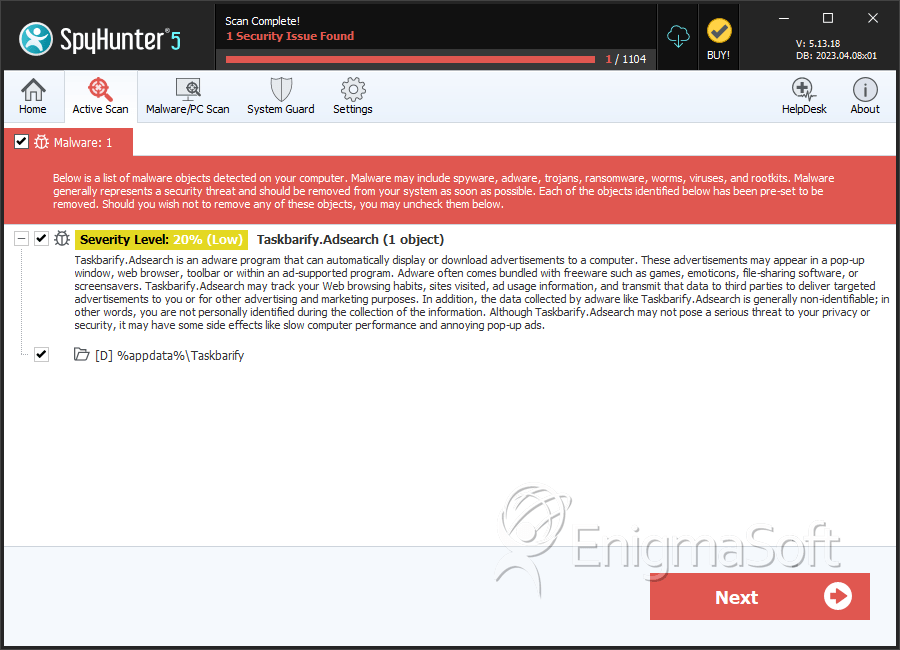
Taskbarify.Adsearch
Taskbarify is a highly intrusive program that disrupts users' browsing experience by injecting unwanted advertisements into the websites they visit and manipulating their browser's homepage and search engine settings. Users should act as soon as possible when they notice any signs that could be attributed to the presence of such undesirable applications that could have managed to sneak their installation on the device.
Table of Contents
Users Should not Trust PUPs (Potentially Unwanted Programs) Like Taskbarify
Once Taskbarify infiltrates users' Mac devices, it takes control of their browser's configuration, forcefully modifying fundamental settings, such as the homepage, new tab page and default search engine preferences. Consequently, when users open the impacted browser, Taskbarify will redirect them and their search queries through untrustworthy and dubious search engines, diminishing the reliability and accuracy of your search results.
In addition to the unauthorized redirects, Taskbarify employs another nefarious tactic to generate and deliver unwanted advertisements. By opening new tabs in the affected browser, Taskbarify could show ads that are unrelated to the website's users are actively browsing. These advertisements often promote questionable software, attempt to deceive visitors with fake software updates, or even lure users into falling victim to tech support or other online tactics.
The primary objective of Taskbarify is to generate revenue for its creators, often at the expense of the user's browsing experience and online privacy. By forcefully injecting advertisements, manipulating browser settings, and promoting fraudulent schemes, Taskbarify seeks to exploit unsuspecting users and profit from their unwitting interactions.
It is crucial to remove Taskbarify from your computer promptly to regain control over your browser settings, protect your online privacy, and safeguard yourself against further unwanted intrusions and potential security risks.
Browser Hijackers and PUPs Often Mask Their Installation via Manipulative Tactics
The distribution of PUPs and browser hijackers involves the implementation of manipulative tactics to deceive users, leading to the installation of these unreliable applications on their devices.
One commonly employed manipulative tactic is software bundling. PUPs and browser hijackers are frequently bundled with legitimate software or applications that users willingly download and install. However, during the installation process, the bundled software is often presented in a confusing or inconspicuous manner, with the user inadvertently agreeing to install the additional unwanted programs along with the desired software.
Deceptive advertising and social engineering techniques are also prevalent in the distribution of PUPs and browser hijackers. Misleading advertisements, often appearing as legitimate system alerts or enticing offers, prompt users to click on them. These deceptive advertisements may falsely claim to provide beneficial services, software updates, or exclusive content, tricking users into taking actions that lead to the installation of unwanted software.
Questionable websites also may play a significant role in manipulating users to install PUPs and browser hijackers. Users may be redirected to these websites through various means, such as misleading links, spam emails or compromised online advertisements. Once on these deceptive websites, users are coerced into engaging with fraudulent content, clicking on misleading download buttons, or providing personal information, ultimately resulting in the installation of unwanted software.
Moreover, PUPs and browser hijackers utilize stealthy installation techniques to avoid detection and removal. They employ obfuscation methods to hide their presence and modify system settings to evade easy uninstallation. These techniques could make it challenging for users to identify and remove unwanted software effectively.
In summary, the distribution of PUPs and browser hijackers involves a range of shady tactics, including software bundling, deceptive advertising, malicious websites, vulnerability exploitation, and stealthy installation techniques. These tactics exploit users' trust, lack of awareness, and vulnerabilities in their devices to deceive and manipulate them into installing unwanted software. It is crucial for PC users to exercise caution, adopt safe browsing practices, and employ reliable security measures to protect against these manipulative distribution tactics.
SpyHunter Detects & Remove Taskbarify.Adsearch
Taskbarify.Adsearch Video
Tip: Turn your sound ON and watch the video in Full Screen mode.
Directories
Taskbarify.Adsearch may create the following directory or directories:
| %appdata%\Taskbarify |

