Taurus Stealer
 Taurus Stealer is the name of a new infosteal that has been offered as a commodity online since April 2020. The authors of the Taurus Stealer appear to be offering this threat for $100, which makes the threat very accessible as the price is not set too high. According to cybersecurity experts, the Taurus Stealer creators are the same ones behind the 'Predator the Thief' threat. The Taurus Stealer is rather threatening not only because of its relatively low price but also because it is a fairly feature-rich threat. Recently, the Taurus Stealer has been distributed via phishing email campaigns such as the 'Google Pay' Email Virus.
Taurus Stealer is the name of a new infosteal that has been offered as a commodity online since April 2020. The authors of the Taurus Stealer appear to be offering this threat for $100, which makes the threat very accessible as the price is not set too high. According to cybersecurity experts, the Taurus Stealer creators are the same ones behind the 'Predator the Thief' threat. The Taurus Stealer is rather threatening not only because of its relatively low price but also because it is a fairly feature-rich threat. Recently, the Taurus Stealer has been distributed via phishing email campaigns such as the 'Google Pay' Email Virus.
The phishing campaigns utilized by the cybercriminals to spread Taurus don't deviate from current trends. The emails resemble advertisements or documents containing potentially important information. For example, an email in such a campaign could pose as a warning for a due charge or some kind of payment. Regardless of the subject, these emails contain malicious attachments. In Taurus' case, the attachments are Word documents. If a target tries to open the document, they are asked to enable macros. If macros are enabled, the malicious code in the document will download three files and store them in the %Temp% folder. After that Taurus uses PowerShell script to decode the payload.
Taurus Stealer employs multiple techniques to avoid sandbox observation. Taurus uses the GetTickCount function to make sure it's not in a sandbox that is patching the sleep function. Taurus also uses the Ping function to see if there is an active internet connection. It also looks for specific files and goes through a number of computer names. If any of the files are found, or if the computer name matches any of the queries, the program is terminated.
The Taurus Stealer does not work in certain countries. The countries on the Taurus Stealer's blacklist all appear to be current or former members of the Commonwealth of Independent States – Ukraine, Belarus, Moldova, Georgia, Armenia, Kazakhstan, Tajikistan, Uzbekistan and others. It is likely that the threat's authors consider these nations allies and prefer to avoid any campaigns targeting users from the aforementioned states.
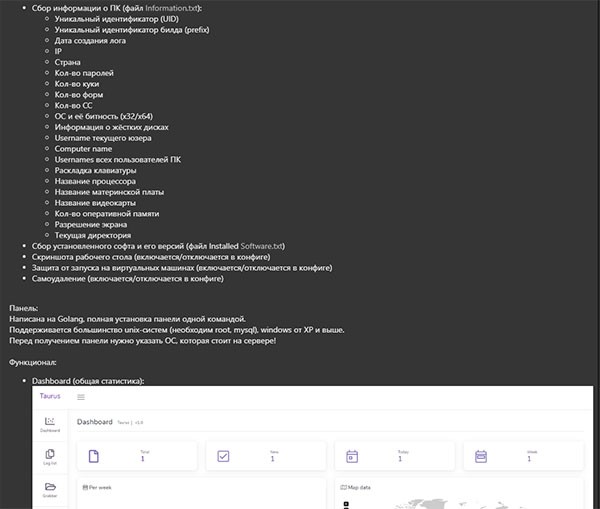
Screenshot 1 of Taurus Stealer Taurus Project Russian website where Taurus malware is sold - Source: twitter.com/3xp0rtblog
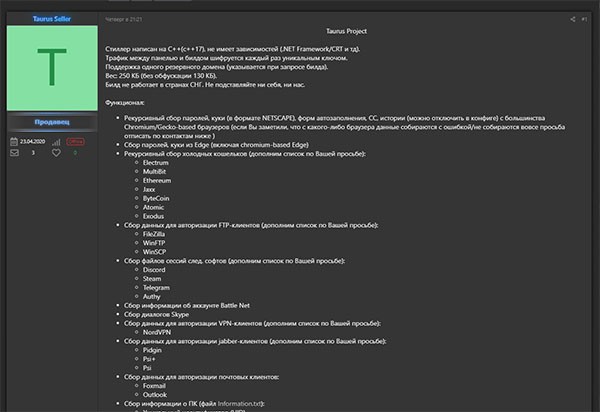
Screenshot 2 of Taurus Stealer Taurus Project Russian website where Taurus malware is sold - Source: twitter.com/3xp0rtblog
>In advertisements promoting the Taurus Stealer, the threat's developers claim that this infostealer can be used to obtain:
- Files associated with well-known cryptocurrency wallet software, including Jaxx, Atomic, Exodus, Electrum, Bytecoin and others.
- Sessions and logs associated with Telegram, Steam and Discord.
- Saved login credentials and cookies from Microsoft Edge and Internet Explorer.
- Login credentials for Microsoft Outlook, Pidgin and Foxmail.
- Skype chat sessions.
- Login credentials for FTP clients (for example, FileZilla).
- Login credentials for NordVPN.
The Taurus Stealer also targets Gecko-based Web browsers, like Mozilla Firefox, and Chromium-based browser such as Google Chrome. This threat is able to collect:
- Autofill information.
- Saved login credentials.
- Cookies.
- Browsing history.
The Taurus Stealer is a threat that can collect a significant amount of information from its targets. To protect your data and your system, it is best to install a genuine, modern anti-virus software suite.

