Suri Ransomware
The Suri Ransomware is an encryption ransomware Trojan that was first observed on September 9, 2018. The Suri Ransomware is one of the many variants of HiddenTear, an open source ransomware engine that has released countless ransomware variants since it was first released in 2015. The Suri Ransomware is capable of carrying out an effective encryption ransomware attack, and it is important that computer users take precautions against the Suri Ransomware and similar threats.
Table of Contents
Why You Should Avoid Been Infected by the Suri Ransomware
The Suri Ransomware uses the AES encryption to make the victim's files inaccessible. The Suri Ransomware targets the user-generated files in its attack, which may include files with the following file extensions:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
The Suri Ransomware marks each file it encrypts by adding the file extension '.SLAV' to the end of the file's name. The Suri Ransomware takes the files hostage, therefore making it inaccessible to the computer user.
The Suri Ransomware’s Ransom Note
The Suri Ransomware delivers a ransom note after the files' encryption is finished. This ransom message is displayed on the infected computer's desktop as a wallpaper image and in a system dialog window titled ':( Suri.' The original text in Italian of this ransom note and a translation into English reads:
'O no, tutti i tuoi file personali sono stati cryptati 🙁
Come faccio a decryptarli?
Ciao utente, tutti i tuoi file personali sono stati cryptati.Non si torna più indietro ormai. Tgliendomi condannerai tutti i tuoi file. Tutti i tuoi file personali verrano decryptati e io mi auto elimino. Semplice! Invia una somma di 100 Euro in bitcoin all'indirizzo sottostante io chiave pubblica. Riavviando o altro non risolvi nulla.
Ora forse ti chiederai come fare. Perché ?
Solo io sono in grado di decryptare tutti tuoi file e solo io ho la Dopo aver pagati che succede ?
Tutti i tuoi file personali verrano decryptati e io mi auto alimio'
'Oh no, all your personal files have been encrypted 🙁
How can I decrypt them?
Hello user, all your personal files have been encrypted. Can't go back now. You will give all your files to me. All your personal files will be decrypted, and I will delete them. Simple! Send a sum of 100 euros in bitcoins to the address below and public key. Restarting or else will not solve anything.
Now maybe you'll wonder how to do it. Why?
Only I can decrypt all your files, and only I have the key. After paying what happens?
All your personal files will be decrypted, and I will give them back.'
Computer users must avoid paying the Suri Ransomware ransom and instead restore the affected files from a backup copy.
SpyHunter Detects & Remove Suri Ransomware
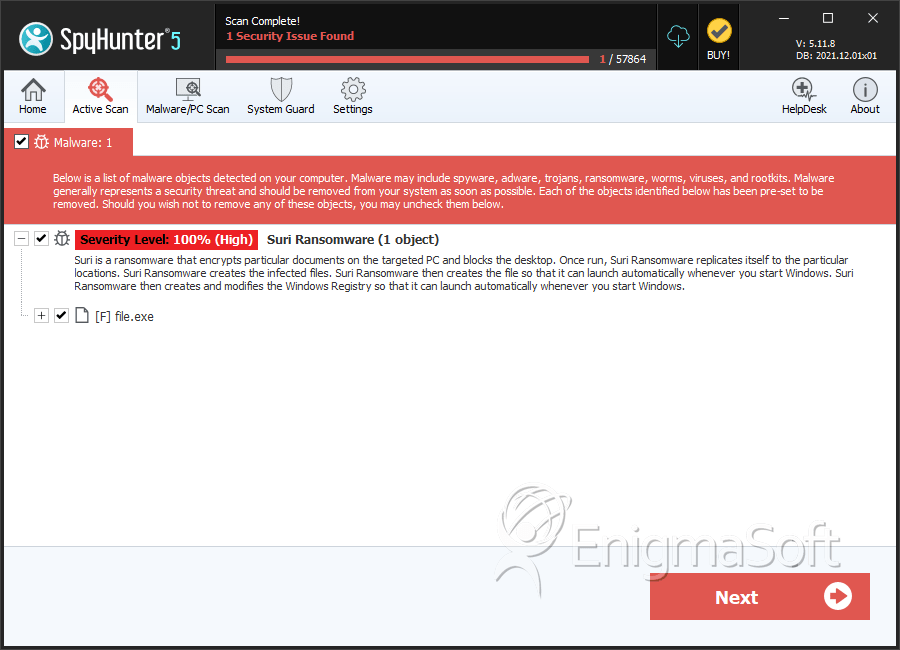
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 5bf9fb1ef36737d7941c88fda7fde41a | 0 |
| 2. | file.exe | 0e6d4bcf3233fc0061cba706255cb752 | 0 |

