TBHRanso Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | November 28, 2017 |
| Last Seen: | July 6, 2018 |
| OS(es) Affected: | Windows |
The TBHRanso Ransomware is an encryption ransomware Trojan that cybercrooks use to make the victims' files inaccessible. PC security researchers first observed the TBHRanso Ransomware on November 22, 2017. Threats like the TBHRanso Ransomware are typically delivered to victims through the use of spam email messages (although there are a variety of other ways in which these threats can be delivered to the victims). Victims of this attack will receive an email message that contains a file attachment or embedded link initially. The messages are often written to resemble legitimate messages from known companies such as Facebook, PayPal or Amazon. The victim will be prompted to open the attached file, which may take the form of a Microsoft Word document or PDF file. This file will use a corrupted macro script to download and install threats like the TBHRanso Ransomware onto the victim's computer.
Table of Contents
The TBHRanso Ransomware will Prevent Access to Your Files
It does not seem that the TBHRanso Ransomware is the work of a sophisticated hacker. The TBHRanso Ransomware is a variant of HiddenTear, an open source ransomware engine that is available on the Dark Web freely. Unfortunately, HiddenTear variants carry out an effective ransomware attack, encrypting the victim's files and then demanding a ransom payment. The TBHRanso Ransomware, in its attack, will target the user-generated files, which can include music, videos, and numerous document types. The TBHRanso Ransomware will mark the files encrypted by the attack by changing their file extension to '.locked,' which is added to the end of each affected file's name. Once the TBHRanso Ransomware finishes encrypting a file, it will no longer be readable and will appear as a blank icon on the Windows Explorer. Some of the file types that are targeted in attacks like the TBHRanso Ransomware include:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
Dealing with a TBHRanso Ransomware Infection
After the TBHRanso Ransomware encrypts the victim's files, it delivers a ransom note, which demands payment from the victim. This ransom note is contained in a text file named 'READ_IT.txt' that is dropped on the infected computer's desktop. The TBHRanso Ransomware ransom note is opened by the victim's default text editor (usually a Microsoft's Notepad application), and contains the following text:
'This computer has been hacked
Your personal files have been encrypted. Send me 100$ BTC to (1MMphN2Rc5xCf4TGTVXQ6B8VSbYdQyCgYS) to get decryption passcode. After that, SEND ME YOUR (PC NAME) TO TBHRanso@protonmail.com, you'll be able to see your beloved files again.
With love… TBHRanso Virus :')'
It is clear from the ransom note and its delivery method, that the people responsible for the TBHRanso Ransomware are not particularly sophisticated. This makes it unlikely that the cybercrooks are equipped to help computer users restore their files after the victim pays the ransom or contacts them via email. Establishing contact with these people is highly unsafe. Instead, take preemptive steps to make sure that your data is safe. The best way to deal with these attacks is to restore the files from a backup copy contained on the cloud or an external device.
SpyHunter Detects & Remove TBHRanso Ransomware
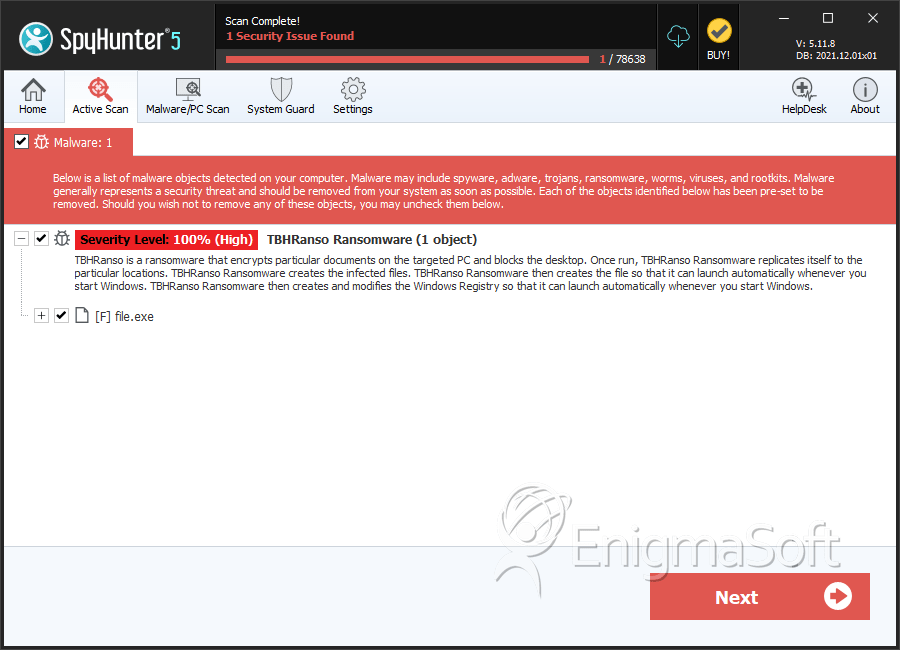
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | b74da335200715a823550470ecca768c | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.