_x.GCN!tr |
| AntiVir | TR/Agent.dpp.2 |
| Kaspersky | HEUR:Trojan.Win32.Generic |
| eSafe | Win32.TRAgent.Dpp |
| Avast | Win32:Agent-APGZ [Trj] |
| McAfee | Generic.dx!bcx4 |
| Ikarus | Trojan.SuspectCRC |
| AhnLab-V3 | Win-Clicker/Agent.499712 |
| AntiVir | TR/Gendal.kdv.300198 |
| BitDefender | Trojan.Generic.KDV.300198 |
| eSafe | Win32.WS.Reputation |
| McAfee | Artemis!764155503436 |
| Panda | Trj/Downloader.QBT |
| AVG | Delf.EKJ |
SpyHunter Detects & Remove Trojan-Downloader.Win32.Agent.ahoe
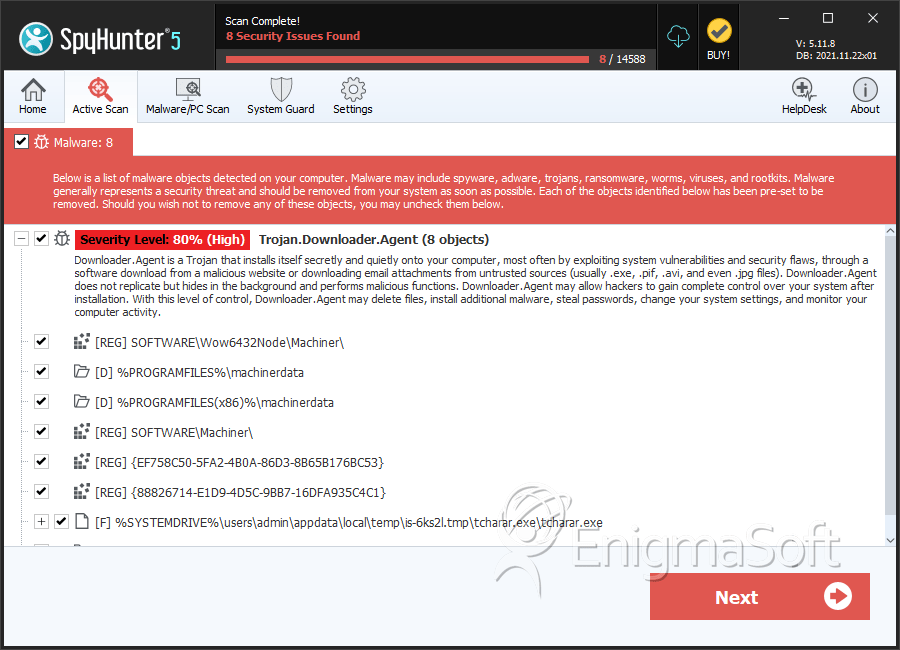
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | tcharar.exe | fb499993c46f50b75f102d5d59b61eb2 | 9,924 |
| 2. | NetUpdService.exe | ac9fa3514f1313c92ae5a52938a50d9a | 1,482 |
| 3. | lsmsrv.exe | b262a3f123fc2ad625654813cf3c3734 | 84 |
| 4. | Client.exe | 1362cac64386ac917c3b91e29749740f | 49 |
| 5. | TssWpfWrp.exe | d017768239636f67bfafd5e02ec53918 | 29 |
| 6. | digital1610_Good_11cr13.exe | 35164e8135d144bf04395e62461d2a0e | 23 |
| 7. | Server.exe | 7f5b5834f8e8a25b7b6586b86091b72d | 20 |
| 8. | mscorsvcw.exe | 860a6d17959203f41a2ca6226270516c | 15 |
| 9. | AGSService.exe | 2d364060d6b042250a351507c0b6d556 | 9 |
| 10. | g666.tmp.exe | c7d0fd72924d39d78010aa13e5f1e3bf | 5 |
| 11. | WindowsDefenderUpdate.exe | 844430aac97001ca90f1e319711ba820 | 5 |
| 12. | get.exe | cd49e0979be34d51eee3606438184f52 | 4 |
| 13. | 4b3f7176cfd3fb818f8e4780b9ded838de5ff6d8cf01865d59fc68fb4c0e0424 | 00e7325c6b03ae161c5fbf755fa14739 | 3 |
| 14. | CasPol.exe | a7aaf4d9e10897faded9a4727a626900 | 1 |
| 15. | rundl64.exe | bce7203e636f826142284d5ac72892ec | 0 |
| 16. | msmsgs.exe | 2ab1867e8b59176adbac333f6357e978 | 0 |
| 17. | iOmm100.exe | 315dbe28016a28842556704148eba158 | 0 |
| 18. | ikwnmb.exe | dcb43c208a13b5c1cccebce576987b26 | 0 |
| 19. | dealassistant.exe | 1ae1c57db53066c7e1ef5076bb9b1b8b | 0 |
| 20. | retadpu77.exe | fc83423421cd2d1b09955e3aee7f29cf | 0 |
| 21. | mrofinu1000106.exe | 3e9f2da6cd3519cb9320f9ba8ed92c72 | 0 |
| 22. | retadpu1002397.exe | dde8bfd270ffeea1c763d1827734d0e4 | 0 |
| 23. | orz.exe | 8a548d9d41f045b29884ecd682d4f1d1 | 0 |
| 24. | pridl.exe | cd88b89d5e4eb922a4e179a1be66aefc | 0 |
| 25. | cpds.exe | fca86cdf5a1851c1c9c33726f0fc6c82 | 0 |
| 26. | file.exe | 865cd7bf0e4612204bfaff0e11bfd166 | 0 |
Registry Details
Directories
Trojan-Downloader.Win32.Agent.ahoe may create the following directory or directories:
| %ALLUSERSPROFILE%\gramblr |
| %ALLUSERSPROFILE%\nirds |
| %ALLUSERSPROFILE%\tlrzjcfpeq |
| %ALLUSERSPROFILE%\yemjxjfcbj |
| %APPDATA%\ww.fm |
| %LOCALAPPDATA%\WServices |
| %PROGRAMFILES%\Procedure |
| %PROGRAMFILES%\Windows Utility Update |
| %PROGRAMFILES%\eMail Extractor |
| %PROGRAMFILES%\machinerdata |
| %PROGRAMFILES(x86)%\Windows Utility Update |
| %PROGRAMFILES(x86)%\machinerdata |
| %TEMP%\HWMonitor |
| %USERPROFILE%\SecurityHealthSystray |
| %USERPROFILE%\cabapi |
| %UserProfile%\AppXDeploymentServer |
| %UserProfile%\wksprt |
Analysis Report
General information
| Family Name: | Trojan.Downloader.Agent |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
4c87a98b06b25d056ba958054f6df7a0
SHA1:
78e7071501e35ab8f8a06920869088d23cd72898
File Size:
46.18 KB, 46183 bytes
|
|
MD5:
b37f263aa3a12f66ac4cea307aa71bd5
SHA1:
7d39c32d4d5b78a79b1fe20121647f14d12958ee
File Size:
46.18 KB, 46180 bytes
|
|
MD5:
1b98bdc7a806091ddf1f929ff93abc97
SHA1:
de04ec480dc52fd96f883fb177f2402497f268b2
SHA256:
888F878D224C18A884FA2C2A68A5EE869CFA23939D3114E70656ADD9BE7ABDBE
File Size:
46.18 KB, 46181 bytes
|
|
MD5:
2892e1c722fe4a15e9f6451be44b1c97
SHA1:
80c1237f62ff8ad6ddbe20b6b00c22ef3e72ec1d
SHA256:
470B8826F437B92C95A09D0F83016B9CA8D25FFF777C288013B2282552175EF4
File Size:
46.18 KB, 46180 bytes
|
|
MD5:
02bd686d7320405b38fcb84578ad9bf9
SHA1:
8c48ee4cd9b0fa70f305b7c4a3ab70a391b2f026
SHA256:
8F3D62B448BB53A5F39373CA296FB5E6E2C50814EC3CA3FDDC5299E56AAAEC30
File Size:
46.18 KB, 46183 bytes
|
Show More
|
MD5:
3d6dc175d4a640a344b09b0313e7621c
SHA1:
b6c9d28d5dc128f4f44dc05f1714d2becc5b440d
SHA256:
D8776458DE607BA71132DE5F6877EBFB6950786B1BE1649E22AAFEEC1A1ECDC4
File Size:
46.18 KB, 46179 bytes
|
|
MD5:
fb33bad211ac5405443eeaad2cd4f324
SHA1:
307e6b510f1b8590adeb0514c8ee3db57d910d31
SHA256:
D94EFDE45FC4367F5B61C4614453052AEC335D848C88D28A392D2446A8AFA16B
File Size:
1.52 MB, 1515520 bytes
|
|
MD5:
b06df00c4478dc8e100e6af0079505dc
SHA1:
2f539c32b5b0fa8f042e161d674072ae13f67232
SHA256:
A52BD84EDFC8BF9A2922A413FF0E6D9928EE1ED9620F19C0DF206FF28602BC9B
File Size:
39.67 KB, 39667 bytes
|
|
MD5:
be57f871c1f3fd9f0fe98ea97de21a00
SHA1:
09339ea667e3f3975797b8fc41945b68502d544b
SHA256:
D4C74959C9BEF137F42341AB7F6CC9F557CDD4635A79350015F3D8A86673DD3F
File Size:
568.84 KB, 568836 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
Show More
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Company Name | noOrg |
| File Version | 1.00 |
| Internal Name | gg |
| Original Filename | gg.exe |
| Product Name | Project1 |
| Product Version | 1.00 |
File Traits
- HighEntropy
- No Version Info
- vb6
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 1,418 |
|---|---|
| Potentially Malicious Blocks: | 9 |
| Whitelisted Blocks: | 1,343 |
| Unknown Blocks: | 66 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\users\user\appdata\local\temp\nsa5a18.tmp | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsa5a18.tmp\pwgen.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsa5a18.tmp\pwgen.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsa5a18.tmp\system.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsa5a18.tmp\system.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsb3091.tmp | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsb3091.tmp\pwgen.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsb3091.tmp\pwgen.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsb3091.tmp\system.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsb3091.tmp\system.dll | Synchronize,Write Attributes |
Show More
| c:\users\user\appdata\local\temp\nsc5110.tmp | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsc5110.tmp\pwgen.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsc5110.tmp\pwgen.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsc5110.tmp\system.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsc5110.tmp\system.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsf7ab9.tmp | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsf7ab9.tmp\pwgen.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsf7ab9.tmp\pwgen.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsf7ab9.tmp\system.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsf7ab9.tmp\system.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsh57b1.tmp | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsh57b1.tmp\pwgen.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsh57b1.tmp\pwgen.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsh57b1.tmp\system.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsh57b1.tmp\system.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsn540d.tmp | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsn540d.tmp\pwgen.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsn540d.tmp\pwgen.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsn540d.tmp\system.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsn540d.tmp\system.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsq338e.tmp | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsq338e.tmp\pwgen.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsq338e.tmp\pwgen.dll | Synchronize,Write Attributes |
Registry Modifications
Registry Modifications
This section lists registry keys and values that were created, modified and/or deleted by samples in this family. Windows Registry activity can provide valuable insight into malware functionality. Additionally, malware often creates registry values to allow itself to automatically start and indefinitely persist after an initial infection has compromised the system.| Key::Value | Data | API Name |
|---|---|---|
| HKCU\software\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; Win64; x64; ovrFT49HUY | RegNtPreCreateKey |
| HKLM\software\wow6432node\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; Win64; x64; ovrFT49HUY | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Nmqimwrn\AppData\Local\Temp\nsn540D.tmp\ | RegNtPreCreateKey |
| HKCU\software\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; ovP2wW2d09 | RegNtPreCreateKey |
| HKLM\software\wow6432node\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; ovP2wW2d09 | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Fjxikcma\AppData\Local\Temp\nsc5110.tmp\ | RegNtPreCreateKey |
| HKCU\software\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; WOW64; ovLqlLUcpU | RegNtPreCreateKey |
| HKLM\software\wow6432node\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; WOW64; ovLqlLUcpU | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Zxtblvbb\AppData\Local\Temp\nsa5A18.tmp\ | RegNtPreCreateKey |
| HKCU\software\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; ovYdEXgYaa | RegNtPreCreateKey |
Show More
| HKLM\software\wow6432node\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; ovYdEXgYaa | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Oosmxeyw\AppData\Local\Temp\nsh57B1.tmp\ | RegNtPreCreateKey |
| HKCU\software\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; ovsyYj3YHK | RegNtPreCreateKey |
| HKLM\software\wow6432node\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; ovsyYj3YHK | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Nfvsrdon\AppData\Local\Temp\nsb3091.tmp\ | RegNtPreCreateKey |
| HKCU\software\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; WOW64; ov098YfArb | RegNtPreCreateKey |
| HKLM\software\wow6432node\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; WOW64; ov098YfArb | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Syxcgwon\AppData\Local\Temp\nsf7AB9.tmp\ | RegNtPreCreateKey |
| HKCU\software\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; Win64; x64; oQaf2tau | RegNtPreCreateKey |
| HKLM\software\wow6432node\microsoft\windows\currentversion\internet settings\5.0\user agent::platform | Windows NT 10.0; Win64; x64; oQaf2tau | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Program Files (x86)\Microsoft\EdgeUpdate\1.3.205.9��\??\C:\Windows\SystemTemp\626d5325-4419-4ac5-baae-1ad029bac7c6.tmp��\ | RegNtPreCreateKey |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Encryption Used |
|
| Other Suspicious |
|
