Symbiom Ransomware
The Symbiom Ransomware is an encryption ransomware Trojan that is used to extort computer users. The Symbiom Ransomware, like other similar ransomware Trojans, will make the victim's files inaccessible by encrypting them with a strong encryption algorithm. The Symbiom Ransomware will then demand the payment of a ransom from the victim in exchange for the decryption key necessary to recover the affected files. The Symbiom Ransomware and similar threats are a real threat to the victims' data, and computer users are urged to take strong precautions.
Table of Contents
Stay Away from the Symbioses Proposed by this Ransomware
The Symbiom Ransomware is based on HiddenTear, an open source ransomware platform. Since its release in August 2015, HiddenTear has spawned countless encryption ransomware variants, most of which are identical to the Symbiom Ransomware. The Symbiom Ransomware has been customized to allow it to evade many anti-virus scanners, as well as affect the latest versions of the Windows operating system. The most common way of distributing the Symbiom Ransomware is via spam email attachments. The email attachments may take the form of Microsoft Word documents with corrupted macro scripts that download and install the Symbiom Ransomware onto the victim's computer system. The Symbiom Ransomware was first observed in the second week of August 2017.
How the Symbiom Ransomware Infection Works
After the Symbiom Ransomware is installed on the victim's computer, it connects to its Command and Control center to report information about the infected computer and the encryption used on the victim's data. The Symbiom Ransomware scans the victim's computer and encrypts data on all local drives, network shared drives, and remote memory devices connected to the infected PC. The Symbiom Ransomware uses a combination of the AES and RSA encryptions to make the victim's files unusable. During its attack, the Symbiom Ransomware also will delete the Shadow Volume Copies on the infected computer. The files encrypted in the Symbiom Ransomware attack can be identified easily because the Symbiom Ransomware will add the string '.symbiom_ransomware_locked' to the end of each affected file's extension. The Symbiom Ransomware will target files generated by the computer user, which include files such as photos, videos, audio, Microsoft Office documents, database, and numerous other file types. The Symbiom Ransomware will encrypt the victim's files but allow the Windows operating system to continue operating normally (so that the victim can view the ransom note and pay the ransom).
The Symbiom Ransomware’s Ransom Demands
The Symbiom Ransomware will demand a ransom payment after encrypting the victim's files. To do this, the Symbiom Ransomware will drop a text file on the victim's desktop. This file is named 'README_Ransomware_Symbiom.txt' and contains the following text:
'Your files have been locked by Symbiom!
Send 0.1 bitcoin (It is about 250 dollars) to : 13NjrGWP8GBRSWCgNBPYpPsGUfbyiYGnDc
Afterwards, send your bitcoin address which you payed with to : hackerz6924@tutanota.com
Don't worry. I will save your files if you pay.
GOOD LUCK!'
The ransom payment is equivalent to approximately 430 USD at the current exchange rate. Computer users should avoid paying the Symbiom Ransomware ransom or following the instructions in the Symbiom Ransomware ransom note. It is possible that the people responsible for the Symbiom Ransomware attack will not keep their word and restore the affected files. They are just as likely to ignore the ransom payment or demand more money. Paying the Symbiom Ransomware ransom also allows con artists to create more ransomware Trojans and make a living from this tactic.
Dealing with the Symbiom Ransomware
Instead of paying the Symbiom Ransomware ransom, computer users should restore their files from a backup. Backup copies of your files combined with a trusted security program and a good anti-spam filter can prevent the Symbiom Ransomware from entering your computer and are the best protection against the Symbiom Ransomware and other ransomware Trojans.
SpyHunter Detects & Remove Symbiom Ransomware
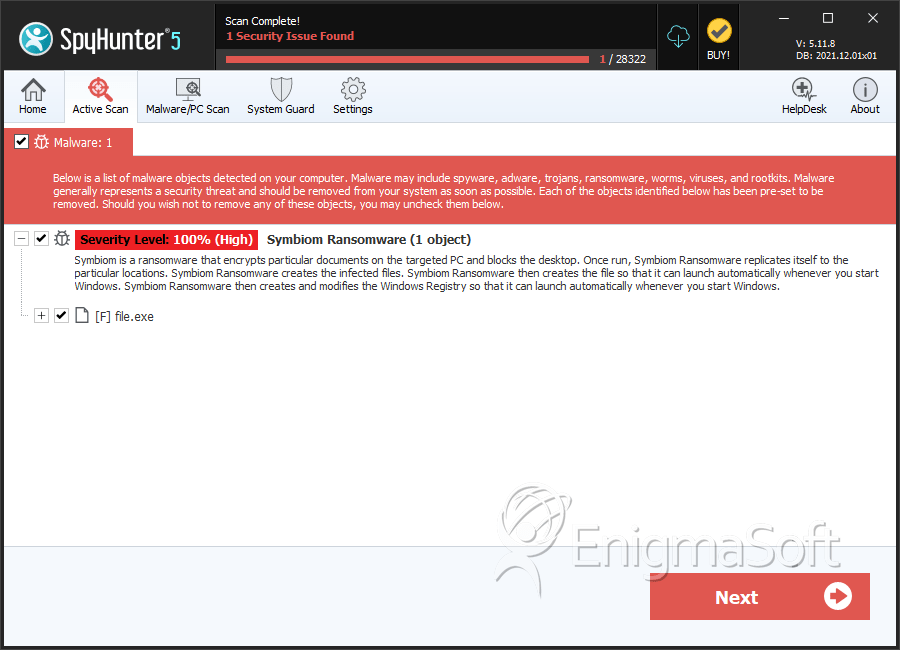
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 89ef6b98c7e352d6b23573bd6d008298 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.